Choosing an attack surface management or a vulnerability management platform often comes down to identifying which tool provides the right mix of visibility, automation, and precision that matches your team’s needs, ideally at as low a price as possible. A few years ago, attack surface management tools were extremely expensive and only available to larger corporations. Recently, however, more affordable solutions emerged as more organizations realized the need to protect their entire attack surface.
Two well-known names in this space—Detectify and Intruder—claim to offer attack surface management and vulnerability management capabilities for not too steep a price. In fact, Detectify starts as low as €82/month and Intruder at €99/month, if billed annually. However, at this price point, neither of them offers a solution that can actually handle attack surface management—in both cases, you’ll need to pay more to get your external attack surface covered. How much more and what are the missing functions? Is there an alternative that can help you with attack surface management for less? Let’s find out!
In this detailed comparison, we break down how these two platforms stack up across key areas such as pricing and the four stages of the external attack surface management (EASM) process: asset discovery, vulnerability scanning, vulnerability prioritization and remediation, and continuous monitoring. We also introduce Attaxion as a more affordable and, in some aspects, more capable alternative to both of them.
Pricing
When it comes to pricing, Detectify and Intruder have different pricing philosophies based on their target use cases.
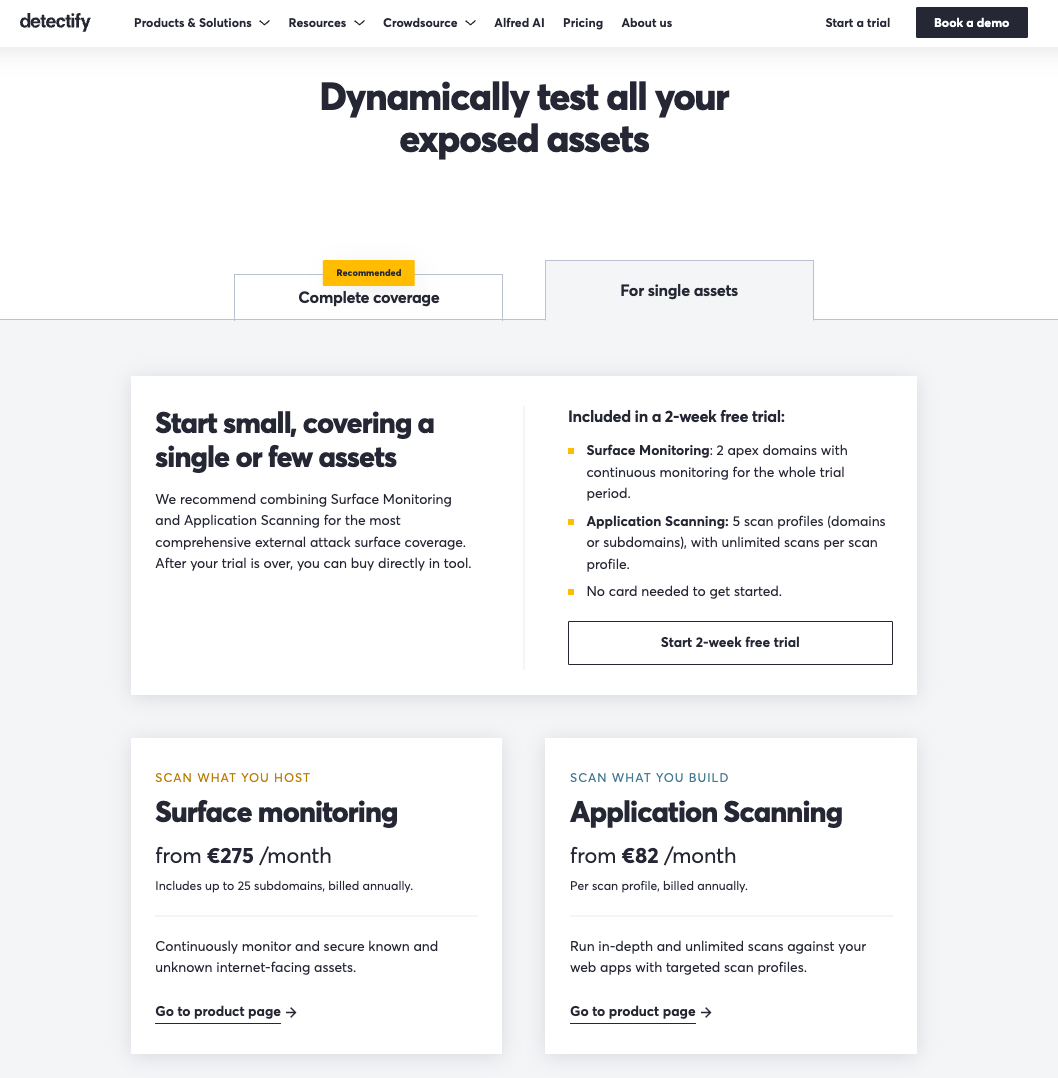
Detectify
Detectify structures its pricing around two main product lines:
- Application scanning, focused on in-depth web application testing, starts at a relatively low entry price of €82/month per scan profile, if billed annually. The plan offers unlimited scans for one web app, including authenticated testing. That’s a dynamic application security testing (DAST) solution, and it doesn’t enable attack surface management due to the complete lack of asset discovery. So, within the scope of this article, we’re more interested in the other option.
- Surface monitoring, which enables continuous external asset tracking, comes in at €275/month for up to 25 subdomains, if billed annually. More assets would be more expensive, but the price per additional asset isn’t too steep. This product doesn’t include authenticated scanning, so, you’ll need to combine it with Application scanning if you need it. What Surface monitoring does offer is asset discovery, allowing you to find, secure, and continuously monitor known and unknown internet-facing assets, which makes it a full-fledged EASM platform.

Overall, Detectify seems to be on the lower end of EASM prices, but some users are noting that if you want to monitor multiple sites, combining Application scanning and Surface monitoring, the costs scale rapidly.
Detectify offers a 14-day free trial. Unfortunately, more detailed pricing isn’t readily available without contacting sales.
Intruder
Intruder’s approach to pricing is to offer four different tiers of one and the same product: Essential, Cloud, Pro, and Enterprise plans, with different kinds of licenses on top of that.
- Essential. Starting at $99/month (if billed annually), the Essential plan offers very limited functionality, boiling down to on-demand scans of predefined targets. There are no integrations, no asset discovery, no emerging threat scans, and you can schedule only one regular recurring scan.
- Cloud. At $153/month (if billed annually), the Cloud plan adds cloud asset syncing for AWS, Azure, and Google Cloud, as well as emerging threat scans and integrations. It includes everything in Essential, with added support for automatically syncing and scanning of new cloud-hosted assets. This tier can be considered an EASM solution at least to some extent, as it has at least some asset discovery capabilities (even though it only works for whatever you have in the public clouds).
- Pro. The Pro plan, priced at $204/month (if billed annually), offers everything in Cloud plus internal scanning. It’s worth noting that Intruder cannot discover internal hosts—you’ll need to manually install its endpoint software on them.
- Enterprise. Pricing for the Enterprise plan is available only upon request. It builds on the Pro plan with features like tailored onboarding and a dedicated customer success manager. Most importantly, only this tier offers subdomain discovery. On all other tiers, Intruder only deals with known assets: manually defined targets and whatever is added from cloud integrations. Only the Enterprise tier can be considered a full-fledged attack surface management solution.

All prices above are for 5 infrastructure licenses and an annual billing cycle. Further licenses come at additional cost, as do application licenses that enable authenticated scanning.
Detectify vs Intruder: Pricing
Detectify may appeal to those who want real external attack surface management at a relatively low price. Unlike Intruder (on its PLG plans), Detectify offers subdomain discovery for its Surface monitoring product at its base price.
However, for those on an even shorter budget, Intruder’s Cloud and Pro tiers may be an interesting option, thanks to the cloud sync. Intruder has recently updated its pricing twice: once in 2024, and once in 2025, when it introduced the Cloud tier. Both times the prices have increased.
It’s worth noting that there are even more budget-friendly Detectify and Intruder alternatives that offer full-fledged asset discovery and start as low as $129/month (even lower if billed annually).
Asset Discovery
Effective vulnerability management starts with knowing what you have. Modern processes such as attack surface management relies on mapping assets and asset-to-asset connections, covering assets that you are aware of and those that exist on your network without your knowledge.
Detectify
Detectify’s Surface monitoring is an external attack surface management solution—it focuses solely on web-facing assets. First, you need to provide and verify some root assets, and then, Detectify will automatically discover subdomains, scan ports, perform DNS lookups to get related IP addresses, assess SSL/TLS certificates, and more.
Every new subdomain that it discovers will be added to the “Attack surface” tab and Detectify will automatically scan it for vulnerabilities—you don’t need to schedule anything, it just works out of the box, after you’ve verified the root assets. Every subdomain that is added to your attack surface counts towards the billed asset count.
Detectify has integrations with major public cloud providers that allow it to pull the lists of assets directly from the cloud accounts, but for that, you need to set up these integrations. Fortunately, they are available for all users.

Intruder
As mentioned above, Intruder doesn’t offer cyber reconnaissance on any plans, except Enterprise. So, its asset discovery capabilities mostly boil down to the very same integrations with AWS, GCP, and Azure—these are available on Cloud and Pro plans and allow it to extract the list of assets from the clouds.
After Intruder pulls the lists of assets from the cloud account, it starts automatically scanning them for vulnerabilities. If you add a new asset in the cloud account, Intruder can automatically add it as a target. That works only for the main public clouds though.
What makes Intruder stand out in the positive sense is that it can monitor internal assets just like external ones. But there is no internal network discovery—you’ll need to manually add each internal asset and install the Intruder agent on all of them. The agent is compatible with Windows, Linux, and macOS.

Verdict on Asset Discovery
When comparing Detectify and Intruder from the asset discovery perspective, Detectify seems to be a clear winner, offering proper external asset discovery and subdomain enumeration with Surface management.
Intruder gates this feature behind the highest pricing tier which requires talking to sales. On cheaper plans, Intruder only offers to add assets manually or connect to the cloud accounts to extract the list of assets from them. However, this means that on self-serve plans, Intruder cannot discover so-called unknown unknown assets (the assets you don’t even suspect exist on your network), limiting the visibility into your attack surface. Detectify is perfectly capable of that.
Vulnerability Scanning
Vulnerability scanners differ significantly in how broad and deep they go. In this aspect, Detectify and Intruder are, perhaps, even more different than in the attack surface discovery aspect.
Detectify
Detectify doesn’t use any popular vulnerability scanners like OpenVAS or Tenable Nessus and, instead, relies on its proprietary scanning engine, enhanced by contributions from its Crowdsource community of several hundreds of ethical hackers. This collaboration allows Detectify to incorporate the latest security research and attack vectors into its scanning tools.
Authenticated scanning is supported exclusively in the Application scanning product, while Surface Monitoring only covers non-authenticated scans. With Application scanning, users can configure scans to access authenticated areas of their web applications by providing basic authentication credentials (that makes Detectify a gray-box scanner).
In Application scanning, users can set up recurring scans on a daily, weekly, biweekly, or monthly basis. Additionally, scans can be triggered manually or configured to start automatically when new versions of Application scanning are released. Scan performance can be adjusted by setting limits on the number of requests per second to accommodate the responsiveness of the target application.
Surface monitoring runs continuously, both discovering new assets and scanning them for vulnerabilities or security misconfigurations.

Here, Detectify has two interesting features. Firstly, it runs payload-based scanning, which reduces the number of false positives. At the same time, payload-based scans are more intrusive, with a potential to overwhelm a web application or trigger an intrusion detection system.
Secondly, it has Alfred AI—an internal machine learning engine that discovers vulnerabilities and builds tests for them. Every test is reviewed by humans so that it doesn’t add too much noise.
Intruder
Intruder employs different scanning engines across its subscription tiers—the more you pay, the higher quality scanning you get:
- Essential: Relies on OpenVAS, a popular open-source vulnerability scanner.
- Cloud: Combines OpenVAS with Nuclei, another open-source scanner known for its speed and extensibility.
- Pro: Drops both open-source scanners in favor of Tenable Nessus, a commercial-grade scanning engine. Since Tenable is perfectly capable of scanning endpoints as well, that allows Intruder to offer internal scanning on this plan in addition to external scans.
- Enterprise: Keeps Tenable Nessus, but brings back Nuclei in addition to it, which theoretically offers more different checks and a broader vulnerability coverage.
On top of all that, for web application security, Intruder incorporates OWASP ZAP, yet another open-source web application scanner, this one maintained by the OWASP Foundation and Checkmarx. This tool allows for both authenticated and unauthenticated scanning of web applications and APIs.

Intruder provides flexible scanning schedules, including weekly, monthly, or quarterly network scans, with daily scans available only on the Enterprise plan. Users can also initiate manual scans or set up scheduled scans as needed.
A feature that makes Intruder stand out is Emerging Threat Scans, which automatically initiate scans when new vulnerabilities are added to Intruder’s database.This feature is available on the Cloud plan and higher tiers. The Enterprise tier also includes Rapid Response Scans, targeting threats actively exploited in the wild.
Verdict on Scanning
In the Detectify vs Intruder debate, Detectify arguably wins for depth in web application scanning, driven by its researcher-contributed tests. Also, its proprietary payload based scanner may seem interesting to those who are not afraid of how intrusive it could be.
However, Intruder is more flexible with the selection of industry-standard scanners that it offers on different plans, as well as with its internal assets scanning. It’s worth noting that external penetration testers are likely to use one of the scanners on the Intruder’s list. So, if one of the goals of your vulnerability management program is to streamline pentests and reduce preparation efforts, Intruder may be the right choice for you.
Vulnerability Prioritization and Remediation
Detecting vulnerabilities is one thing; helping teams act on them is another. Here’s how these tools support vulnerability prioritization and remediation workflows.
Detectify
Detectify allows you to sort vulnerabilities by severity, also showing you assets with the most vulnerabilities or latest security policy alerts. Also, you can add tags to assets to highlight their business criticality. That’s it for prioritization with Detectify.
When it comes to help with remediation, it boils down to 1-click creation of support tickets in various task trackers including Atlassian Jira and Trello automatically filled out with necessary vulnerability details and remediation suggestions. Integrations rely on the Workato platform, so there’s plenty of ticketing systems that Detectify can integrate with.
Detectify offers a decent amount of information about issues that it discovers including references and sometimes even specific pieces of code that spawned the issue. Every issue can be tagged as fixed, false positive, or accepted risk.

Intruder
Intruder goes a few steps further than Detectify in prioritization, offering CVSS and EPSS scores for each CVE vulnerability, along with CISA KEV catalog status—indicating whether a vulnerability is known to be exploited in the wild.
In addition to these external references, Intruder calculates a custom severity score that factors in CVSS, EPSS, and CISA KEV data, as well as its own internal research to help teams focus on the most critical issues. However, they admit that most often this score isn’t different from CVSS.

Users can manage findings by snoozing them as accepted risks, marking them as false positives, or flagging them as mitigated through compensating controls. After applying a fix, users can manually trigger a rescan to confirm whether the issue has been fully resolved.
For remediation workflows, Intruder integrates directly with popular task management and ticketing systems, including Atlassian Jira, ServiceNow, and GitHub. Users can configure automatic ticket creation based on scan results, ensuring that vulnerabilities are turned into actionable tasks without manual copying or extra steps.
Verdict on Prioritization
When it comes to vulnerability prioritization, Detectify keeps it simple with CVSS score being the only parameter for prioritization. Intruder is a few steps ahead with data such as EPSS and CISA KEV status, as well as their own custom scoring.
When it comes to remediation workflows, Intruder and Detectify seem to be roughly the same—both have integrations with the main platforms and allow 1-click ticket creation. Neither offer automated remediation workflows like automatically closing ports or anything like this—such features are only available in much more complex and expensive platforms.
Continuous Monitoring
Attack surface management isn’t a once-a-month activity—it’s continuous, and one of its goals is to provide ongoing visibility into the organization’s attack surface and its changes.
Detectify
Detectify’s Surface monitoring continuously scans both the network for new assets and the assets for security vulnerabilities and misconfigurations. Application scanning by default is scheduled to run weekly scans, but the user can customize it however they want.
When Detectify discovers something worthy of the user’s attention, it can send a notification. It uses the Workato platform to integrate with various services including Slack, Microsoft Teams, and email. Workato also allows the user to create recipes, customizing what happens when something is discovered. That means you can, for example, choose to get Slack notifications for all vulnerabilities with CVSS score over 5 and email notifications for crowdsourced vulnerabilities with severity score above 7.
Detectify also has an API that allows the user to trigger scans and get their results programmatically. An important feature that Detectify has is Custom Policies—it allows security teams to create custom security rules using simple IF-THEN logic to monitor their external assets. Integrated into Surface Monitoring, it lets users define conditions—such as flagging when unexpected ports are open, certain technologies like WordPress are detected, or DNS records change—and assigns severity levels to each rule. When a policy violation occurs, Detectify automatically generates alerts, if you’ve set up this kind of notifications.

Intruder
Intruder provides continuous vulnerability monitoring and can automatically sync with cloud environments as new assets are added. Users can schedule scans at different intervals—daily, weekly, monthly, or quarterly—and also trigger scans manually or through the API. Regular network scans follow the cadence of the selected plan: monthly on Essential, weekly on Cloud and Pro, and daily on the Enterprise plan. In addition, when new vulnerabilities are added to Intruder’s database, Emerging Threat scans automatically assess relevant assets.
Intruder integrates with notification platforms like Slack and Microsoft Teams, allowing users to customize alerts based on specific criteria, such as vulnerability severity or scan outcomes.
For reporting, Intruder offers detailed vulnerability assessment reports that include information on identified issues, affected assets, and remediation guidance. Reports can be exported in different formats and integrated with compliance platforms like Drata and Vanta to support audit and reporting workflows.

Verdict on Monitoring
Detectify offers more visibility into network changes and automatically scans all assets it discovers, while Intruder can only do that for synced cloud assets on most plans. Also, security teams may find Detectify’s Custom Policies very helpful.
When it comes to notifications, both platforms are equally good and flexible. As for reporting, Intruder is, perhaps, a step ahead with its nice reports and integrations with compliance platforms Drata and Vanta that can automatically ingest them.
A More Affordable Alternative with Better Discovery: Attaxion EASM
Detectify and Intruder stand out from the crowd because most other tools capable of helping with EASM are quite expensive, while these two can be afforded even by smaller companies. But there is an alternative to Detectify and Intruder that is even more affordable and yet doesn’t sacrifice key functionalities,—Attaxion.
Why Choose Attaxion Over Detectify and Intruder?
In a way, Attaxion offers the best from both worlds, combining the good from the two platforms at a lower price. It bests both Detectify and Intruder in attack surface discovery, outperforms Detectify in prioritization and Intruder in the continuous monitoring of the entire external attack surface, with more assets covered even on the cheapest plan.
| Detectify | Intruder | Attaxion | ||
| Starting price (for external attack surface management) | €275/month | $153/month | $129/month | |
| Assets monitored | 25 | 5 | 40 | |
| Asset coverage | ⭐⭐ | ⭐ | ⭐⭐⭐ | |
| Continuous scanning of the entire attack surface | ✅ | ❌ | ✅ | |
| Prioritization context | CVSS | ✅ | ✅ | ✅ |
| EPSS | ❌ | ✅ | ✅ | |
| CISA KEV | ❌ | ✅ | ✅ | |
| One-click remediation request creation | ✅ | ✅ | ✅ | |
| Daily network scans | ✅ | ❌(except on Enterprise) | ✅ | |
More Affordable Pricing – While Intruder’s Cloud plan (the cheapest of their plans that is somewhat capable of helping security teams with external attack surface management) starts at $153/month for up to 5 licenses and Detectify’s Surface monitoring would cost you about $305/month (€275/month, as Detectify’s priced in euros) for up to 25 assets, Attaxion starts as low as $129/month for up to 40 assets.
At this price, it offers all the functionalities that it has, including continuous discovery and integrations.

Better Discovery Capabilities – Attaxion is a young EASM platform with its primary focus being attack surface discovery.
In this regard, Attaxion beats both Detectify and Intruder, simply because it generally can find many more assets than either of those platforms. It relies on both passive and active subdomain enumeration with over a dozen of different cyber-reconnaissance techniques, as well as premium DNS and WHOIS data.
In our tests, Attaxion found more subdomains than Detectify or Intruder (the latter relying only on cloud sync). On top of that, Attaxion finds and scans other types of assets that are not domains or subdomains such as CIDRs, open ports, and even exposed email addresses.
Attaxion also builds dependency and discovery graphs for each asset, showing how it was discovered and what assets depend on it to give you a clear understanding of the attack paths potential threat actors might take. Like Detectify, it builds a full technology inventory as well.

Continuous Scanning – While Intruder sticks to a scanning schedule with emerging threat scans on top, both Detectify and Attaxion scan continuously. They are always on the watch for previously undiscovered connected assets—and once they find them, they scan them for security issues.
Attaxion is less intrusive than Detectify, primarily relying on the same OWASP ZAP that Intruder uses for application scanning (but Intruder requires you to buy application licenses, while Attaxion doesn’t distinguish between infrastructure and web apps).
Flexible Prioritization – For vulnerability prioritization, Attaxion offers the same flexibility and amount of context as the better of the two platforms—Intruder. They both combine CVSS and EPSS scores with CISA KEV data on real-world exploitation—something that Detectify lacks.

– Unlike Intruder (on all plans but the expensive Enterprise), Detectify and Attaxion run network scans with a much higher regularity—roughly daily. So, if some new vulnerable assets appear on your network, you’ll know about it much faster with Attaxion or Detectify than with Intruder.
Similarly, if someone decides to change configurations or accidentally messes up security headers, Detectify and Attaxion will discover it earlier thanks to their continuous scanning for all sorts of vulnerabilities that are not limited to emerging threats.

Being a young platform, Attaxion lacks some of the bells and whistles the older ones have, such as some integrations and polished reports. But it outperforms them when it comes to core capabilities.
Conclusion
Both Detectify and Intruder are well-known tools that have their pros and cons. And then, there is Attaxion—a dark horse that combines most of their pros, while having some of its unique smaller drawbacks, but also costs less.
Intruder
Pros:
- Friendly user interface
- Broad selection of scanners
- Good prioritization capabilities
Cons:
- No cyber reconnaissance on most plans
- Doesn’t keep track of your attack surface changes (only through cloud connectors)
- Limited features on cheaper plans
- Gets quite expensive when used for more than a few assets
Choose Intruder if you need a DAST solution and don’t care about attack surface discovery. Or if you have a big security budget and can go for the Enterprise plan.
Detectify
Pros:
- Continuous attack surface discovery
- Crowdsourced vulnerability data
- Security policies monitoring
Cons:
- Poor risk prioritization capabilities
- Could be hard to set up
Choose Detectify if you’re worried about zero-days and want help in enforcing security policies across the organization.
Attaxion
Pros:
- Best attack surface discovery capabilities in class
- Rich context for prioritization
- Truly continuous monitoring
- Most affordable EASM on the market
Cons:
- Limited integrations
- Basic reporting capabilities
Choose Attaxion if you want to have a full picture of your external attack surface and continuous monitoring. Or if you have a very tight security budget. Or both.
To learn more, you can start a free 30-day trial of Attaxion or book a personalized demo.