Key Takeaways:
- Nearly half of organizations lack sufficient visibility into their software supply chains, increasing breach risk.
- AI-driven threats and third-party software dependencies are expanding the attack surface.
- Executive concern is rising, but a disconnect remains between leadership awareness and IT preparedness.
Organizations are struggling with poor visibility into their software supply chains, even as 40% of CEOs rank it as their top cybersecurity concern. A new report from LevelBlue exposes how this lack of transparency, combined with escalating AI-driven threats and uneven global preparedness, is putting critical systems at serious risk.
LevelBlue surveyed 1,500 respondents across four global regions, including North America, Europe, Latin America, and Asia-Pacific, to assess their perspectives, preparedness, and investment strategies related to software supply chain security. The report shows that only 23 of the organizations report having “very high” visibility into their software supply chain.
However, 49% of respondents lack the visibility required for security teams to fully identify or understand cybersecurity risks. Organizations with high visibility into their software supply chain are dramatically less likely to suffer breaches (6%) compared to those with low visibility (80%).
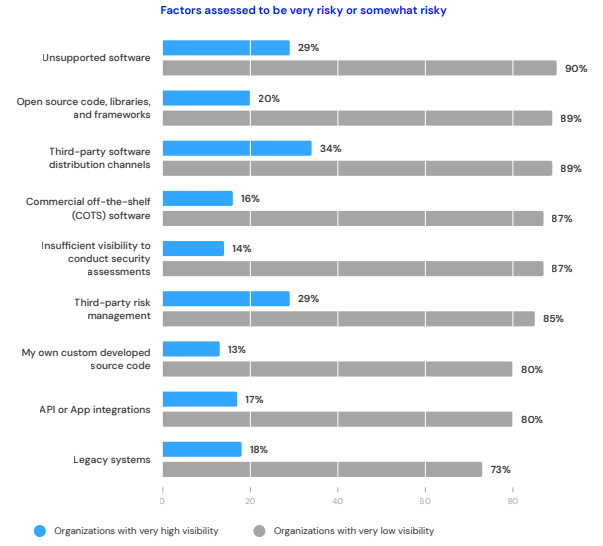
Why does low visibility equal higher breach risk?
Additionally, most of the organizations that lack strong visibility into their supply chain tend to perceive critical factors such as commercial off-the-shelf software, custom code, and API integrations as high-risk. LevelBlue emphasized that the findings of the study show an urgent need for organizations to strengthen their software supply chain defenses.
“In an era of increasing AI disruption and evolving threats from nation-states and cyber criminal groups, the ability to withstand and recover from cyber attacks is directly tied to a clear understanding of an organisation’s software ecosystem,” said Theresa Lanowitz, Chief Evangelist at LevelBlue.

The rapid adoption of AI tools and growing reliance on third-party software have increased the attack surface, which makes it harder to secure the software supply chain. Interestingly, CEOs are more concerned about these risks than CIOs and CTOs, which suggests a disconnect between executive-level awareness and IT operational focus.
Global readiness varies—Europe leads in proactive measures
The study also found that 57% of North American organizations feel prepared for a software supply chain attack. However, only 44% in APAC, 51% in Europe, and 50% in Latin America say the same, despite similar levels of visibility.
LevelBlue’s research shows that European organizations are taking a more proactive stance on software supply chain security. With 67% of enterprises in the region investing in enhanced capabilities, Europe is leading the way in recognizing the importance of long-term resilience and allocating resources accordingly.
Four key steps to strengthen supply chain security
The LevelBlue report outlines four key recommendations for IT leaders to strengthen software supply chain security:
- Leverage executive awareness
IT leaders should use the growing concern among C-suite leaders about software supply chain risks to advocate for increased cybersecurity funding. They must highlight specific threats and align security initiatives with business priorities to gain executive support.
- Identify and prioritize vulnerabilities
It’s recommended to collaborate across departments to pinpoint the most critical weaknesses in the software supply chain. This approach helps set short-term goals for improving visibility and reducing risk exposure.
- Invest in proactive cybersecurity measures
Organizations must adopt advanced tools for threat detection, incident response, and vulnerability management. These technologies are important to stay ahead of evolving threats and to build long-term resilience.
- Assess and monitor supplier security
IT leaders are advised to regularly evaluate the cybersecurity credentials of software suppliers. They must request evidence of their security practices and conduct ongoing assessments to ensure that their supply chain remains secure.




