Cybersecurity researchers at GreyNoise have uncovered a significant pattern that could revolutionize how organizations prepare for emerging threats.
Their analysis reveals that spikes in malicious attacker activity consistently precede the disclosure of new vulnerabilities, providing defenders with a critical early warning window of up to six weeks.
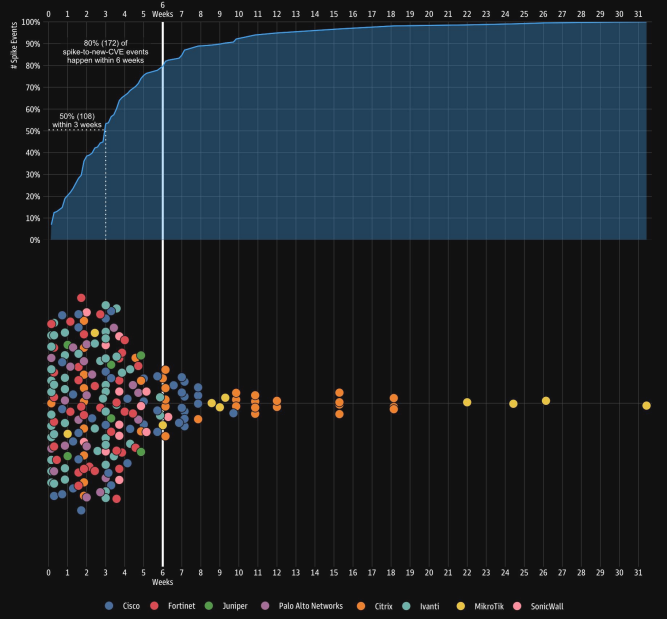
The comprehensive study analyzed 216 statistically significant spikes in attacker activity across enterprise edge technologies, finding that 80 percent of these surges were followed by new Common Vulnerabilities and Exposures (CVE) disclosures within six weeks.
Perhaps most remarkably, 50 percent of spikes preceded new CVE announcements within just three weeks, offering defenders an unprecedented opportunity for proactive security measures.
Enterprise Edge Infrastructure Under Systematic Reconnaissance
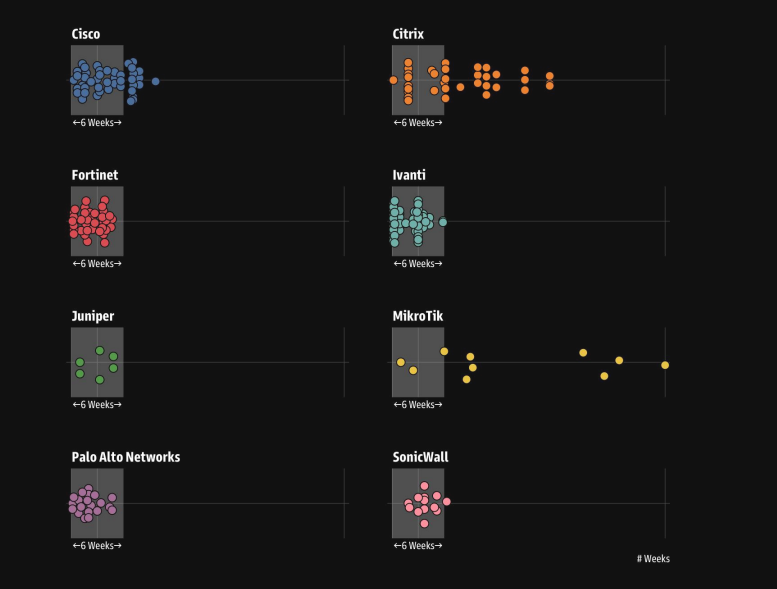
The research focused exclusively on internet-facing enterprise assets, including VPNs, firewalls, and products from major vendors such as Cisco, Fortinet, Citrix, and Ivanti.
This pattern emerged organically from the data, despite researchers not initially limiting their analysis to enterprise technologies.
Most concerning for security teams, the majority of spike activity involved actual exploit attempts against previously known vulnerabilities rather than generic scanning.
This suggests threat actors are conducting sophisticated reconnaissance operations, either testing attack vectors that may lead to new vulnerability discoveries or systematically inventorying exposed systems for future exploitation.
The study revealed particularly striking patterns for specific vendors. Ivanti demonstrated exceptionally tight correlations between activity spikes and subsequent CVE disclosures, while Fortinet showed rapid succession patterns where new vulnerabilities emerged within days of observed spikes.

However, the reliability varies by vendor, with MikroTik showing inconsistent patterns that make it less suitable for predictive defense strategies.
Exploiting Legacy Flaws to Map Future Targets
A disturbing trend emerged showing attackers leveraging remarkably old vulnerabilities during their reconnaissance campaigns.
Researchers observed significant activity spikes targeting 14-year-old Cisco CVE-2011-3315 and eight-year-old PAN-OS CVE-2017-15944, just before new vulnerabilities affecting the same technologies were disclosed.
This behavior suggests multiple strategic purposes: creating target confusion through broad activity across various products, pre-positioning through system inventorying using older exploits, and potentially discovering zero-day vulnerabilities through systematic probing.
The implications extend beyond corporate security, as state-sponsored groups have repeatedly targeted enterprise edge infrastructure for pre-positioning and surveillance activities.
GreyNoise recommends that defenders use this six-week window to block reconnaissance IP addresses, preventing systems from being catalogued in attacker inventories before new exploits emerge.
This research challenges conventional reactive security models by demonstrating that attacker behavior often precedes rather than follows vulnerability disclosures, potentially transforming threat intelligence into a proactive defense capability.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates


