

Craig is a former software developer and red teamer. He has been pentesting at Black Hills Infosec since 2018.
Read more of this series here:
Part 1 – Burpference
Part 2 – Copilot
In my journey to explore how I can use artificial intelligence to assist in penetration testing, I experimented with a security-focused chat bot created by Jason Haddix called Arcanum Cyber Security Bot (available on https://chatgpt.com/gpts). Jason engineered this bot to leverage up-to-date technical information related to application security and penetration testing. One of the example prompts is to supply the chatbot with JavaScript source and have it analyze the code from a security perspective.
As with previous blogs in this series, I used OWASP’s intentionally vulnerable Juice Shop web application for this experimentation. Again, it is important to consider client confidentiality when performing penetration tests. So, take care not to send customer information to remote LLMs, and use local on-premises models instead for real penetration tests. At first, I tried to paste Juice Shop’s entire main.js file into the Arcanum chat bot’s prompt form. This resulted in a response indicating that the prompt was too large. I used parallel-prettier to make the file more readable so I could break it up and submit it to the chatbot in chunks.
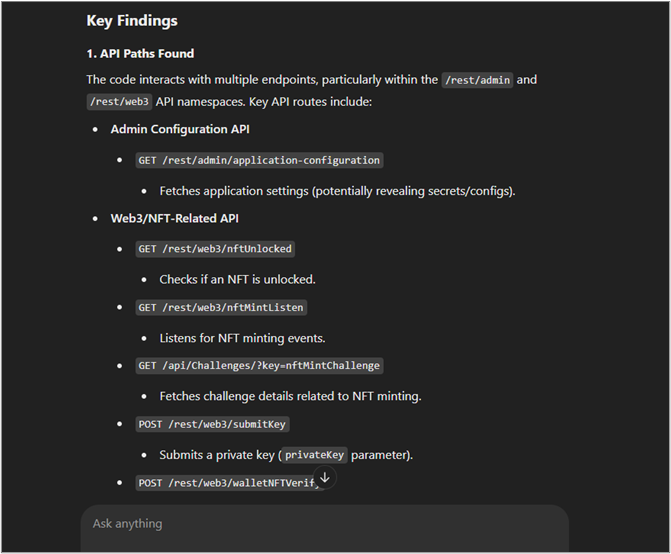
The chatbot returned a list of API endpoints it discovered in the source code. It’s always a good idea to look for additional attack surface in JavaScript files, so it was really helpful for the chatbot to pull those out of the source code. It even attempted to provide some documentation for the API calls!
The chatbot continued with its security analysis of the file. Interestingly, it identified hacking tutorial content in the source code and deduced that the code was part of an intentionally vulnerable web application, even calling out the application I was using by name.
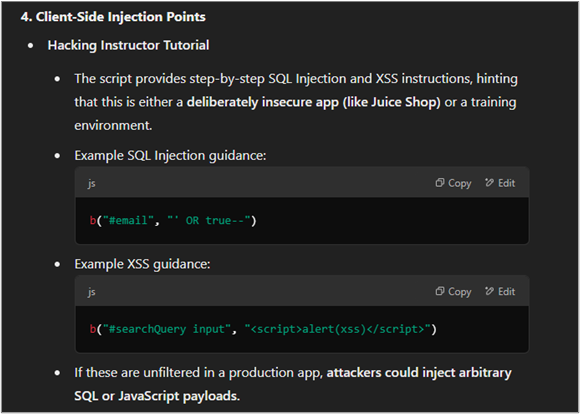
The response continued with ideas for possible attack paths.
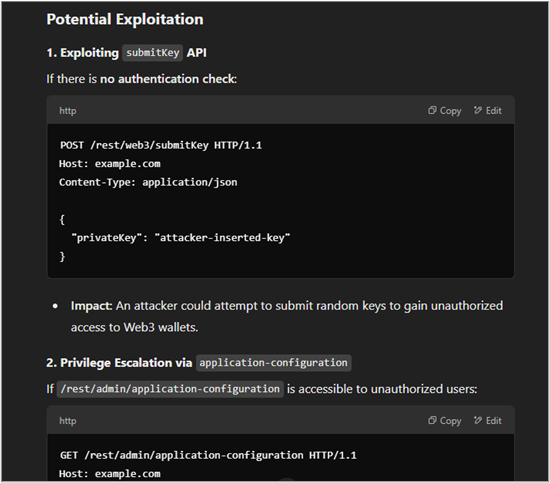
The chatbot response concluded with defensive recommendations and an overall summary of its findings. At this point, I’m already impressed. The speed at which the chatbot extracted API endpoints from the source code alone is a huge value in terms of time savings. But wait! There’s more! The bot asked if I wanted to provide proof-of-concept exploits for the potential vulnerabilities it identified. I told it “yes,” and it provided the PoCs.
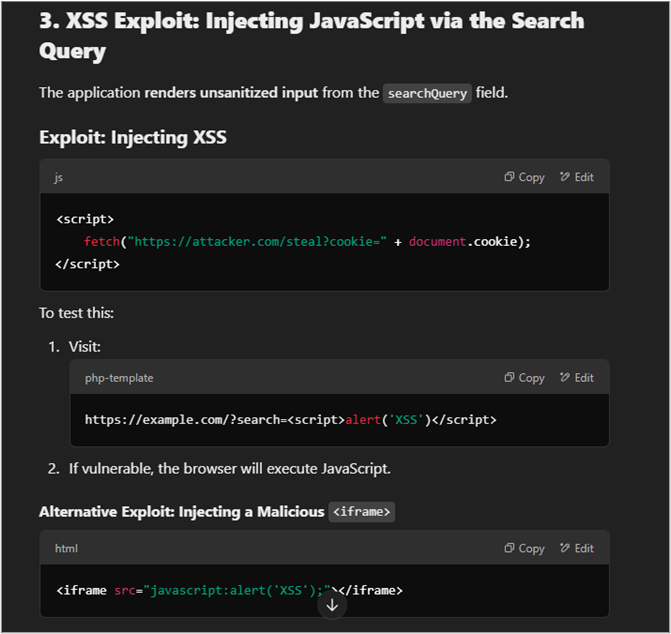
Again, this is where I would likely depart the AI and begin trying to exploit these things, but the chatbot was offering me more, and I wanted to see what else it had.
The chatbot next walked me through how to use Intruder to perform attacks against the different reported vulnerabilities, and it provided various payloads for each attack.
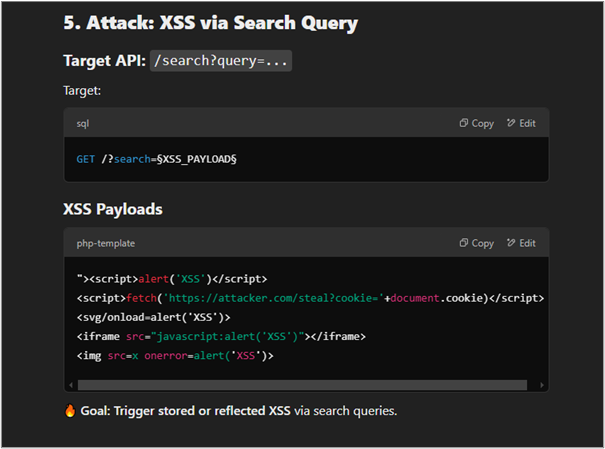
The chatbot proceeded by providing Python code to automate the attacks it had just described.
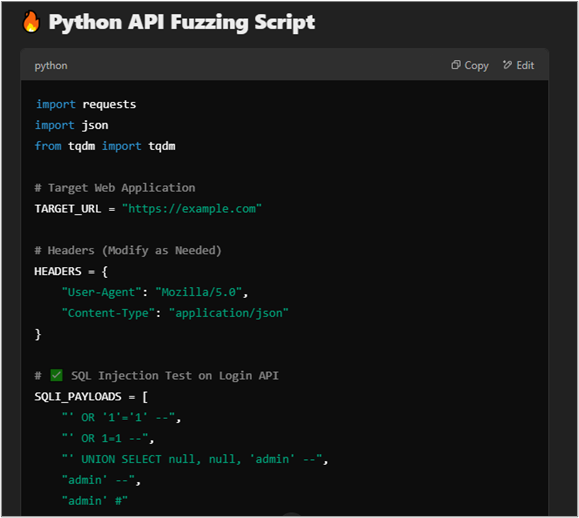
Next, the chatbot offered up ideas about other more advanced vulnerabilities that I might check for in the context of its analysis, and provided payloads and automation for those vulnerabilities.
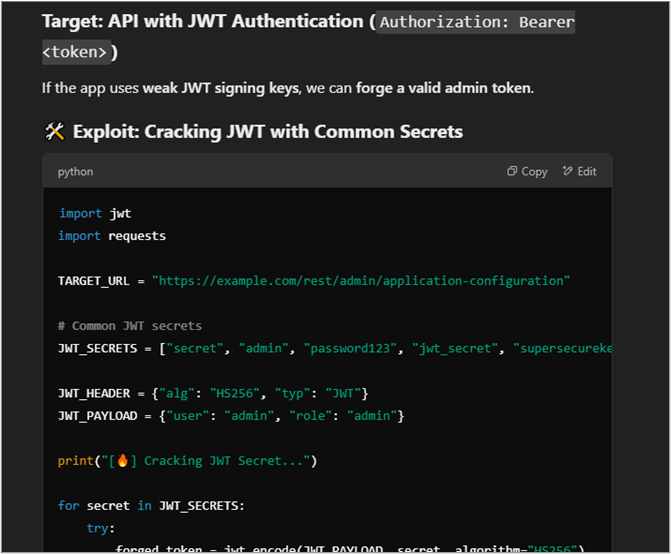
Eventually, the AI got a little off track and began offering up information on other unrelated offensive security topics such as post exploitation and cloud attacks. Overall, I found the Arcanum Cyber Security Bot to be helpful and easy to use.
Summary
“The article demonstrates practical applications of AI in security testing, showing both benefits (time savings, automated analysis) and limitations (context awareness, ethical restrictions) of current AI tools in penetration testing workflows.” – Copilot, when I asked it to summarize the blog posts in this series.
I like to think the AI generated summary is accurate. There are definitely opportunities for us to leverage AI to improve efficiency and performance in our work as penetration testers. There are also pitfalls to avoid like getting so bogged down fiddling with the AI that it becomes a hindrance to the work you’re actually trying to accomplish. Ensuring the confidentiality of client data is another concern that requires careful consideration if you choose to leverage AI in your methodology. Ultimately, I am excited to explore more ways to use AI to improve my work, and I hope this series has been helpful to anyone interested in using AI this way.
Ready to learn more?
Level up your skills with affordable classes from Antisyphon!
Pay-Forward-What-You-Can Training
Available live/virtual and on-demand





