Cybersecurity threats are growing more complex, and domain-based attacks are at the center of this shift. CSC’s CISO Outlook 2025 report, based on a survey of 300 security leaders, reveals a rising sense of urgency as organizations confront both established and emerging threats.

70 percent of respondents expect an increase in cyber threats in 2025, and 98 percent believe risks will continue rising over the next three years. Domain-related threats, such as cybersquatting, DNS hijacking, and subdomain takeovers, are now among the top concerns.
Domain threats are growing and hard to stop
“DNS and domain-related infrastructure are soft targets for cybercriminals, who use specific threat vectors like DNS hijacking or domain spoofing to exploit exposed systems,” said Ihab Shraim, CTO of CSC’s Digital Brand Services. “We’re already seeing high volumes of these attacks, and we expect them to grow drastically in 2025, as more off-the-shelf tools and attack kits become widely available.”
Many of these threats are now powered by AI. Nearly 90 percent of respondents said DGAs (domain generation algorithms) powered by AI pose a threat. These can be used to create endless combinations of fake domains for phishing, counterfeiting, or fraud.
“There are various platforms built with AI that enable bad actors to launch targeted campaigns against specific verticals, such as financial services,” Shraim said. “These kits are designed to be comprehensive, making attacks more convincing. The misspellings and poor grammar we used to see are largely gone, as AI can produce highly accurate, polished messaging.”
Meanwhile, traditional threats have not gone away. Ransomware, DDoS attacks, and social engineering continue to pressure CISOs and security teams. “What we’re seeing is that attacks such as ransomware don’t happen in isolation, and that bad actors can then go on to steal information in hybrid or blended attacks, which could turn out to be truly devastating,” said CSC CISO Mark Eggleston.
Security is falling behind, and budgets are tight
One challenge is that many organizations still do not view domain and DNS protection as part of core cybersecurity. “Many companies still look at domain names as purely a trademark budget line and this thinking needs to shift towards security,” said Nina Hrichak, VP of EMEA Account Management at CSC. She added, “In companies where CISOs lack visibility of how digital assets are managed, and where responsibility sits with someone with less focus on security, critical, cost-effective measures such as registry locks can get overlooked.”
Despite the growing risk, only 7 percent of respondents said they are “very confident” in their company’s ability to mitigate domain attacks. Most rely on a patchwork of in-house tools and limited outsourcing. Nearly all, or 99 percent, are concerned that their registrars are not following Know Your Customer (KYC) protocols, potentially exposing them to fraud.
The use of AI is also raising internal risks. One major concern is shadow AI, the unsanctioned use of generative AI tools like ChatGPT by employees or vendors. These tools can lead to the unintentional sharing of sensitive company or customer information.
“The answer to the problem of shadow AI,” said Eggleston, “is to use software agents that track all the LLMs used across an organization. It means we can see who is uploading and downloading information from AI tools, and we can block the ones that are too risky. You then apply a zero trust framework, validating users and enforcing control, to ensure everyone is following the organization’s AI governance policy.”
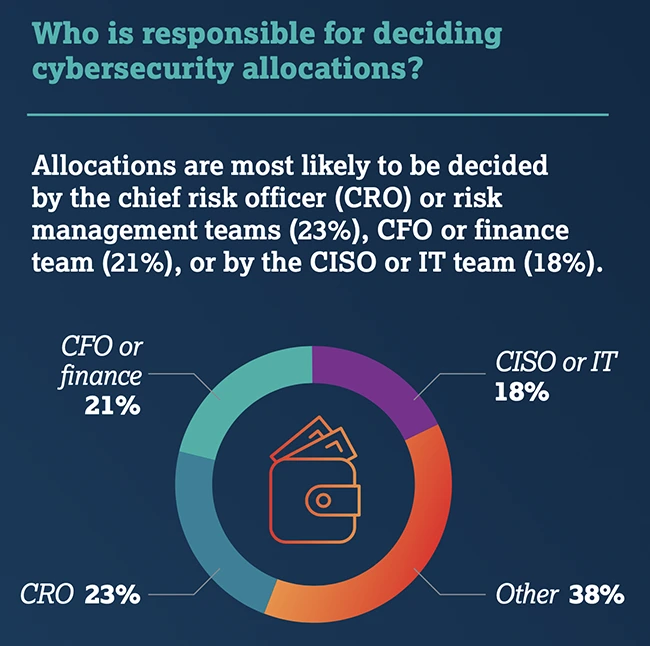
Even with new challenges emerging, many CISOs are struggling to secure the resources they need. Only 7 percent said their cybersecurity budgets had increased significantly year over year, even as threat levels continue to rise.
“The problem is that there’s no glossy return on investment from spending on cybersecurity,” said Mark Flegg, Senior Director of Technology, Security Products and Services at CSC. “It’s like buying insurance. Everyone hates paying for it, but when it’s time to file a claim, that policy is the best thing since sliced bread.”
Flegg added, “You always have to plan for a higher budget year over year. The threats you’ve already been managing don’t just disappear, so you still need funding for those, plus anything new that’s emerged. CISOs have spent a lot of time building firewalls, pulling up the drawbridge to the castle. Now they’re finding that people are building tunnels beneath the moat.”
Closing the gaps with strategy and trusted partners
Regulation adds another layer of pressure. Only 9 percent of respondents said they are fully compliant with the EU’s NIS2 Directive. “In our opinion, the reason NIS2 is number one is because it’s the most time-critical one to deal with at the moment,” said Hrichak. “We’re going through similar processes as we did with GDPR, where everyone knows they need to do something, but they’re not completely sure where to start.”
As for staying agile, Hrichak recommends an outsourcing strategy. “That includes choosing the right provider, not providers, because having many different points of contact can introduce risk. Organizations should streamline their strategy to make sure that if something’s on fire, they know who to reach out to, and don’t have 10 different providers, especially in an intense situation.”