
As digital transformation becomes a strategic imperative, development teams have emerged as a pillar of organizations. Agile and DevOps practices have revolutionized the pace of innovation, enabling businesses to respond rapidly to evolving market demands. However, this accelerated development comes with a cost—the expansion of the application attack surface. Every new feature or update introduces potential entry points for hackers to exploit sensitive data, disrupt operations, and launch targeted attacks. To mitigate these risks, organizations must embed security into every stage of development. Leveraging tools like a website scanner is crucial for identifying and remediating vulnerabilities in real time, ensuring that web applications remain secure, resilient, and compliant in a fast-paced digital environment.
What is a Website Scanner?
Organizations commonly rely on website vulnerability scanners to protect their applications from malicious attacks. These automated tools are designed to identify exploitable weaknesses in applications that could be leveraged by threat actors. As a standard component of network security across various industries, vulnerability scanning is often used alongside penetration testing to establish a multi-layered defense strategy against cyber threats.
While various types of website scanners can detect vulnerabilities at different stages of the software development life cycle (SDLC), they often fall short in offering continuous visibility into the evolving application attack surface. Instead, they deliver only a snapshot in time, requiring repeated scans and extensive analysis to maintain effective vulnerability management.
The Process Behind Website Scanning
A website scanner automates the detection and evaluation of security vulnerabilities within a website. It generally performs this task through a series of well-defined stages.
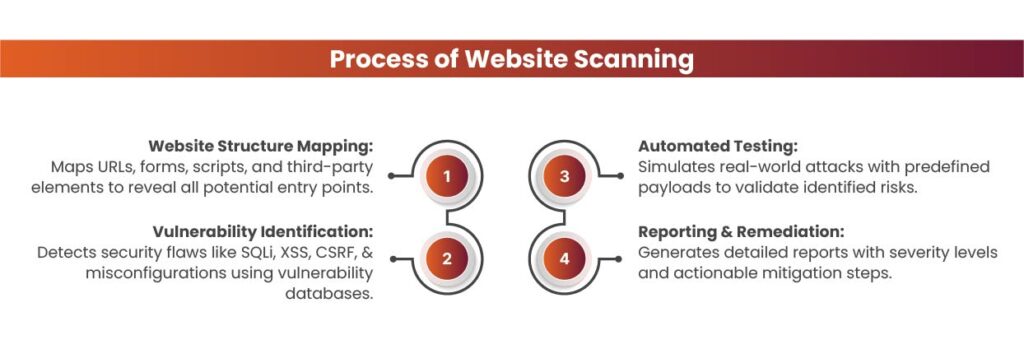
Website Structure Mapping
The initial phase involves a website scanner systematically mapping the website’s architecture—capturing URLs, input forms, scripts, and third-party integrations. This step helps identify all potential entry points, ensuring comprehensive coverage of the website’s exposed surface for accurate vulnerability assessment.
Identification of Vulnerabilities
Once the website structure is mapped, the scanner proceeds to its primary task—identifying vulnerabilities. It inspects the application for common security flaws such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and file inclusion issues. The scanner detects both known vulnerabilities using established databases and uncovers potential risks caused by misconfigurations in server settings or insecure application code.
Automated Testing
At this stage, the website scanner leverages a mix of predefined test cases and techniques to simulate potential attack scenarios. It may, for instance, try injecting malicious code or scanning for insecure server configurations. By mimicking cyberattack methods, the scanner can uncover vulnerabilities that could be exploited by threat actors in live environments.
Reporting
After the scan is completed, website scanner produces a comprehensive report detailing the discovered vulnerabilities, their severity levels, and recommended mitigation steps. The report typically includes technical insights such as the type of vulnerability, impacted components, and actionable remediation guidance—enabling security teams to proactively resolve issues before they are exploited.
How Website Scanners Find Vulnerabilities Faster?
Website scanners play a crucial role in accelerating the detection of security vulnerabilities within web applications. Tools like AutoSecT, Kratikal’s AI-driven vulnerability management and pentesting solution, automate the entire scanning process, starting with mapping the website’s structure, including URLs, forms, scripts, and third-party components. They then simulate real-world attack techniques using predefined test cases, heuristics, and vulnerability databases to identify issues such as SQL injection, cross-site scripting (XSS), CSRF, insecure configurations, and outdated components.
Unlike manual testing, which can be time-consuming and inconsistent, automated website scanners like AutoSecT deliver fast, repeatable, and comprehensive scans. This allows development and security teams to detect vulnerabilities early in the software development lifecycle (SDLC), significantly reducing exposure time. With support for continuous scanning across dynamic application environments, AutoSecT is an essential tool for organizations embracing DevSecOps and aiming to maintain strong, proactive security postures.



