Key Takeaways:
- FileFix builds on ClickFix to trick users into executing hidden commands via the Windows clipboard.
- Attackers are already testing this method in the wild, signaling active threat development.
- Defense requires user awareness and technical controls to detect clipboard-based exploits.
Cybersecurity researchers have identified a new social engineering attack that builds on the previously known ClickFix technique. According to Check Point, attackers are already conducting dry runs of the new FileFix method to test malware delivery tactics in the wild.
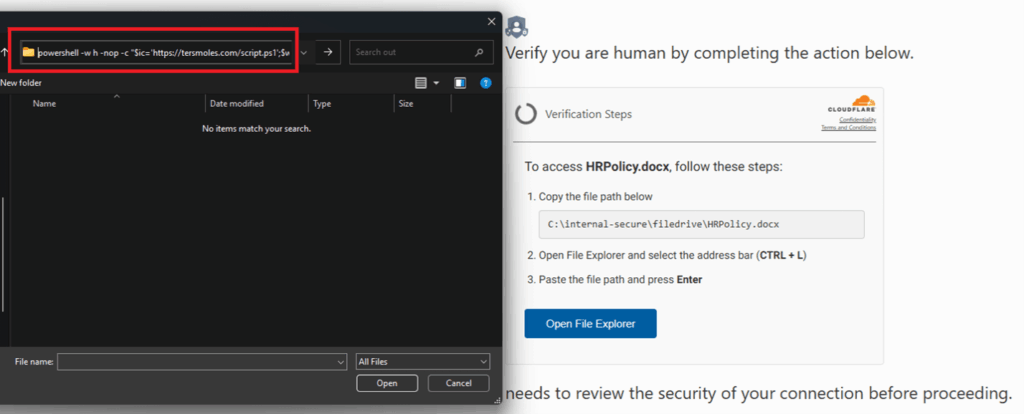
The FileFix attack manipulates users into running malicious commands by exploiting familiar Windows behavior. When a user visits a compromised website, it automatically opens a legitimate File Explorer window and places a hidden PowerShell command onto the clipboard. The user is then tricked into pasting this content into the Explorer address bar, which causes the command to execute. This method cleverly avoids traditional malware detection by relying entirely on built-in system tools and user interaction.
According to Check Point researchers, cybercriminals have already begun experimenting with the FileFix technique in real-world scenarios. This activity is a strong indicator that attackers are preparing to replace these benign tests with actual malware soon.
“The rapid rise of the ClickFix technique in 2025 highlights that social engineering remains one of the most cost-effective and enduring methods cyber criminals use to breach defenses,” the researchers explained. “The fact that FileFix is already being tested and used in the wild mere days after its public disclosure shows how quickly attackers adopt new techniques and adapt to the evolving cyber threat landscape.”

How to protect your organization against the FileFix attack?
To protect against FileFix attacks, organizations and individuals should focus on both technical defenses and user awareness. It’s advised to educate users about the risks of pasting unknown content into the File Explorer address bar. Security teams should monitor clipboard activity and command execution patterns for suspicious behavior, particularly involving PowerShell.
It’s highly recommended to implement endpoint protection tools that can detect and block clipboard-based attacks, and unusual use of system utilities is also important. Finally, consider restricting clipboard access in browsers or using browser extensions that warn users when potentially dangerous content is copied automatically.
Lastly, users should be encouraged to double-check any unexpected or unusual requests with their IT or security teams before taking action. They should also treat any website or email that asks them to perform unfamiliar tasks with suspicion.



