As the backbone of modern energy systems, smart grids and digital substations promise efficiency and sustainability—but they also open the door to escalating cyberthreats. This article dives into a layered cybersecurity strategy that blends integrated vulnerability assessments, robust protocols, and defense-in-depth tactics. Packed with practical insights and a look at breakthrough technologies, it empowers utilities to protect critical infrastructure and build a more secure, resilient energy future.
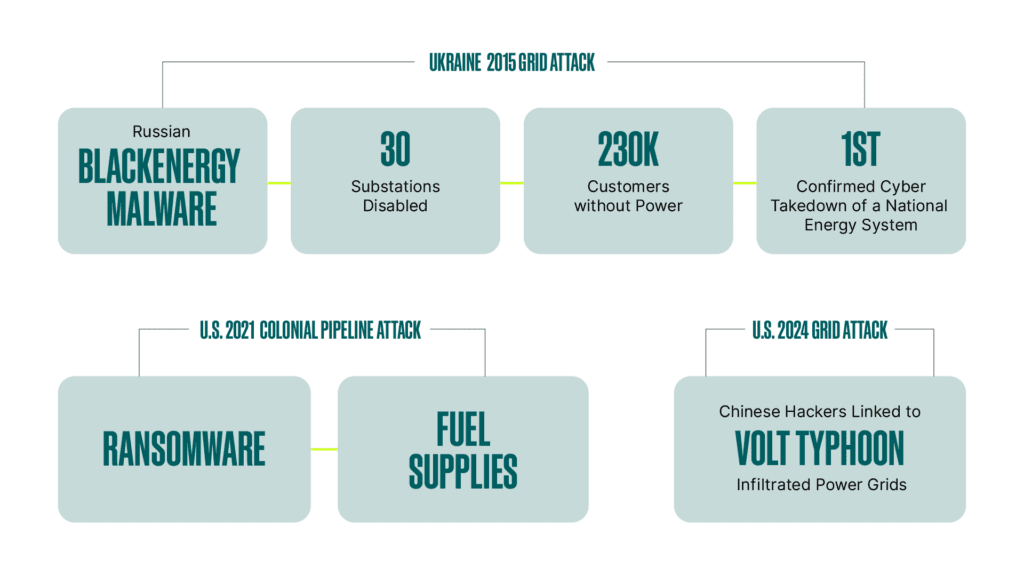
Smart grids and substations are transforming the energy sector, delivering efficient, reliable, and sustainable electricity through advanced energy management systems. Yet, their digital interconnectivity makes them prime targets for cyberattacks (Figure 1) that can disrupt services and destabilize economies. With utility cyberattacks surging 70% in 2024, driven by espionage, profit, or geopolitics, these assaults threaten essential services and public confidence.

Cybersecurity Threats and Vulnerabilities
Smart grids and substations are increasingly vulnerable to sophisticated cyberthreats due to their reliance on digital technologies and interconnected systems. The complexity and scale of these systems amplify their attack surface, making comprehensive security (see sidebar “Definitions”) a formidable challenge.
DefinitionsWhat Is a Smart Grid? Smart grids, enabling two-way communication between energy sources and end-users like homes and businesses, optimize operations through advanced energy management systems, supporting distributed energy resources (DERs) such as solar panels. What Is Cybersecurity? Cybersecurity protects digital systems, networks, devices, and data from unauthorized access, cyberattacks, or damage. It encompasses technologies, processes, and policies designed to ensure information and systems’ confidentiality, integrity, and availability. |
The dispersed nature of smart grids, with thousands of interconnected devices like smart meters, sensors, and distributed energy resources (DERs), creates a vast attack surface. For substations, many operate legacy systems (such as supervisory control and data acquisition [SCADA] systems), which are essential for monitoring and control, and are prime targets. Figure 2 summarizes the primary attack vectors, specific vulnerabilities, and their potential impacts on grid reliability and societal stability.

In addition to the challenges noted above, specific vulnerabilities challenge the cybersecurity protection of energy infrastructure, such as:
- Smart Grid Vulnerabilities. The dispersed nature of smart grids, with thousands of interconnected devices, creates a vast attack surface. These devices often lack robust security features, making them entry points for attackers. Additionally, two-way communication in smart grids increases the risk of data interception or manipulation, which can lead to mismanagement or poor decision-making.
- Substation Vulnerabilities. Many substations operate legacy systems not designed with modern cybersecurity and lack encryption or authentication mechanisms. SCADA systems are prime targets. A compromised SCADA can feed incorrect data and destabilize the grid. Communication networks within substations are also vulnerable to interception, where altered data transmissions can disrupt operations or enable espionage (Figure 3).
- Integration Challenges. Integrating legacy systems with modern technologies in energy infrastructure creates security gaps. For example, connecting older substation equipment to cloud-based platforms can expose vulnerabilities that attackers exploit to gain network access.

The consequences are severe. Outages disrupt economic productivity, halt services like healthcare, and erode public trust. Data breaches lead to mismanagement, financial losses, and regulatory penalties, undermining demand response programs. Addressing these challenges requires a proactive, multi-layered cybersecurity strategy.
Defense-in-Depth Cybersecurity Strategies
The defense-in-depth approach is a comprehensive cybersecurity strategy that benefits from multiple layers of cybersecurity protection, incorporating the principles of redundancy, diversity, and compartmentalization. Each layer of defense (Figure 4) serves a unique purpose in protecting against various cyber threats, ensuring that if one cybersecurity layer is compromised, the other cybersecurity layers remain active to provide protection.

Layering refers to utilizing multiple cybersecurity protection mechanisms to address different cyberthreat types. By layering cybersecurity defenses, the substation cybersecurity team can reduce the risk that a single point of failure could compromise the entire substation. The operational technology (OT) security layer enhances resilience for OT systems, which manage essential grid operations.
Redundancy ensures backup cybersecurity controls are in place to protect critical functions (such as two is one, and one is none). Compartmentalization divides the network into isolated segments, ensuring that a cyber breach in one area does not easily spread to other areas, thus limiting the scope and impact of a cyberattack. The six strategic layers of a multi-layered defense-in-depth cybersecurity framework are listed in Figure 5. Each addresses a specific aspect of protection for smart grids and substations. The table defines the overarching structure and high-level best practices to counter vulnerabilities and ensure resilience.

Compliance with standards like North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP), International Electrotechnical Commission (IEC) 62443, and Network and Information Systems Directive 2 (NIS2) is not only a legal requirement, but also a cornerstone of robust cybersecurity. These frameworks mandate rigorous security practices, ensuring utilities avoid penalties and maintain operational integrity.
Implementing Robust Cybersecurity Practices
Implementing robust cybersecurity measures for smart grids and substations requires a strategic approach integrating best practices, leveraging advanced tools, and fostering a security culture. The following key practices, summarized in Figure 6, address the complex threat landscape and enhance energy infrastructure resilience.

These operational tactics complement the defense-in-depth layers, leveraging advanced tools and fostering a security culture. A real-world example, the Dubai Electricity and Water Authority (DEWA), illustrates their application (see sidebar “Applying Best Practices”).
Applying Best PracticesDubai Electricity and Water Authority (DEWA) is a government-owned utility that provides electricity and water services in the Emirate of Dubai. The company generates electricity primarily from gas and steam turbines, and solar photovoltaic plants, which are expected to reach 5 GW installed capacity by 2030. DEWA also manages the transmission and distribution (T&D) across Dubai, operating multiple power stations, desalination plants, and extensive transmission networks. GE Vernova’s analysis of DEWA’s cyber protection resulted in a customized solution based on IEC 62443 and GE Vernova best practices to reduce the attack surface and eliminate the risk of unauthorized access and operational issues, among other recommendations. The tools employed include virtualization, central access control (active directory), role-based access control, application whitelisting, zone-based segmented network design, Nozomi intrusion detection solution, deep packet inspection on multimedia messaging service (DPI on MMS), and device logging and central system log (syslog) server. The solution significantly improved DEWA’s security posture and internal security procedures. |
Future Trends in Cybersecurity
Emerging technologies will strengthen smart grid and substation cybersecurity. Artificial intelligence (AI) and machine learning enable real-time threat detection by analyzing network anomalies, reducing response times. Utilities must integrate these innovations (Figure 7) with existing defenses, adopting scalable solutions to stay ahead of evolving cyber threats and ensure long-term grid resilience.

Securing smart grids and substations is essential to sustaining reliable and sustainable energy infrastructure. A multi-layered cybersecurity approach—integrating vulnerability assessments, secure protocols, and defense-in-depth strategies—counteracts diverse threats.
Utilities must adopt comprehensive frameworks, invest in emerging technologies like AI and blockchain, and join industry consortia, partnering with regulators and academia to address evolving risks. By budgeting for workforce training, prioritizing cybersecurity, and continuously updating defenses, utilities can protect essential assets, ensure grid stability, and safeguard communities. The time to act is now—every step toward stronger cybersecurity builds a resilient energy future for all.
—John (JB) Bedrick is senior global cybersecurity product line leader with GE Vernova. For more on this topic, the following full-length white papers are available: Enhancing Cyber Resilience in Substations and Securing Smart Grids – Strategies & Best Practices.



