Let’s have an honest conversation about something that keeps security engineers up at night – the vulnerabilities that can turn your carefully designed SSO system into an attacker’s playground. If you’re building or maintaining SSO integrations, understanding these security risks isn’t just academic – it’s the difference between a system that protects your users and one that inadvertently hands over the keys to your application.
Think of SSO security like home security. You might have the best locks on your front door, but if you leave a window open or forget to secure the back entrance, all that front door security becomes meaningless. SSO systems have multiple “entrances” and “pathways” that attackers can exploit, and securing them requires understanding not just the obvious attack vectors, but also the subtle ones that often get overlooked.
Let me walk you through the most common ways SSO systems get compromised and, more importantly, how to protect against these attacks. We’ll start with some foundational concepts and then dive deeper into the specific vulnerabilities that affect OAuth and SAML implementations.
Understanding the SSO Attack Surface
Before we jump into specific vulnerabilities, let’s build a mental model of what attackers are trying to accomplish when they target SSO systems. At its core, SSO is about trust – your application trusts that when an identity provider says “this person is John from Accounting,” that assertion is true and hasn’t been tampered with.
Attackers want to break this trust relationship in one of several ways. They might try to impersonate someone else entirely, getting your application to believe they’re a legitimate user when they’re not. They might try to escalate their privileges, convincing your application that they have more permissions than they actually do. Or they might try to steal authentication tokens or credentials that they can use later to access systems they shouldn’t have access to.
The challenge with SSO security is that the attack surface spans multiple systems. There’s the identity provider, the network communication between systems, your application itself, and often the user’s browser or device. A weakness in any of these components can compromise the entire authentication flow.
This distributed nature of SSO is both its strength and its weakness. When everything works correctly, users get seamless authentication across multiple applications. But when something goes wrong, the impact can be widespread because a single compromised authentication token might grant access to many different systems.
OAuth Vulnerabilities: When Authorization Goes Wrong
Let’s start our deep dive with OAuth, since it’s probably the most widely used authentication protocol in modern web applications. OAuth has some beautiful design principles, but it also has some subtle vulnerabilities that can be exploited if you’re not careful about your implementation.
The most important thing to understand about OAuth vulnerabilities is that they often arise from implementation mistakes rather than flaws in the protocol itself. OAuth gives you a lot of flexibility in how you implement it, but with that flexibility comes the responsibility to make security-conscious choices at every step.
The Authorization Code Interception Attack
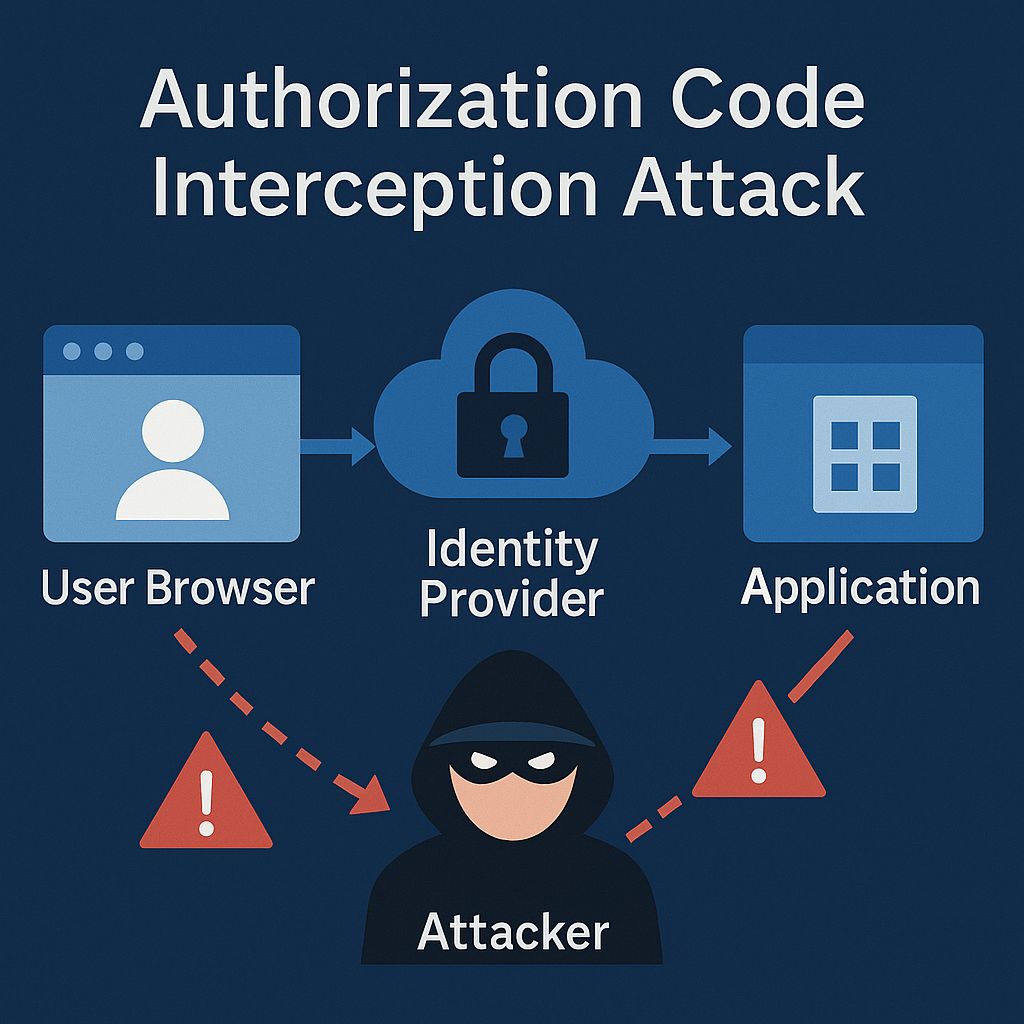
One of the most serious OAuth vulnerabilities is authorization code interception. Let me explain how this works by walking through what should happen in a normal OAuth flow, and then showing you where it can go wrong.
In a typical OAuth authorization code flow, your application redirects the user to the identity provider for authentication. After the user logs in, the identity provider redirects them back to your application with an authorization code in the URL. Your application then exchanges this code for an access token by making a server-to-server request to the identity provider.
The vulnerability occurs if an attacker can intercept that authorization code before your application uses it. Since the code is passed in the URL, it might be logged by web servers, proxy servers, or browser history. If an attacker gains access to these logs, they can steal the authorization code and use it to obtain access tokens for your application.
Here’s what makes this attack particularly dangerous: the authorization code is often valid for several minutes, giving attackers a window of opportunity to use it. And since the code is designed to be exchanged for long-lived access tokens, a successful attack can give an attacker persistent access to user accounts.
The primary defense against this attack is using PKCE (Proof Key for Code Exchange), which we’ll discuss in detail in the mitigation section. But it’s worth understanding that this vulnerability exists because OAuth was originally designed assuming that the communication between your application and the identity provider would always be secure. In practice, there are many ways that communication can be intercepted or logged.
The Redirect URI Manipulation Attack
Another common OAuth vulnerability involves manipulation of the redirect URI – the URL where the identity provider sends the user after authentication. If your OAuth configuration isn’t carefully secured, attackers might be able to manipulate this redirect to send authorization codes to URLs they control instead of your legitimate application.
Let me paint a picture of how this attack works. Suppose your application is configured to accept redirects to https://yourapp.com/oauth/callback. An attacker might try to register a similar domain like https://yourapp-evil.com/oauth/callback and then trick users into starting an OAuth flow that redirects to the malicious domain instead of the legitimate one.
The attack gets more sophisticated when you consider that many OAuth implementations support wildcard or pattern-based redirect URIs to handle complex application architectures. If you’re not careful about how you validate these patterns, attackers might find ways to redirect to domains that match your patterns but are actually under their control.
What makes this attack particularly sneaky is that from the user’s perspective, everything looks normal. They’re redirected to what appears to be a legitimate identity provider, they enter their credentials, and they get redirected to what might appear to be your application. The user has no way of knowing that their authorization code was actually sent to an attacker-controlled server.
The State Parameter Attack
The state parameter in OAuth serves an important security function that’s often misunderstood or incorrectly implemented. The state parameter is supposed to prevent CSRF (Cross-Site Request Forgery) attacks by ensuring that the OAuth callback your application receives corresponds to an OAuth flow that your application actually initiated.
Here’s how the state parameter should work: when your application starts an OAuth flow, it generates a random, unpredictable state value and includes it in the authorization request. The identity provider includes this same state value in the callback to your application. Your application should verify that the state value in the callback matches the one it originally sent, and reject any callbacks with missing or incorrect state values.
The vulnerability occurs when applications either don’t use the state parameter at all, or use predictable values, or don’t properly validate the state value in callbacks. Without proper state validation, attackers can potentially trick users into authorizing access to their accounts by initiating OAuth flows from malicious websites.
Imagine this scenario: a user is logged into your application in one browser tab, and they visit a malicious website in another tab. The malicious website could initiate an OAuth flow that, if successful, would grant the attacker access to the user’s account in your application. The state parameter prevents this by ensuring that only OAuth flows initiated by your application can successfully complete.
SAML Attacks: When Assertions Can’t Be Trusted
Now let’s shift our focus to SAML, which has its own set of unique vulnerabilities. SAML is a more complex protocol than OAuth, and this complexity creates additional attack surfaces that you need to be aware of. The fundamental security principle in SAML is that assertions (the documents that contain user identity information) must be cryptographically signed and verified to ensure they haven’t been tampered with.
The SAML Replay Attack
The SAML replay attack is one of the most well-known SAML vulnerabilities, and it’s a great example of why timestamp validation is crucial in security protocols. Let me explain how this attack works and why it’s so dangerous.
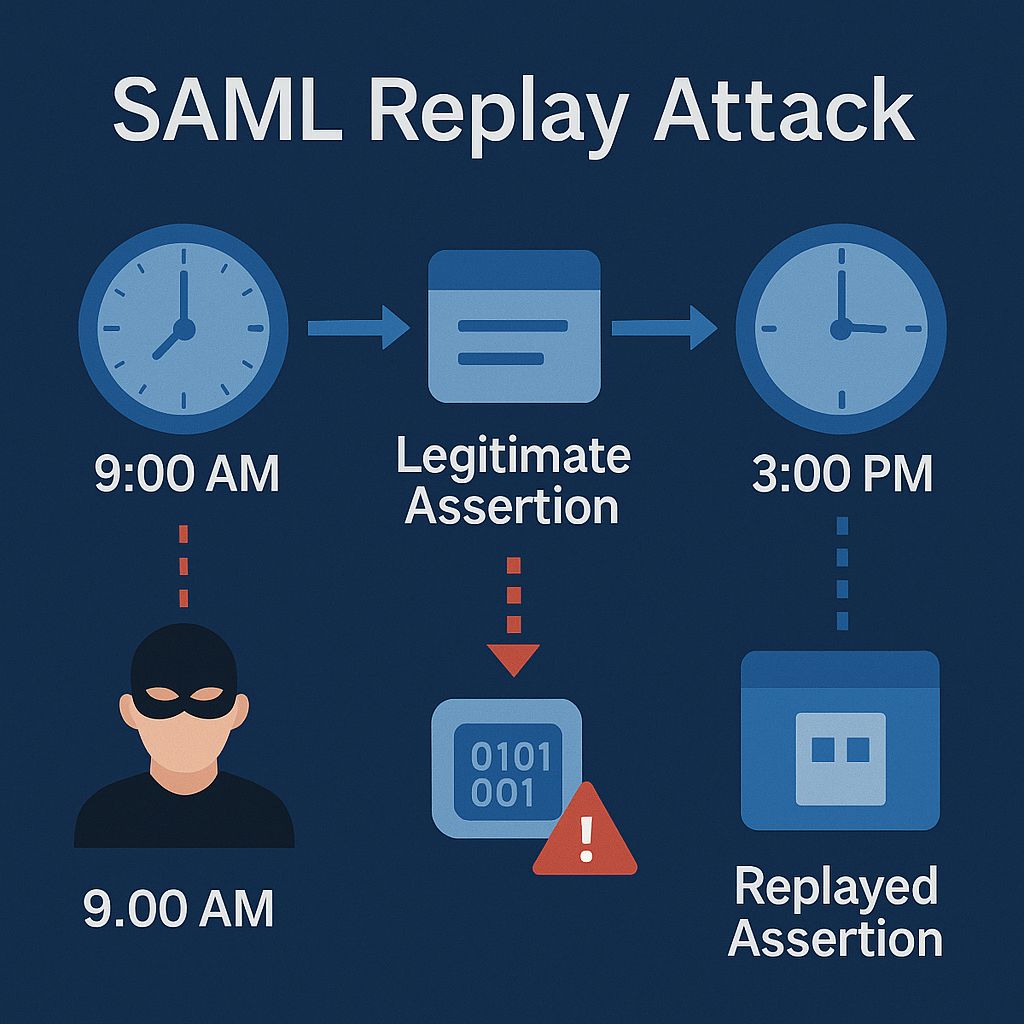
In a SAML authentication flow, the identity provider creates a SAML assertion that contains information about the user (like their username and email address) along with a timestamp indicating when the assertion was created. This assertion is digitally signed and sent to your application, which validates the signature and extracts the user information.
The replay attack occurs when an attacker captures a valid SAML assertion and then “replays” it later to gain unauthorized access. Since the assertion was originally valid and properly signed, your application might accept it even though it’s being used in a different context than originally intended.
Here’s a concrete example: suppose a user logs into your application via SAML at 9:00 AM, and an attacker somehow captures the SAML assertion from that login. If your application doesn’t properly validate timestamps and nonces, the attacker could replay that same assertion at 3:00 PM and gain access to the user’s account, even though the user never attempted to log in at 3:00 PM.
The insidious thing about replay attacks is that they use completely legitimate, properly signed assertions. The vulnerability isn’t in the cryptography or the assertion structure – it’s in your application’s failure to verify that the assertion is being used in the correct temporal and contextual framework.
The SAML Assertion Wrapping Attack
This is a more sophisticated attack that exploits weaknesses in how applications parse and validate SAML assertions. To understand this attack, you need to understand that SAML assertions are XML documents with a specific structure, and the digital signature covers specific parts of that XML structure.
In an assertion wrapping attack, an attacker takes a legitimate, signed SAML assertion and wraps it inside additional XML elements in a way that changes how your application interprets the assertion, while keeping the signature technically valid. The goal is to trick your application into extracting different user information than what was actually signed by the identity provider.
Let me give you a simplified example. Suppose the identity provider creates an assertion saying “user [email protected] has role=user”. An attacker might wrap this assertion in additional XML that makes your application think the assertion says “user [email protected] has role=admin”, even though the original signed assertion is still intact within the modified XML.
This attack works because many XML parsing libraries don’t handle complex XML structures in the same way, and because the digital signature validation might pass even though the application is interpreting the XML differently than intended. It’s a subtle attack that requires deep understanding of both XML parsing and SAML assertion structure.
The SAML Signature Wrapping Attack
Similar to assertion wrapping, signature wrapping attacks exploit the complexity of XML digital signatures. In SAML, the digital signature is supposed to cover the entire assertion to ensure its integrity. However, XML signatures are more complex than simple file signatures, and there are subtle ways to manipulate the XML structure that can confuse signature validation.
In a signature wrapping attack, an attacker manipulates the XML structure of a SAML response in a way that moves the signature to a different part of the document or changes what the signature appears to cover. The goal is to make your application think that a different assertion is signed than what was actually signed by the identity provider.
These attacks are particularly dangerous because they can be difficult to detect. The signature validation might pass all technical checks, but the assertion your application processes might be completely different from what the identity provider intended to send.
Implementing Robust OAuth Security
Now that we understand the vulnerabilities, let’s talk about how to protect against them. Building secure OAuth implementations requires attention to detail at every step of the flow, but the good news is that most of these security measures are well-established and straightforward to implement.
PKCE: Your First Line of Defense
PKCE (Proof Key for Code Exchange) is probably the most important security enhancement you can add to your OAuth implementation. PKCE prevents authorization code interception attacks by ensuring that only the application that initiated an OAuth flow can successfully exchange the authorization code for tokens.
Here’s how PKCE works: when your application starts an OAuth flow, it generates a random code verifier (a long, random string) and derives a code challenge from it using a one-way hash function. The application includes the code challenge in the authorization request to the identity provider, but keeps the code verifier secret.
When the identity provider redirects back to your application with an authorization code, your application exchanges the code for tokens by including both the authorization code and the original code verifier. The identity provider verifies that the code verifier matches the code challenge from the original request before issuing tokens.
The beauty of PKCE is that even if an attacker intercepts the authorization code, they can’t use it without also having the code verifier, which never leaves your application. This makes authorization code interception attacks virtually impossible.
Implementing PKCE in your application looks something like this conceptually:
// When starting OAuth flow
const codeVerifier = generateRandomString(128); // Keep this secret
const codeChallenge = sha256(codeVerifier).base64url(); // Send this to identity provider
// Store codeVerifier securely (in session, encrypted cookie, etc.)
storeCodeVerifier(codeVerifier);
// Redirect to identity provider with code challenge
const authUrl = `${identityProviderUrl}/oauth/authorize?` +
`client_id=${clientId}&` +
`redirect_uri=${redirectUri}&` +
`response_type=code&` +
`code_challenge=${codeChallenge}&` +
`code_challenge_method=S256`;
// When handling callback
const authCode = extractCodeFromCallback();
const storedCodeVerifier = retrieveCodeVerifier();
// Exchange code for tokens with code verifier
const tokenResponse = await fetch(`${identityProviderUrl}/oauth/token`, {
method: 'POST',
body: new URLSearchParams({
grant_type: 'authorization_code',
code: authCode,
redirect_uri: redirectUri,
client_id: clientId,
code_verifier: storedCodeVerifier // This proves we initiated the flow
})
});
The code comments here help illustrate the key insight: the code verifier proves that your application initiated the OAuth flow, making it impossible for attackers to use intercepted authorization codes.
Strict Redirect URI Validation
Protecting against redirect URI manipulation requires being very strict about which redirect URIs you’ll accept. The general principle is to be as specific as possible and avoid wildcards or pattern matching unless absolutely necessary.
Instead of registering broad patterns like https://*.yourapp.com/*, register specific, exact redirect URIs like https://app.yourapp.com/oauth/callback. If you need to support multiple environments or subdomains, register each one explicitly rather than using wildcards.
When validating redirect URIs in your OAuth implementation, use exact string matching rather than pattern matching or URL parsing that might be vulnerable to manipulation. Here’s the kind of validation logic you want:
// Good: Exact matching against a whitelist
const allowedRedirectUris = [
'https://app.yourapp.com/oauth/callback',
'https://staging.yourapp.com/oauth/callback',
'https://dev.yourapp.com/oauth/callback'
];
function validateRedirectUri(providedUri) {
return allowedRedirectUris.includes(providedUri);
}
// Bad: Pattern matching that could be exploited
function insecureValidateRedirectUri(providedUri) {
return providedUri.startsWith('https://yourapp.com/'); // Vulnerable to subdomain attacks
}
The key insight here is that exact matching eliminates entire classes of attacks that rely on subtle manipulations of URLs or domain names.
Proper State Parameter Implementation
Implementing the state parameter correctly requires generating unpredictable values and properly validating them in your OAuth callback handler. The state parameter should be cryptographically random and unique for each OAuth flow.
Here’s how to implement state parameter security properly:
// When initiating OAuth flow
const state = crypto.randomBytes(32).toString('hex'); // Cryptographically random
storeStateForValidation(state); // Store securely for later validation
const authUrl = `${identityProviderUrl}/oauth/authorize?` +
`client_id=${clientId}&` +
`redirect_uri=${redirectUri}&` +
`response_type=code&` +
`state=${state}`;
// When handling OAuth callback
const receivedState = extractStateFromCallback();
const expectedState = retrieveStoredState();
if (!receivedState || receivedState !== expectedState) {
throw new Error('Invalid state parameter - possible CSRF attack');
}
// Only proceed with token exchange if state validation passes
The critical security property here is that the state value must be both unpredictable (so attackers can’t guess valid values) and tied to the specific user session (so attackers can’t reuse state values from other users).
Defending Against SAML Attacks
SAML security requires a different set of defenses because the attack vectors are different from OAuth. The core principle in SAML security is rigorous validation of assertions, including their structure, signatures, and temporal validity.
Preventing SAML Replay Attacks
Defending against replay attacks requires implementing both timestamp validation and nonce tracking. Every SAML assertion should include a timestamp indicating when it was created, and your application should reject assertions that are too old.
Additionally, each assertion should include a unique nonce (a random identifier), and your application should track used nonces to prevent the same assertion from being processed multiple times. Here’s how this defense works in practice:
// When processing SAML assertion
function validateSAMLAssertion(assertion) {
// Check timestamp - reject assertions older than 5 minutes
const assertionTime = parseTimestamp(assertion.issueInstant);
const now = new Date();
const maxAge = 5 * 60 * 1000; // 5 minutes in milliseconds
if (now - assertionTime > maxAge) {
throw new Error('SAML assertion is too old - possible replay attack');
}
// Check nonce - reject if we've seen this assertion before
const nonce = assertion.id;
if (hasProcessedNonce(nonce)) {
throw new Error('SAML assertion nonce already used - replay attack detected');
}
// Store nonce to prevent future replay
storeProcessedNonce(nonce, assertionTime);
// Additional validation steps...
}
The nonce tracking system needs to be persistent and shared across all instances of your application to be effective. You might implement this using a database, Redis cache, or other shared storage mechanism.
XML Signature Validation Best Practices
Protecting against XML signature attacks requires using robust XML parsing libraries and implementing strict signature validation. The key insight is that you need to validate not just that the signature is cryptographically correct, but also that it covers the parts of the XML document that you actually care about.
Use XML parsing libraries that are specifically designed for security-sensitive applications and that have built-in protections against common XML attacks. Avoid writing your own XML parsing code or using general-purpose libraries that might not handle edge cases securely.
When validating signatures, verify that the signature covers the entire assertion element and not just sub-elements. Be explicit about which parts of the XML document must be signed for the assertion to be considered valid.
Here’s the conceptual approach to secure SAML signature validation:
function validateSAMLSignature(samlResponse) {
// Parse XML using security-hardened parser
const doc = parseXMLSecurely(samlResponse);
// Verify that the assertion element is signed
const assertion = doc.querySelector('saml:Assertion');
if (!assertion) {
throw new Error('No assertion found in SAML response');
}
// Verify that the signature covers the entire assertion
const signature = assertion.querySelector('ds:Signature');
if (!signature) {
throw new Error('SAML assertion is not signed');
}
// Validate signature cryptographically
const isValid = cryptographicallyValidateSignature(assertion, signature);
if (!isValid) {
throw new Error('SAML assertion signature is invalid');
}
// Verify certificate chain and trust
validateCertificateChain(signature.certificate);
}
The important principle here is defense in depth – you’re not just checking that a signature exists, but verifying that it covers the right content and comes from a trusted source.
Assertion Structure Validation
To prevent assertion wrapping and signature wrapping attacks, implement strict validation of the XML structure of SAML assertions. This means not just parsing the XML, but also verifying that it conforms exactly to the expected SAML schema structure.
Define clear expectations for how SAML assertions should be structured and reject any assertions that don’t match these expectations, even if they’re technically valid XML. This approach prevents attacks that rely on unusual or unexpected XML structures.
Building a Comprehensive SSO Security Strategy
Protecting against SSO vulnerabilities isn’t just about implementing individual countermeasures – it’s about building a comprehensive security strategy that addresses the entire authentication flow. Let me walk you through the key components of a robust SSO security strategy.

Defense in Depth
The most effective SSO security strategies use multiple layers of protection, so that if one layer fails, others can still prevent successful attacks. This might include network-level protections (like IP whitelisting), application-level protections (like the OAuth and SAML security measures we’ve discussed), and monitoring-based protections (like anomaly detection).
Each layer serves a different purpose and protects against different types of attacks. Network-level protections can prevent attacks from obviously malicious sources. Application-level protections prevent attacks that exploit protocol vulnerabilities. Monitoring-based protections can detect attacks that bypass other defenses.
Regular Security Audits
SSO implementations should be audited regularly by security professionals who understand the specific vulnerabilities we’ve discussed. These audits should include both code review (to identify implementation vulnerabilities) and penetration testing (to verify that the implemented protections actually work in practice).
Pay particular attention to configuration management during these audits. Many SSO vulnerabilities arise not from implementation bugs, but from configuration errors that create security gaps. Make sure your audit process includes reviewing OAuth client configurations, SAML endpoint configurations, and certificate management practices.
Monitoring and Alerting
Implement comprehensive monitoring for your SSO systems that can detect both successful attacks and attempted attacks. Look for patterns like unusual geographic distribution of login attempts, high numbers of authentication failures, or authentication attempts using expired or invalid tokens.
Set up alerts for security-relevant events like failed signature validations, rejected replay attempts, or OAuth flows with invalid state parameters. These events might indicate attempted attacks, and investigating them promptly can help you identify and address security issues before they become serious problems.
Understanding and mitigating SSO vulnerabilities is an ongoing process, not a one-time implementation task. As attack techniques evolve and new vulnerabilities are discovered, you’ll need to update your security measures accordingly. The key is building security into your development and operational processes so that protecting against these vulnerabilities becomes a natural part of how you build and maintain your SSO systems.
The security measures we’ve discussed – PKCE, strict redirect URI validation, proper state parameter implementation, SAML replay protection, and robust signature validation – form the foundation of secure SSO implementations. But remember that security is not just about implementing the right technical controls; it’s also about maintaining those controls over time, monitoring for attacks, and continuously improving your security posture as new threats emerge.
*** This is a Security Bloggers Network syndicated blog from SSOJet authored by Devesh Patel. Read the original post at: https://ssojet.com/blog/common-sso-vulnerabilities-and-mitigations-protecting-your-authentication-flow/






