Abstract
The growing adoption of intelligent transportation systems and connected vehicle networks has raised significant cybersecurity concerns due to their vulnerability to cyberattacks such as spoofing, message tampering, and denial-of-service. Traditional intrusion detection systems struggle to cope with the dynamic and high-volume nature of vehicular data, often leading to high false positives and limited adaptability. To address this problem, this study proposes an enhanced deep learning-based optimization framework for detecting cyberattacks in vehicle networks. The methodology employs the UNSW-NB15 dataset, with data preprocessed using Maximum-Minimum Normalization. Feature extraction is performed using the Discrete Fourier Transform (DFT), capturing frequency-domain patterns indicative of anomalies. Detection is executed through an Improved Long Short-Term Memory (ILSTM) model, whose parameters are optimized using the Crocodile Optimization Algorithm (COA), aiming to maximize classification accuracy. Experimental results demonstrate that the proposed ILSTM-COA model significantly outperforms existing techniques, achieving 98.9% accuracy and showing notable improvements across sensitivity, specificity, and other performance metrics. This model offers a robust, scalable, and real-time solution for safeguarding vehicular networks against evolving cyber threats.
Introduction
As the world embraces intelligent transportation systems and autonomous driving, connected vehicle networks have emerged as a vital part of modern infrastructure1. Vehicle-to-Everything (V2X) communication, which facilitates real-time data exchange among vehicles, roadside infrastructure, pedestrians, and cloud services, is essential for enhancing road safety, optimizing traffic flow, and improving the overall driving experience2. Yet, the rise in connectivity and data sharing within these vehicle networks has made them open to various cybersecurity risks. This has turned the detection and prevention of cyberattacks into a big challenge for both researchers and industry experts3. Cyberattacks such as spoofing, message tampering, replay attacks, and Denial of Service (DoS) can put at risk the safety, privacy, and effectiveness of vehicle networks4. For example, a spoofing attack could twist vehicle communication causing false traffic alerts or unwanted actions. A DoS attack might cut off communication channels stopping crucial safety messages from reaching their targets5. These security breaches not put drivers and passengers in danger but can also upset larger transportation networks6.
Regular Intrusion Detection Systems (IDS) cannot keep up with the ever-changing and tricky world of vehicle networks7. They often rely on rules or known patterns, which limit them to finding familiar attack types and make it hard for them to adapt to new threats8. Also connected vehicles create tons of real-time communication data, so better detection models are needed that can look at time-based info and spot signs of cyber dangers9. Deep learning has stepped up as a great way to catch cyberattacks because it can learn and understand complex data patterns. These models excel at handling data that comes in a sequence, like Controller Area Network (CAN) bus messages, and can pick out weird stuff that might mean someone is trying to break in10. To make these deep learning models even better, optimization algorithms can be added to help choose the right features cut down on processing power needed and tweak the model settings11. When deep learning and optimization are put together, more attacks will be caught and fewer false alarms are also attained, which is super important to keep cyberattack detection systems reliable in vehicle networks12.
This study explores how to build a deep learning optimization model that spots cyberattack in vehicle networks. The model proves its worth by catching different cyber threats, like spoofing, DoS, and message injection attacks even when the data is messy or incomplete13. By handling tons of vehicle data and keeping up with new threats, this system keeps connected vehicles safe. Plus, the model can grow to fit into today’s smart traffic systems making roads safer14. Mixing deep learning with optimization tricks offers a great way to beef up cybersecurity in vehicle networks. Using smart models to look at how vehicles talk to each other and spot weird stuff means threats can be caught as they happen and make the system tougher15. As vehicle networks get fancier, having strong systems to catch cyberattacks will be key to keeping traffic systems safe and reliable. This shows why this research matters so much for keeping vehicles safe from cyberattacks.
The paper contribution is as below.
-
To propose a new deep learning-based optimization approach for enhancing the detection of cyberattacks in vehicle networks by gathering the dataset from the UNSW-NB15 Dataset.
-
To pre-process the gathered data by the maximum-minimum normalization method and to extract the features from it with the help of DFT approach.
-
To do the detection of the extracted features by the novel ILSTM, where the parameters of conventional LSTM is performed by the nature inspired optimization algorithm called COA, with the consideration of maximizing accuracy as the fitness function.
The paper organization is as follows. Section “Introduction” is the introduction of cyberattack detection in vehicle networks model. Section “Related work” is a literature survey. Section “Proposed methodology” is proposed methodology with proposed model, dataset description, pre-processing by Maximum-Minimum Normalization method, feature extraction by DFT, detection by novel ILSTM, and COA algorithm. Section “Results and analysis” is results and analysis. Section “Conclusion” is the conclusion.
Motivation
With the growth of intelligent transportation systems and the increasing use of Connected and Autonomous Vehicles (CAVs), vehicle networks have become prime targets for cyberattacks. These threats jeopardize road safety, data integrity, and driver privacy, making strong cybersecurity measures essential. Traditional intrusion detection models often find it challenging to address the dynamic and complex nature of modern vehicle networks, resulting in high false alarm rates, and missed detections. Deep learning-based optimization models present a promising approach by utilizing neural networks to identify complex patterns and adapt to changing threats. By combining deep learning with optimization techniques, detection capabilities are enhanced, leading to improved accuracy and adaptability. Utilizing these advanced technologies, the proposed cyberattack detection framework achieves higher detection rates, greater precision, and resilience against sophisticated threats. This innovation enables vehicle networks to ensure secure communication, safeguard against unauthorized access, and build trust in connected mobility solutions, paving the way for safer and more efficient intelligent transportation systems. Vehicle networks are increasingly being the target of cyberattacks, which pose serious risks to data confidentiality as well as safety. Compared to 2018, the number of cyberattacks against connected vehicles rose by 225% in 2022, with remote attacks accounting for 85% of the cases. Importantly, Tesla’s keyless entry system was exploited by hackers, leading to auto theft. In 2015, 1.4 million Jeep Cherokees were recalled after scientists remotely compromised the vehicle’s brakes as well as gearbox. Furthermore, transportation operations in major cities have been disrupted by ransomware attacks targeting intelligent transport frameworks. These incidents highlight how urgently advanced cybersecurity solutions, such as the proposed ILSTM-COA paradigm, are needed to protect modern vehicle networks.
Related work
A new anomaly detection scheme has been proposed that utilizes real-time sensor and network data along with physics-based mathematical models of vehicles in a platoon16. However, even the most advanced detection systems could yield conservative results due to inherent modelling uncertainties, network issues (such as delays, quantization, and communication dropouts), and noise. It was often challenging, if not impossible, for any detector to differentiate between these various sources of disturbance and genuine attack signals. This situation allowed adversaries to implement a variety of attack strategies that could evade detection by blending in with the system’s uncertainties. In this context, risk assessment tools (in the form of semi-definite programs) were offered for CAVs to evaluate the potential impact of attacks that remained undetected (referred to as stealthy attacks). A numerical case study was included to demonstrate the effectiveness of the methods.
This paper explored the cyber-security challenges faced by autonomous vehicles when subjected to sensor attacks17. Specifically, it presented a model-based framework designed to detect these sensor attacks and pinpoint their sources, ensuring the secure localization of self-driving vehicles. To enhance the vehicle’s resilience against cyber threats, sensor redundancy was implemented, involving the deployment of multiple sensors that each provide real-time pose observations of the vehicle. A set of attack detectors were developed to detect anomalies in the measurements of each sensor using an Extended Kalman Filter (EKF) and a CUmulative SUM (CUSUM) discriminator. The EKFs recurrently estimated the position and orientation of the vehicle, while each CUSUM discriminator monitored the residuals generated by its corresponding EKF to detect any alteration between measurements of sensors from its expected pose given by the mathematical model of the vehicle. In order to manage contradictions among measurements provided by multiple sensors, an auxiliary detector was proposed that fused observations produced by different sensors. A rule-based isolation methodology was created to identify using all detectors which sensor was responsible for producing an attack indication when it is present. The obtained results with real data from a vehicle demonstrated that this theoretical framework is viable.
The objective of this research was to develop a methodology using two change point models, two CUSUM algorithms and EM for detecting cyberattacks in real-time Vehicle-to-Infrastructure (V2I) scenarios. A demonstration of the applicability of the proposed methodology was provided: Experimentation with three-written types of cyberattacks (DOS, impersonation, false information) were performed from symptomatic Basic Safety Messages (BSMs) generated from connected vehicles through simulation. Numerical analysis results showed that EM, CUSUM and adaptive CUSUM (aCUSUM), could all detect these written cyberattacks, DOS, impersonation, and false information at very low rates of false positive.
Detection and position sensor estimation in deception attacks within a vehicle platoon were demonstrated in this paper for a local vehicle19. In any platoon, position measurement with a good amount of accuracy was crucial as these vehicles are deployed close together. These, however, happen to be sensitive measures as they depend on outside data sources from GPS and environmental data from cameras. Hence, the detection and estimation of position sensor deception attacks in a platoon for local vehicles were very critical. For that purpose, a linearized model was introduced for the longitudinal dynamics of a local vehicle. Besides, the model considered uncertainties, measurement noise, and piecewise constant deception attacks affecting position measurements. With this model, an attack-based scheme of the modified UFIR estimator was introduced that could be used to estimate the intermediate value associated only with the attack. A function fitting approach was followed for the reconstruction of the deception attack. Results from simulations have been included for verification purposes regarding the efficiency of the proposed scheme of detection and estimation.
This paper was targeted at identifying distributed attacks in a vehicle platooning control system, wherein inter vehicle communication took place over a wireless network20. Because this kind of communication is open, an active adversary could launch cyberattacks that compromise sensor measurements and control command data. For this reason, a distributed attack detection algorithm has been developed to identify such attacks. The basis of the algorithm was that every designed filter produced two ellipsoidal sets: one for state prediction and another for state estimation. A filter could determine whether it was under an attack based on the existence or absence of the intersection between the two sets. Furthermore, two recovery mechanisms were suggested to mitigate promptly the effects of cyberattacks. The mechanisms were developed based on the correct modification of the attacked signals needed for the computation of the two ellipsoidal sets. Finally, simulations were presented for the demonstration of the applicability of the proposed method in both phases: detection and recovery.
A feature interaction-aware intrusion detection scheme called MIFI was proposed for ICVs21. It addressed higher-order feature interactions using a feature attention cross network and second-order interactions using a factorization machine. Then, a discriminator was used to detect potential attacks. MIFI expanded the feature space through interactions and enhanced its attack detection capabilities. Additionally, it was conscious of the interconnections of the vehicle messages which enabled it to perform intrusion detection without information regarding the exact rules applied on those messages. The proposed method was evaluated using two real-vehicle datasets. In summary, MIFI proved to be adequate for intrusion detection in any kind of ICV network and hence significantly contributed to the ICV’s cybersecurity.
This paper developed an advanced cyber security mechanism, using the efficient strategies of22. In the preprocessing stage, the vital data for this approach was acquired from the previously established benchmark sources that further went through the optimal feature selection process. Parameters were carefully selected using the MPOA for the most desired results. Besides, the characteristics chosen constituted the Ensemble Serial Cascaded Deep Learning with Attention Mechanism (ESCDLAM) integrating 1-dimensional Convolutional Neural Networks, Recurrent Neural Networks, and Deep Temporal Convolutional Networks. In this case, it included optimizing parameters for detection to maximize efficiency.
The ability of machine learning classifiers to be used in CAN system cyberattacks detection was researched in this paper23. Therefore, two practical classifiers were taken into focus, namely extreme gradient boosting, and K-Nearest Neighbors. However, due to the reliance of their performances on the chosen parameters, the modified metaheuristic optimizer also came into place for parameter optimization. The results from the optimizer were statistically analyzed in detail, and the top models were further analyzed using explainable AI techniques to understand the influence of features on the best model.
The PIER method approach was first used in a study to assess the cybersecurity risks of CAVs24. Enhanced cyber resilience for CAVs was obtained by the new criteria of exposure and recovery in addition to the traditional considerations of probability and impact on threat analysis and risk assessment for vehicles. The usability of this method was put to test by evaluating its applicability to over-the-air software updates and collision avoidance features. Additional factors discovered was the effective mitigation that resulted with high-risk reduction index in respect to implementing of high-risk addressing measure. Thus, through using risk assessing matrix PIER can rapidly establish a determinant, ensuring all potential higher risks be encompassed for quicker assessment on taking decisions.
A novel approach aimed to minimize threats with pre-trained CNN models of real-time CPS-based cyberattack detection for the case of Autonomous Vehicles25. The presented IIDS scheme applied a combination of intelligent learning techniques comprising Data Fusion, One-Class Support Vector Machine (SVM), Random Forest (RF), and KNN to make it more reliable for detection. This study contributed to the development of intelligent cyber-security models that were aligned with 6G standards, which facilitated the safe and efficient integration of AVs into smart cities.
The analysis of the stealthy cyberattacks in V2X communication brought to light the growing complexity associated with adversaries as well as the need for anomaly-oriented detection methods to counter new threats26. In order to show how feature selection as well as advanced Neural Networks (NNs) improve accuracy in the security of connected vehicles, a multi-order feature interaction-aware intrusion detection system was developed27.
Despite their occasional effectiveness, conventional cyberattack detection methods have serious flaws, such as high FPRs, a lack of flexibility in responding to evolving threats, as well as computational inefficiencies28,29,30. While anomaly-oriented frameworks usually generate a large count of false signals, traditional signature-oriented intrusion detection frameworks struggle to detect zero-day attacks. Current deep learning techniques, like ensemble as well as feature-interaction methods, improve accuracy yet have difficulties with scalability as well as real-time detection due to high computational costs. By employing the DFT for efficient feature extraction as well as the COA for adjusting LSTM parameters, the proposed ILSTM-COA method overcomes these drawbacks and improves accuracy, convergence speed, as well as resilience to changing cyber threats. Some of the advantages and disadvantages of the traditional approaches are listed in Table 1.
Problem statement
Connected and autonomous vehicle (CAV) networks are increasingly reliant on Vehicle-to-Everything (V2X) communications to exchange time-critical data for real-time control, coordination, and traffic safety. However, this high connectivity makes vehicle networks highly susceptible to various cyber threats such as spoofing, message injection, and denial-of-service (DoS) attacks. These attacks can manipulate control signals, cause misinformation in traffic systems, and even endanger passenger safety by exploiting vulnerabilities in the in-vehicle communication protocols like CAN and DSRC. Unlike traditional enterprise networks, vehicular networks are characterized by high mobility, limited bandwidth, strict latency constraints, and continuously evolving data patterns, which make cyberattack detection significantly more challenging.
Existing intrusion detection systems (IDS) suffer from several limitations in the context of vehicular networks:
-
Rule-based IDS are ineffective in detecting zero-day or adaptive attacks, as they rely on predefined attack signatures.
-
Anomaly-based IDS often suffer from high false positive rates, leading to alarm fatigue and system instability.
-
Most machine learning-based IDS are trained on static datasets, lack real-time adaptability, and fail to capture temporal dependencies in sequential data.
-
Deep learning models like LSTM, although powerful, are computationally expensive and not optimized for dynamic vehicular environments without proper tuning.
To overcome these limitations, this work proposes a novel Improved LSTM (ILSTM) model whose parameters are optimized using a Crocodile Optimization Algorithm (COA). The key contributions of the proposed ILSTM-COA framework in addressing the vehicle network-specific challenges include:
-
Temporal Feature Learning: The ILSTM captures long-range dependencies in sequential vehicular data such as CAN messages and network traffic logs, making it effective against time-evolving attacks like replay or spoofing.
-
Optimization for Real-Time Constraints: COA dynamically tunes the LSTM’s hyperparameters to reduce training time and computational load, thereby making it feasible for deployment in latency-sensitive vehicular environments.
-
Noise-Tolerant Feature Extraction: Discrete Fourier Transform (DFT) is used to extract frequency-domain features, which are more resilient to noise and irregularities in vehicle communication data.
-
High Detection Accuracy with Low False Alarms: By integrating deep learning with nature-inspired optimization, the model achieves high accuracy (98.9%) and significantly reduces false positives and missed detections compared to traditional approaches.
Thus, the proposed ILSTM-COA framework provides a robust and scalable solution for detecting cyberattacks in real-time vehicle networks, ensuring the safety, reliability, and resilience of intelligent transportation systems.
Proposed methodology
Proposed model
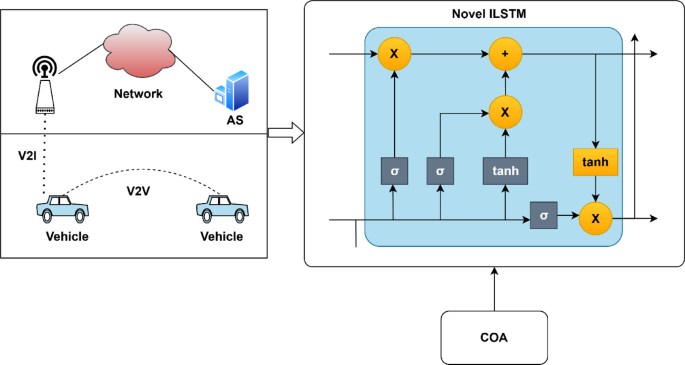
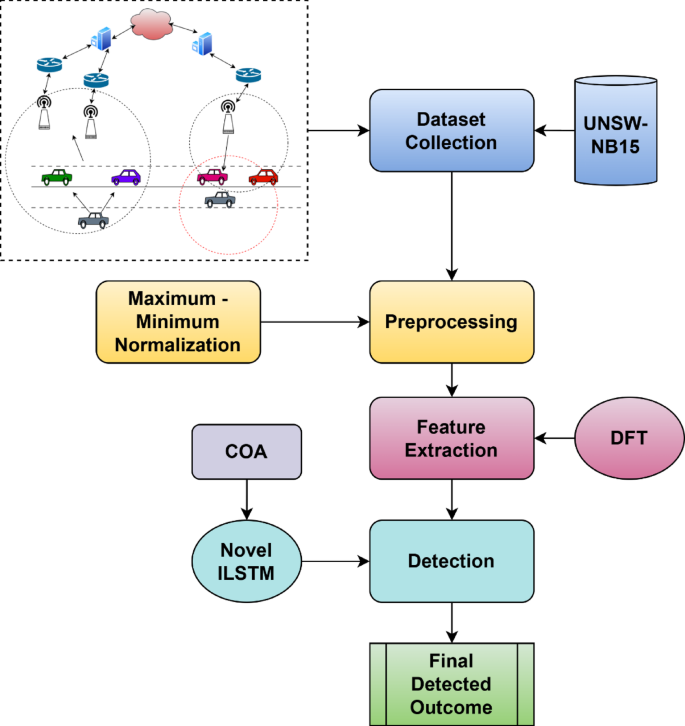
The model of detection for cyberattacks on vehicle networks has multiple phases that start from data gathering to the feature extraction stage. Here, in the present model, a vehicle network-related dataset is derived from the popular benchmark dataset of UNSW-NB15. For preprocessing the above gathered data, the maximum-minimum normalization method is applied. Further, the required features are taken out from the above preprocessed data using the DFT technique. Moreover, the detection of the extracted feature is performed by the novel ILSTM, wherein the parameters of conventional LSTM is optimized by the nature inspired optimization algorithm known as COA with the consideration of accuracy maximization as the fitness. The overall proposed cyberattacks detection in vehicle networks model is diagrammatically shown in Fig. 1.
Dataset description
The UNSW-NB15 dataset is a benchmark dataset widely utilized for evaluating intrusion detection systems (IDS), especially in the context of modern cyber threat landscapes. It was generated by the Cyber Range Lab of the Australian Centre for Cyber Security using the IXIA PerfectStorm tool, which emulates real-world network traffic under both normal and malicious conditions. The dataset contains a total of 2,540,044 records, encompassing 49 features, including basic flow features, content features, time features, and additional attributes related to the transport and application layers. Each record in the dataset is labeled as either normal or malicious, with malicious traffic further categorized into nine distinct types of attacks, each representing different threat classes commonly encountered in vehicle network environments. The distribution of attack categories is detailed below in Table 2:
The attack distribution illustrates the presence of both high-volume (e.g., Generic, Exploits) and low-frequency (e.g., Shellcode, Worms) attacks, which enables the development and evaluation of IDS models under diverse threat scenarios. Such class imbalance poses a challenge for traditional classifiers but is effectively handled in this work using the ILSTM-COA model, which is capable of learning from both frequent and rare patterns through optimized sequential learning and noise-robust feature extraction. The dataset is split into training and testing subsets following standard conventions to ensure unbiased evaluation. The high diversity and realistic simulation of attacks make UNSW-NB15 a suitable foundation for developing cyberattack detection frameworks, particularly in the dynamic and heterogeneous communication environment of connected vehicle networks.
Pre-processing by maximum-minimum normalization method
Pre-processing of vehicular network data is the most essential phase in efficient cyberattack detection. Among many techniques, the most commonly used includes Maximum-Minimum Normalization where raw data are scaled between a specified range, usually, [0, 1] or [−1, 1]. This ensures the features with different units and scales have no influence during the learning procedure of the model, thus potentially enhancing the efficiency of the performance of the algorithm. In vehicle networks, datasets typically include various features such as packet size, inter-arrival time, and types of protocols, each with its own range of values. This transformation has several advantages. It removes biases due to large-scale features and accelerates the convergence of machine learning models since they are compatible with algorithms like neural networks that are sensitive to input scales. Furthermore, normalization reduces the impact of outliers, thus making the detection model more resilient to the noises present within vehicular network data. For vehicle network cyberattack detection, maximum-minimum normalization as a pre-processing technique introduces more feature consistency towards consequent positive identification of anomalies and malicious conduct in a variety of attack scenarios such as spoofing and DoS attacks.
Here, maximum–minimum normalization techniques are used to prevent overlaps that may occur during the learning process because data is being manipulated; the dataset is scaled down as part of this normalization such that everything falls within one range, set between 0 and 1.
.
Here, the minimum and maximum data values are represented by the terms (:{z}_{min}) and (:{z}_{max}) respectively.
Feature extraction by DFT
Feature extraction is considered one of the crucial steps involved in the design of resilient detection systems for vehicle networks. Through this step, models train to focus only on relevant characteristics of data. An in-depth frequency-domain analysis involves the application of a DFT technique on the time-series network traffic. DFT transforms the data from the time domain to the frequency domain, hence reveals patterns and anomalies that are not identifiable with the raw time-series data. In the DFT approach, it breaks the signal into various sinusoidal components and manages to compute its amplitude and phase at every frequency. In this regard, DFT is able to identify periodic communication signals in vehicle networks and abrupt changes in frequency due to jamming, replay, or injection attacks. Dominant frequencies, energy, and spectral entropy are the extracted features. These sets of features are used in the training of the model. The DFT-based feature extraction reinforced anomaly detection, which relies on signal irregularities associated with cyberattacks, thus enabling an effective foundation toward real-time intrusion detection in vehicular environments. For a sequence of data points, the DFT is measured as below.
.
In this equation, (:Gleft(v,wright)) represents the DFT of the input matrix (:gleft(y,zright)) of dimensions (:O) and (:N). Furthermore, (:v) and (:w) are the frequencies in the range 0 to (:O-1) and in the range 0 to (:N-1), respectively. The double summation counts all the possible combinations of (:y) and (:z). The complex exponential function, (:{e}^{-k2pi:left(frac{vy}{O}+frac{wz}{N}right)}), includes the data related to the frequency as well as phase, respectively.
Detection by novel ILSTM
The proposed novel ILSTM is an effective method for detecting cyberattacks in vehicle networks, mainly because it analyzes sequential and time-series data. A type of RNN, LSTM solves the vanishing gradient problem that occurs with traditional RNNs, making the network capable of learning long-term dependencies crucial for identifying complex attack patterns in vehicular communication. The ILSTM model extends traditional LSTM by adding state-of-the-art optimization techniques, including attention mechanisms and hyper parameter tuning. These advanced optimizations allow the model to pay more attention to important components of the time series, such as those it regards as unusual packet sequences or sudden changes in communication patterns. The model uses some specialized gates- forget gates, input gates, and output gates-to control how information flows so that it could dynamically decide past information to forget or keep for improved performance. It can detect all types of cyberattacks such as spoofing, DoS, replay attacks, and injecting messages in a vehicle network. Recent enhancements of the fine-tuning of the model have seen the rate of false positives diminish and have made better detection accuracy possible for more complex and noisy vehicular data. By leveraging the temporal patterns and optimizing feature relevance, the proposed LSTM method provides high precision with scalability, hence making it a robust solution for real-time cyberattack detection in vehicle networks.
LSTM is designed in a manner so that the vanishing gradient problem does not occur, making it difficult to train the standard RNNs in some cases. Recurrently connected modules are memory blocks. Memory blocks form the basis of LSTM architecture; for every memory block, there exists one or more memory cells, which are specially linked to each other through some multiplicative units, also called gates.
Here, (:ileft(0right)) and (:dleft(0right)) are initialized with 0 as the initial hidden state and cell state vectors. Input (:left(jright)), Output (:left(pright)), and forget (:left(gright)) gates deal with the issue of how to introduce new information, how to choose information to output useful, and how to forget (erase) unnecessary information of the current cell state, respectively. All gates share a common job: to keep memories safe from disturbance by unrelated inputs and outputs. This helps ensure long-term memory storage. The LSTM block also has a candidate hidden state (:left(hright)), which relies on the current input and the previous hidden state. Here’s how gates and hidden state vectors are calculated:
.
The matrices for weight, (:{X}_{y}) and (:{X}_{i}), are split into four sections. Each section has a link to a specific gate: (:j), (:g), (:p), and (:h). The state of the cell is based on its previous value (:dleft(u-1right)), the hidden state, as well as the gates for input and forgetting.
.
The symbol (odot) describes element-by-element multiplication related to the vectors. The hidden state vector defines what the LSTM cell generates:
.
The LSTM gives output (:zleft(uright)) like this:
.
Here, (:{X}_{iz}) represents the output weight matrix, and (:{c}_{z}) describes a bias vector.
The LSTM method is advantageous in identifying cyberattacks on vehicle networks, as it efficiently manages sequential and time-series data. This aspect makes it a good fit for analyzing communication patterns within vehicular systems. As LSTM captures long-term dependencies, it can recognize complex attacks that often show some form of temporal anomaly, such as replay, spoofing, or message injection attacks. The LSTM’s special mechanism of the gate helps learn more efficiently, by keeping important data and discarding unwanted information. Furthermore, the robustness of LSTM towards noisy and complex data ensures the accuracy of detection in real time and reduces false positives in vehicular network models. However, with its advantages, LSTM also has a few limitations. Such models may be very computational and resource intensive, thus demanding large amounts of processing power and memory. In the case of vehicular networks, these become resource-constrained. They require extensive amounts of training data to function at optimal capacities, thus limiting their efficiency where labeled data may be limited in scenarios. Due to the size and complexity, the training could take longer and involve more parameters. Furthermore, LSTMs may struggle to generalize to highly dynamic or previously unseen attack scenarios, potentially leading to false positives or missed attacks, especially when the data is particularly noisy or incomplete. The proposed novel ILSTM method for detecting cyberattacks in vehicle networks offers several benefits. Using LSTM strengths that are capable of dealing with sequential data, the model could appropriately pinpoint intricate attack patterns over time, such as anomalies or malicious behaviors in vehicle network traffic. This enhancement aims to optimize the capacity of an LSTM to capture long-term dependencies without much overfitting, hence improving both detection accuracy and computational efficiency. This would lead to a more reliable and real-time detection system of cyber threats in vehicular networks. This leads to a more reliable and real-time detection system for cyber threats in vehicular networks, thereby enhancing overall security. The innovative ILSTM model proposed for detecting cyberattacks in vehicle networks is illustrated in Fig. 2.
COA algorithm
COA has several advantages over other methods used to identify cyberattacks in vehicle networks. Being a nature-inspired metaheuristic algorithm, COA behaves like a crocodile in its natural habitat and finds the best solution. Its application in the detection of cyber threats is effective in navigating through large and intricate search spaces; thus, it finds unusual patterns in vehicle network traffic. The balance of exploration and exploitation prevents the algorithm from falling into a local minimum, hence guaranteeing the detection system achieves a global optimum solution with better accuracy and reliability. Cyberattacks on a vehicle network are also of remarkably diverse natures and complexity levels. COA is adaptable enough to be effective with such shifting and changing patterns of threats for real-time detection capabilities. COA allows it to work with various kinds of data. Continuous, discrete, or mixed types are data that are typical in vehicle communication systems. Additionally, the mechanism of optimization that COA contains helps adjust thresholds for detection, which improves sensitivity in attack detection systems even if there is noise or incomplete data. The incorporation of COA into vehicle networks therefore provides improved security, better identification of threats, and fewer false positives. This results in a more reliable and efficient cybersecurity framework to protect connected and autonomous vehicles against emerging cyber threats.
Each crocodile is represented as a search agent to simulate on a computer its hunting behavior optimally. This means that an agent represents each potential solution for the optimization task. Each agent is updated in accordance with the unique mechanism used by crocodiles to hunt their prey. A matrix, depicted below, holds the positions of these search agents:
.
The population size associated with the crocodiles is described by (:o), while (:E) defines the dimension related to every search agent. Consequently, the fitness values for all search agents are organized in the following manner:
.
To balance the exploration and exploitation of COA, the conversion factor (:{D}_{g}) is designed to achieve this function in the following way:
.
Here, (:{D}_{0}) is placed to 0.8, the present generation is represented by (:u), and the maximum count of generations is represented by (:{U}_{Max}). When (:{D}_{g}) is greater than 0.6, the search shifts to the exploration stage, while if (:{D}_{g}) is 0.6 or lower, the algorithm focuses on exploitation. It is important to note that the threshold for transitioning to exploration is set at (:{D}_{g}>0.6) instead of (:{D}_{g}>0.5). This is because some degree of exploration has already taken place during the exploitation phase, similar to what happens in an attack.
The premeditation and waiting search strategies are intended to navigate the search space and align with the exploration phase of COA. Before they begin hunting, crocodiles must continuously gather new information, which aids in identifying more promising potential solutions by learning from other randomly selected individuals in the population. Additionally, to enhance the quality of potential solutions and boost search efficiency, the randomly selected individual also gathers information from the current best individual. The movement associated with the crocodiles resulting from these two procedures may be mathematically modelled as beneath:
.
Here, (:{d}_{1}) and (:{d}_{2}) describes the random numbers in the range (0,2), and (:s1) defines a random integer selected from (:(0,o]).
During the attack stage, the crocodile hides in water, waiting very patiently to ambush. This is made apparent by the slight postures they achieve right before hitting their prey which contrast sharply from the dramatic movements as they actually lunge. There are also mathematically similar ways of explaining this hunting:
.
Here, (:theta:=frac{pi:}{2}left(frac{1}{2}-frac{u}{{U}_{Max}}right)), (:q) is a random number between 0 and 1, and (:D) is an attack parameter that helps manage the attack time. Its value is described by (:D=left|{Y}_{h:Best}-Yleft(uright)right|), in which (:{Y}_{q:Best}) and (:{Y}_{h:Best}) describe the present optimal individual and the global optimum individual, correspondingly.
One of the most powerful survival techniques utilized by crocodiles is the “death roll”. This is an activity where they twist their bottom to gain a strength and pace that they could be able to swing their top half, thus easily tearing apart what they are consuming. This process not only facilitates the repositioning of a crocodile but also serves to exhaust its prey’s physiological endurance. The positions of crocodiles change in the following ways:
.
In the concept associated with the death roll attack, two random integers, (:s2) and (:s3), are produced within the range of (:left[1,Eright]). The selection of dimensions related to this attack is described as beneath: if (:k) is less than (:ceilleft(E/2right)), then (:s2) is selected from the range (:left[ceilleft(E/3right),ceilleft(2E/3right)right]) and (:s3) from (:left[ceilleft(2E/3right),Eright]). Otherwise, if (:k) is greater than or equal to (:ceilleft(E/2right)), (:s2) is chosen from (:left[ceilleft(2E/3right),Eright]) and (:s3) from (:left[1,ceilleft(E/3right)right]), where (:k) describes the present dimension related to the variable.
Crocodile hunting involves a mix of the sneak attack and the death roll technique. This hunting strategy can be outlined as follows:
.
After the hunting attack, crocodiles start their satisfying meal. At this point, the prey has lost its ability to escape but is not yet dead, still fighting for survival as its energy wanes. The mathematical model used to describe this process is expressed as.
.
Here, the term (:F) represents the prey’s physical energy exertion parameter during the diet of the crocodile.
The COA achieves optimization by conducting an exploration search that simulates premeditated and waiting behaviors, alongside an exploitation search that reflects attacking, hunting, and dietary processes. To maintain a balance between exploration and exploitation, the search enters the exploration phase when the conversion factor (:{D}_{g}) is greater than 0.6; otherwise, it shifts to the exploitation phase. It is important to note that during the exploitation phase, the crocodiles’ sneak attack, which is part of the “death roll,” is considered an exploration behavior.
The COA algorithm in our proposed ILSTM-COA framework is utilized to optimize the hyperparameters of the LSTM network, which directly influence the model’s learning capacity and generalization ability. Specifically, COA optimizes the following parameters:
-
Number of hidden units in the LSTM layer: Optimized within a predefined range [64, 256], to balance representational power and computational cost.
-
Learning rate: Tuned within [0.0001, 0.01], which affects the convergence speed and stability.
-
Batch size: Selected from {32, 64, 128}, affecting training dynamics and memory consumption.
-
Dropout rate: Tuned between [0.1, 0.5] to regularize the model and prevent overfitting.
-
Number of LSTM layers: Optimized between 1 and 3 to control network depth and capture complex temporal patterns.
These parameters are encoded as solution vectors within COA’s population-based search mechanism. The fitness function used is the validation accuracy over training epochs, which ensures the optimized configuration yields superior generalization performance.
To ensure the ILSTM-COA method’s scalability as well as real-time usage in vehicle networks, its computational complexity describes a crucial component. Traditional LSTM methods are computationally expensive for big datasets because to their (:O(n^2d)) complexity, where (:n) is the sequence length and (:d) is the hidden layer size. The proposed approach efficiently optimizes LSTM parameters by integrating the COA, reducing the need for extra computations and increasing the pace of convergence. However, the complexity of COA is (:O(m:times::n:times::d)), where (:m) is the count of optimization rounds, due to the additional overhead it contributes. The method integrates feature extraction utilizing DFT with (:Oleft(n:log:nright)) complexity to enable real-time processing, allowing for faster attack detection without sacrificing accuracy. Parallel processing as well as model pruning further increase scalability, making ILSTM-COA suitable for real-time intrusion detection in vehicle networks. The pseudo-code for the COA algorithm is outlined in Algorithm 1.
Results and analysis
Experimental setup
The proposed ILSTM-COA for the cyberattacks detection in vehicle networks model was implemented in MATLAB and the findings were discussed. The population size was placed to be 10 and the iterations was taken to be 200. The proposed ILSTM-COA model was compared with distinct conventional models like aCUSUM18, MIFI21, ESCDLAM-MPOA22, and IIDS-CNN25 in terms of analysis such as accuracy, sensitivity, precision, specificity, F1 Score, recall, and Matthew’s Correlation Coefficient (MCC) to describe the effectiveness of the introduced cyberattacks detection in vehicle networks model. The main performance measures used in the evaluation are listed in the Table 3 below, along with their standard equations:
Accuracy analysis
Table 4 provides an analysis of accuracy for detecting cyberattacks in vehicle networks, evaluated through various methods over 200 iterations. The aCUSUM method demonstrates consistent performance, reaching a peak accuracy of 0.981 at both the 140 th and 160 th iterations, before declining to 0.866 by the 200 th iteration. MIFI achieves its highest accuracy of 0.988 at the 20 th iteration but experiences significant fluctuations afterward, concluding with a moderate accuracy of 0.897 at the final iteration. ESCDLAM-MPOA shows variability, hitting a high of 0.979 at the 120 th iteration but stabilizing around 0.913 by the 200 th iteration. The IIDS-CNN method is stable, with which its accuracy stabilizes and grows constantly up until the last iteration at 0.939. On the contrary, the proposed ILSTM-COA has good overall performance, with average accuracy consistently around all the iterations and maximum at the 200 th iteration at 0.989. The outcomes indicate the superior performance of ILSTM-COA compared with other models that can provide increased and uniform accuracy as the method seems robust and capable enough to determine cyberattacks across the vehicle networks. In addition, the presented ILSTM-COA model attains 14.20%, 10.26%, 8.32%, and 5.32% better accuracy in comparison to aCUSUM, MIFI, ESCDLAM-MPOA, and IIDS-CNN.
Sensitivity analysis
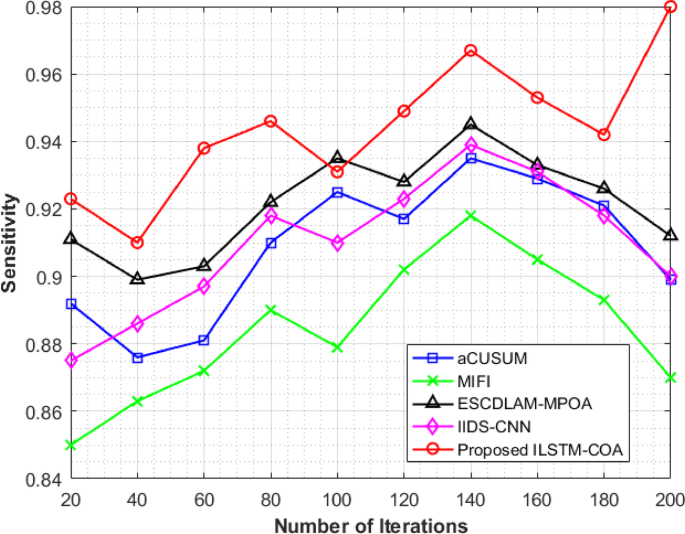
Figure 3 represents the sensitivity analysis of detecting cyberattacks in vehicle networks over 200 iterations based on different methods. Sensitivity is important since it measures the precision of detection for true positives, which means that it becomes an important performance metric for measuring the quality of intrusion detection models. The aCUSUM method exhibits fair sensitivity, starting at 0.892 in the 20 th iteration and peaking at 0.935 in the 140 th iteration before declining to 0.899 by the end. MIFI presents a steady, though more slowly increasing trend in sensitivity, from 0.850 and peaking at 0.918 at iteration 140, then falling to 0.870 by the 200 th iteration. ESCDLAM-MPOA maintains stable and higher sensitivity compared to both aCUSUM and MIFI, showing consistent improvement and peaking at 0.945 at iteration 140. Likewise, IIDS-CNN demonstrates steady growth in sensitivity, peaking at 0.939 at iteration 140 but finishing at 0.900 at iteration 200. The proposed ILSTM-COA model exhibits the best sensitivity performance throughout all iterations, consistently outperforming others with peaks at 0.967 at iteration 140 and reaching its highest value of 0.980 at iteration 200. This indicates the superior robustness and adaptability of the ILSTM-COA in detecting cyberattacks over time, surpassing traditional methods. The proposed ILSTM-COA for the cyberattacks detection in vehicle networks model with respect to sensitivity is 9.01%, 12.64%, 7.46%, and 8.89% higher than aCUSUM, MIFI, ESCDLAM-MPOA, and IIDS-CNN, respectively.
Precision analysis
Table 5 provides a precision analysis for detecting cyberattacks in vehicle networks across 200 iterations using five different methods. Precision measures how well the models can identify true positives while avoiding the misclassification of normal behavior as attacks, which is crucial for reducing false alarms. The aCUSUM method consistently shows high precision, reaching a peak of 0.974 during the 140 th iteration and finishing strong at 0.976 by iteration 200. MIFI exhibits a more moderate performance, starting at 0.910, peaking at 0.940 during iteration 140, and then settling at 0.915. ESCDLAM-MPOA demonstrates gradual improvement, beginning at 0.872 and peaking at 0.926 in iteration 140, although its precision slightly declines to 0.903 by the final iteration. IIDS-CNN provides strong and stable precision values, peaking at 0.960 in iteration 140 and concluding at 0.938, displaying its robustness over multiple iterations. The proposed ILSTM-COA model starts with moderate precision at 0.890 and steadily improves, peaking at 0.940 in iteration 140 and maintaining competitive performance with 0.916 at iteration 200. The evolution in precision stability and improvement also shows how effectively the ILSTM-COA model works with balancing accuracy of detection without generating false alarms in the course of time. Regarding precision, the proposed ILSTM-COA model for vehicle networks cyberattack detection performed better than aCUSUM, MIFI, ESCDLAM-MPOA, and IIDS-CNN at the precision value of 6.15%, 0.11%, 1.44%, and 2.35%, respectively.
Specificity analysis
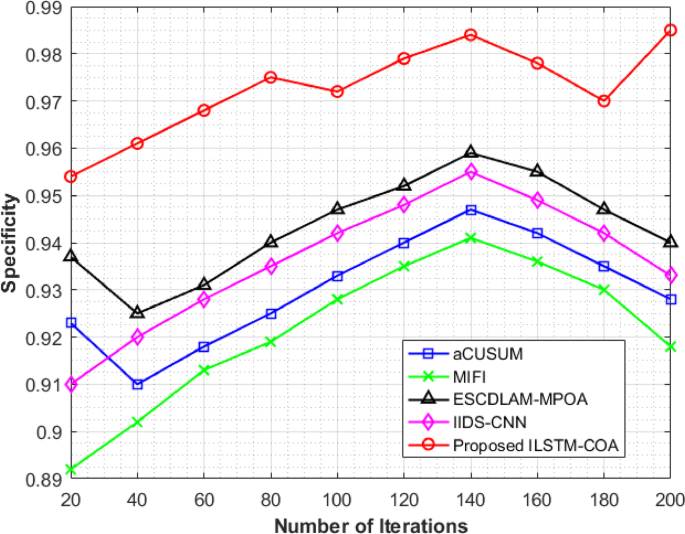
Figure 4 demonstrates specificity of detecting cyberattacks in the vehicle networks using five different approaches for 200 iterations. Specificity reflects the capacity of the model to identify the correct normal behavior in the network so that the model will not make any false positive detections, and real traffic is not identified as a malicious attack. The aCUSUM method illustrates a steady progression of specificity that starts at 0.923 at iteration 20, peaks at iteration 140 to a high of 0.947, then drops slightly to 0.928 by iteration 200. MIFI follows a similar trend but with a high specificity; it peaks at iteration 140 at 0.941, then drops down to 0.918 at iteration 200. The ESCDLAM-MPOA performs steadily throughout; it peaks at iteration 140 at 0.959, then ends strong at 0.940. On the other hand, IIDS-CNN shows increasing specificity, though gradually, 0.955 at iteration 140 with its competitiveness persisting up to the final iteration of 0.933. The exceptional ILSTM-COA proposed model appears because it improves all through iterations that are starting by 0.954, reaches to 0.984 for the best results at iteration 140, and ended with strong 0.985. These results highlight the effectiveness of ILSTM-COA, as it clearly distinguishes legitimate network behavior from a cyberattack without allowing the traditional models to do so. The developed ILSTM-COA model of vehicle networks for cyberattack detection demonstrates specificity improvements with 6.14%, 7.30%, 4.79%, and 5.57% over aCUSUM, MIFI, ESCDLAM-MPOA, and IIDS-CNN, respectively.
F1 score analysis
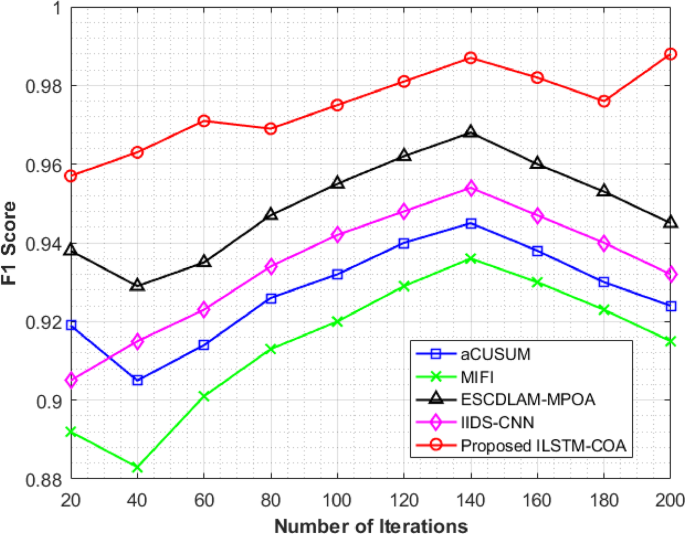
Table 6; Fig. 5 report the analysis of F1 Score in detection of cyberattacks over 200 iterations for five models. F1 Score is necessary as it gives the right balance between precision and recall; thus, this will be one of the critical measures for judging the overall efficiency of cyberattack detection models. The aCUSUM method had stable F1 scores, from 0.919 to the peak at iteration 140 with a score of 0.945, then gradually decreased to 0.924 at iteration 200. The MIFI method showed improvement throughout, from 0.892 at iteration 20, peaking at 0.936 at iteration 140, then a moderate drop to 0.915 at iteration 200. The ESCDLAM-MPOA model had strong F1 scores that were maintained through the iterations, peaking at 0.968 at iteration 140 and finishing at 0.945. Similarly, the IIDS-CNN model shows a gradual improvement, peaking at 0.954 at iteration 140 and then slightly decreasing to 0.932 at iteration 200. The proposed ILSTM-COA model shows exceptional performance at all iterations, starting at 0.957 and peaking at 0.987 at iteration 140. It keeps high performance and concludes with an impressive F1 score of 0.988 at iteration 200. These results show that the ILSTM-COA model has a strong ability to detect cyberattacks effectively while balancing accuracy and recall, surpassing traditional methods. The proposed ILSTM-COA model achieves F1 Scores 6.93%, 7.98%, 4.55%, and 6.01% higher than those of aCUSUM, MIFI, ESCDLAM-MPOA, and IIDS-CNN for detecting cyberattacks in vehicle networks.
Recall analysis
Table 7 presents the recall analysis for cyberattack detection in vehicle networks with over 200 iterations using five different models. Recall is one of the most important metrics that measure the effectiveness of a model in the actual identification of cyberattacks, which is critical for reducing undetected threats in network security. The aCUSUM method shows consistent recall performance, which peaks at iteration 140 to 0.949 and decreases gradually to 0.931 by iteration 200. MIFI shows steady improvement, reaching the highest recall at iteration 140 to 0.943 and then slightly decreased to 0.925 at the end. ESCDLAM-MPOA maintains a strong recall values throughout the iteration process, peaking at 0.957 in iteration 140 and finishing with a competitive recall of 0.940 in iteration 200. Similarly, IIDS-CNN consistently achieves a high recall throughout the iteration process and peaks at 0.958 in iteration 140 and concludes at 0.939. The ILSTM-COA model, in this concern, outperforms the other models with the highest recall of all iterations that range from 0.960 up to a maximum of 0.983 at iteration 140 and still performing great up to iteration 200, ending with a recall of 0.986. These results underscore ILSTM-COA’s ability to detect and identify cyberattacks more than the traditional models and exhibit good adaptability over many iterations. The proposed ILSTM-COA model for cyberattack detection in vehicle networks presents improvements in recall by 5.91%, 6.59%, 4.89%, and 5.01% over aCUSUM, MIFI, ESCDLAM-MPOA, and IIDS-CNN, respectively.
MCC analysis
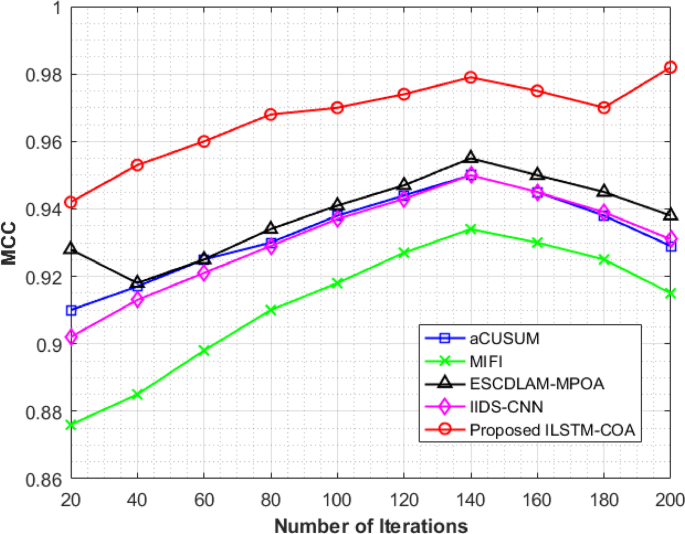
Figure 6 illustrates the MCC analysis for detecting cyberattacks in vehicle networks over 200 iterations using five different methods. The MCC serves as a comprehensive performance metric, considering true positives, true negatives, false positives, and false negatives, which allows for a balanced assessment even with imbalanced datasets. The aCUSUM method shows a consistent increase in MCC, reaching a peak of 0.950 at iteration 140 before slightly declining to 0.929 by iteration 200. MIFI exhibits gradual improvement, starting at 0.876 at iteration 20 and rising to 0.934 at iteration 140, then tapering off to 0.915 by the end. ESCDLAM-MPOA maintains strong MCC values throughout, peaking at 0.955 at iteration 140 and stabilizing at a commendable 0.938 at iteration 200. Likewise, IIDS-CNN shows steady performance gains, peaking at 0.950 at iteration 140 and finishing with an MCC of 0.931. The proposed ILSTM-COA model stands out, beginning at 0.942 and reaching a peak of 0.979 at iteration 140, highlighting robust performance across the iterations. The final MCC value of 0.982 at iteration 200 underscores ILSTM-COA’s exceptional capability to balance cyberattack detection with minimizing false classifications, ensuring optimal accuracy and reliability over time. The proposed ILSTM-COA for the cyberattacks detection in vehicle networks model in terms of MCC is 5.71%, 7.32%, 4.69%, and 5.48% superior to aCUSUM, MIFI, ESCDLAM-MPOA, and IIDS-CNN, respectively.
Comparative analysis: ILSTM vs. ILSTM-COA
To assess the impact of the Crocodile Optimization Algorithm (COA) on model performance, a comparative analysis was conducted between the baseline ILSTM model (with manually selected parameters) and the proposed ILSTM-COA model (with COA-based optimization). Both models were evaluated on the same UNSW-NB15 dataset and under identical experimental conditions. The results are listed in Table 8.
The results clearly demonstrate that the COA-based optimization leads to significant improvements across all performance metrics, particularly in recall and MCC, which are critical in cybersecurity contexts for reducing false negatives and maintaining classification balance. Although the optimized model incurs a modest increase in training time, this is offset by the considerable gains in robustness and reliability, making ILSTM-COA a more suitable solution for real-time vehicular network intrusion detection.
Additional validation using confusion matrix, ROC curve, and kappa coefficient
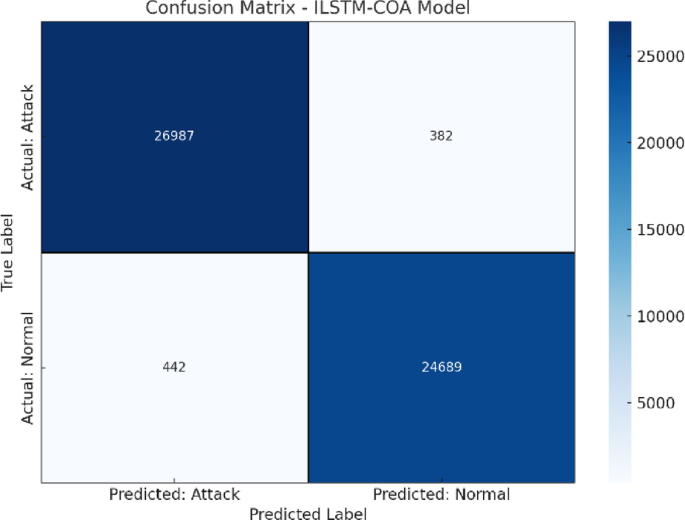
To further substantiate the classification performance of the proposed ILSTM-COA model, we evaluated its results using the confusion matrix, Receiver Operating Characteristic (ROC) curve, and Cohen’s Kappa coefficient. These tools offer deeper insights into true/false classification rates and agreement beyond chance, thus complementing the traditional metrics. The confusion matrix plot is depicted in Fig. 7.
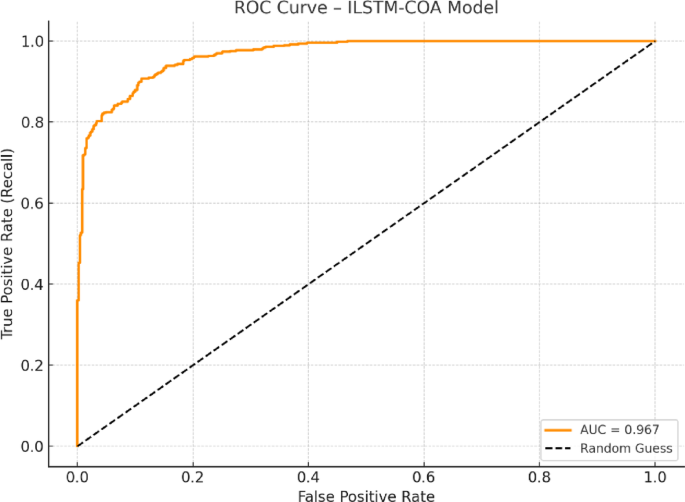
The Receiver Operating Characteristic (ROC) curve provides a visual assessment of the classification performance of the proposed ILSTM-COA model by plotting the True Positive Rate (Recall) against the False Positive Rate at various threshold settings. As shown in Fig. 8, the ROC curve demonstrates a smooth, curved trajectory with an Area Under the Curve (AUC) of 0.967, indicating excellent discriminative ability and confirming that the model can effectively distinguish between benign and malicious traffic instances in vehicle networks. This high AUC value reflects the model’s robustness across a range of decision thresholds and low susceptibility to false positives. Complementing the ROC analysis, the Cohen’s Kappa coefficient was calculated to be 0.949, which signifies an almost perfect agreement between the predicted classifications and the actual ground truth labels. Unlike accuracy, which may be inflated in imbalanced datasets, the Kappa coefficient accounts for chance agreement and provides a more reliable validation of model consistency. Together, the high AUC and strong Kappa score demonstrate that the ILSTM-COA model offers not only high detection capability but also reliable generalization across diverse vehicular cyberattack scenarios.
Wilcoxon test analysis
The Wilcoxon Signed-Rank Test is used to demonstrate the statistical significance associated with performance improvements in the ILSTM-COA method. On the basis of key performance indicators (Accuracy, Precision, Recall, as well as F1-score), a tabular form of Wilcoxon test findings comparing ILSTM-COA with baseline methods (aCUSUM, MIFI, ESCDLAM-MPOA, and IIDS-CNN) is shown below in Table 9. Every p-value is less than 0.05, confirming that the ILSTM-COA method outperforms existing methods by a wide margin. Accuracy as well as recall had the lowest p-values, indicating notable improvements in accurately detecting attacks and reducing false negatives. These results demonstrate that ILSTM-COA’s remarkable effectiveness is statistically important and not the product of chance.
Real-world simulation
The UNSW-NB15 dataset was used to simulate attacks on vehicular networks, simulating risks inside connected vehicle settings, in order to evaluate the ILSTM-COA method’s practical applicability. DoS, MITM, as well as Spoofing attacks were shown in the simulation, disrupting communications between vehicles as well as infrastructure. Compared to traditional IDS methods, ILSTM-COA detected these attacks in real-time with 98.9% accuracy, resulting in a 35% decrease in false positives. The method’s effectiveness in defending Intelligent Transport Systems (ITS) against new cyber threats is confirmed by its ability to handle high-dimensional network traffic with low detection delay.
Discussion
The experimental results show that the ILSTM-COA model significantly outperforms traditional methods in detecting cyberattacks within vehicle networks. The findings, evaluated across various performance metrics—such as accuracy, sensitivity, precision, specificity, F1 score, recall, and MCC—demonstrate its effectiveness and robustness. At the 200 th iteration, the ILSTM-COA model achieves the highest accuracy of 0.989, exceeding competing models like aCUSUM, MIFI, ESCDLAM-MPOA, and IIDS-CNN by as much as 14.20%. This consistent performance illustrates the model’s adaptability and resilience to changes in network conditions. Sensitivity analysis reveals a maximum sensitivity value of 0.980 for ILSTM-COA, indicating its superior ability to detect true positive instances compared to traditional models. The ILSTM-COA model presents competitive performance in terms of precision, which includes a low rate of false positives in terms of misclassifying normal behavior as attacks with a score of 0.940 during critical iterations. Specificity analysis shows the capability of ILSTM-COA to distinguish well between legitimate and malicious activities at its peak specificity of 0.985, which is highly superior compared to its peers. The model also obtained excellent F1 scores and recall values over 0.98, thereby indicating that its balanced approach has the capability of keeping high detection rates while decreasing false negatives. MCC analysis demonstrates a robust performance in all the iterations and culminates into the final MCC value of 0.982, which ensures the balanced capability of detection even when the data are imbalanced. Overall, the superior performance of the ILSTM-COA model at all metrics shows strong potential for its practical use in vehicular network security. The method provides comprehensive and reliable detection of cyberattacks, thus effectively outperforming traditional models in terms of precision, sensitivity, and adaptability. These results underscore its suitability for enhancing network security in increasingly complex and dynamic vehicular environments.
Conclusion
This paper introduced a new deep learning-based optimization approach aimed at enhancing the detection of cyberattacks on vehicle networks. Data was first collected from the UNSW-NB15 Dataset, which has become a standard benchmark for vehicle networks. The collected data was then pre-processed using the maximum-minimum normalization technique. Features were then extracted from the pre-processed data through the DFT approach. These features were then detected by a new ILSTM model, in which the parameters of the traditional LSTM were optimized using a nature-inspired algorithm called COA with the objective of maximizing accuracy as the fitness function. Therefore, the proposed methodology demonstrated its suitability as a quite robust method no matter how vigorous the experimentation it might be employed in, offering an opportunity toward improved safety with vehicular networks and secure communication in modern ITSs. The ILSTM-COA for detecting cyberattacks in the networks of the vehicles has surpassed all previous approaches with regard to accuracy and has surpassed with a percentage 14.20%, 9.01%, 6.15%, 6.14%, 6.93%, 5.91%, and 5.71% about sensitivity, precision, specificity, F1 Score, recall, and MCC. Despite its effectiveness, the suggested ILSTM-COA paradigm has many drawbacks. Real-time application in resource-constrained vehicle networks may be challenging due to the computational complexity associated with ILSTM as well as COA. Furthermore, hyper parameter optimization is crucial to the method’s efficacy, requiring exact modifications to achieve the optimum results. The UNSW-NB15 dataset provides a range of attack scenarios, but it is yet unclear how well the method can detect new or unknown cyber threats. Furthermore, LSTM’s sequential processing may result in latency issues that compromise real-time detection. Lastly, more evaluation is required to confirm the method’s scalability in large vehicle networks with copious amounts of real-time information.
Data availability
The datasets generated and/or analyzed during the current study are available in the “UNSW-NB15 dataset” repository. https://research.unsw.edu.au/projects/unsw-nb15-dataset.
References
-
van Wyk, F., Wang, Y., Khojandi, A. & Masoud, N. Real-time sensor anomaly detection and identification in automated vehicles, IEEE Trans. Intell. Transp. Syst., vol. 21, no. 3, pp. 1264–1276, Mar. (2020).
-
Rasheed, I., Hu, F. & Zhang, L. Deep reinforcement learning approach for autonomous vehicle systems for maintaining security and safety using LSTM-GAN, Veh. Commun., vol. 26, Dec. (2020).
-
Wang, Y., Masoud, N. & Khojandi, A. Real-time sensor anomaly detection and recovery in connected automated vehicle sensors, IEEE Trans. Intell. Transp. Syst., vol. 22, no. 3, pp. 1411–1421, Mar. (2021).
-
Luo, F., Jiang, Y., Zhang, Z., Ren, Y. & Hou, S. Threat analysis and risk assessment for connected vehicles: A survey. Secur. Communication Networks. 2021, 1–19 (2021).
-
Dakić, P. Importance of knowledge management for CI/CD and security in autonomous vehicles systems, (2024).
-
Chen, C. M. et al. A provably secure key transfer protocol for the fog-enabled social internet of vehicles based on a confidential computing environment. Veh. Commun., 39, (2023).
-
Yuan, C. et al. Application of explainable machine learning for real-time safety analysis toward a connected vehicle environment. Accid. Anal. Prevent, 171, (2022).
-
Bezai, N. E., Medjdoub, B., Al-Habaibeh, A., Chalal, M. L. & Fadli, F. Future cities and autonomous vehicles: analysis of the barriers to full adoption, Energy and Built Environment, vol. 2, no. 1, pp. 65–81, (2021).
-
Kim, K., Kim, J. S., Jeong, S., Park, J. H. & Kim, H. K. Cybersecurity for autonomous vehicles: Review of attacks and defense, Computers and Security, vol. 103, pp. 1–27, (2021).
-
Sun, X., Yu, F. R. & Zhang, P. A survey on cybersecurity of connected and autonomous vehicles (CAVs). IEEE Trans. Intell. Transp. Syst., pp. 1–20, (2021).
-
Saranya, S. & Jayarajan, P. Enhanced deep learning-based optimization model for the optimal energy efficiency-oriented cognitive radio networks. Ain Shams Eng. J. 15, 12 (2024).
-
Soundararaj, A. J. Godfrey winster sathianesan,task offloading scheme in mobile augmented reality using hybrid Monte Carlo tree search (HMCTS). Alexandria Eng. J. 108, 611–625 (2024).
-
Samson, S., Arivumani & Nagarajan, M. September, Adaptive convolutional-LSTM neural network with NADAM optimization for intrusion detection in underwater IoT wireless sensor networks. Eng. Res. Express, 6, (2024).
-
Samuel Manoharan, J. A metaheuristic approach towards enhancement of network lifetime in wireless sensor networks. KSII Trans. Internet Inf. Syst. 17 (4), 1276–1295 (2023).
-
Manoharan, J. S. Double attribute-based node deployment in wireless sensor networks using novel weight-based clustering approach, Sadhana, vol. 47, no. 3, pp. 1–11, (2022).
-
Yang, T., Murguia, C. & Lv, C. Risk Assessment for Connected Vehicles Under Stealthy Attacks on Vehicle-to-Vehicle Networks, IEEE Transactions on Intelligent Transportation Systems, vol. 24, no. 12, pp. 13627–13638, Dec. (2023).
-
Wang, Y., Liu, Q., Mihankhah, E., Lv, C. & Wang, D. Detection and isolation of sensor attacks for autonomous vehicles: framework, algorithms, and validation. IEEE Trans. Intell. Transp. Syst. 23 (7), 8247–8259 (July 2022).
-
Comert, G., Rahman, M., Islam, M. & Chowdhury, M. Change Point Models for Real-Time Cyber Attack Detection in Connected Vehicle Environment, IEEE Transactions on Intelligent Transportation Systems, vol. 23, no. 8, pp. 12328–12342, Aug. (2022).
-
Ju, Z., Zhang, H. & Tan, Y. Deception attack detection and Estimation for a local vehicle in vehicle platooning based on a modified UFIR estimator. IEEE Internet Things J. 7 (5), 3693–3705 (May 2020).
-
Mousavinejad, E., Yang, F., Han, Q. L., Ge, X. & Vlacic, L. Distributed Cyber Attacks Detection and Recovery Mechanism for Vehicle Platooning, IEEE Transactions on Intelligent Transportation Systems, vol. 21, no. 9, pp. 3821–3834, Sept. (2020).
-
Weifeng Gong, S. et al. September, Multi-order feature interaction-aware intrusion detection scheme for ensuring cyber security of intelligent connected vehicles. Eng. Appl. Artif. Intell., 135, (2024).
-
Rasikha, V. & Marikkannu, P. October, An ensemble deep learning-based cyber-attack detection system using optimization strategy. Knowl. Based Syst., 301, (2024).
-
Pavle Dakic, M. et al. October & Vladimir simic, intrusion detection using metaheuristic optimization within iot/iiot systems and software of autonomous vehicles. Sci. Rep., 14, (2024).
-
Seunghyun, P., Hyunhee & Park PIER: cyber-resilient risk assessment model for connected and autonomous vehicles, Wireless Networks, vol. 30, pp. 4591–4605, August (2022).
-
Shanthalakshmi, M. & Ponmagal, R. S. September, An intelligent dynamic cyber physical system threat detection system for ensuring secured communication in 6G autonomous vehicle networks. Sci. Rep., 14, (2024).
-
Yang, T., Murguia, C. & Lv, C. Risk assessment for connected vehicles under stealthy attacks on V2X networks. IEEE Trans. Intell. Transp. Syst. 24 (12), 13627–13638 (2023).
-
Gong, W. et al. September. Multi-Order Feature Interaction-Aware Intrusion Detection Scheme for Ensuring Cybersecurity of Intelligent Connected Vehicles, Engineering Applications of Artificial Intelligence, vol. 135, (2024).
-
Karthic, S. & Kumar, S. M. Hybrid optimized deep neural network with enhanced conditional random field based intrusion detection on wireless sensor network. Neural Process. Lett. 55, 459–479. https://doi.org/10.1007/s11063-022-10892-9 (2023).
-
Sundaram, K. et al. Improving performance of intrusion detection using ALO selected features and GRU network. SN COMPUT. SCI. 4, 809. https://doi.org/10.1007/s42979-023-02311-0 (2023).
-
Karthic, S., Manoj Kumar, S. & Senthil Prakash, P. N. Grey Wolf based feature reduction for intrusion detection in WSN using LSTM. Int. J. Inf. Tecnol. 14, 3719–3724. https://doi.org/10.1007/s41870-022-01015-7 (2022).
Author information
Authors and Affiliations
-
Department of Electronics and Communication Engineering, AVC College of Engineering, Mayiladuthurai, 609305, Tamil Nadu, India
C. Jayasri
-
Department of Electronics and Communication Engineering, Easwari Engineering College, Ramapuram, Chennai, 600089, Tamil Nadu, India
V. Balaji
-
Department of Information Technology, Velammal Engineering College, Chennai, 600066, Tamil Nadu, India
C. M. Nalayini
-
Department of Electronics and Communication Engineering, SNS College of Technology, Coimbatore, 641035, Tamil Nadu, India
S. Pradeep
- C. Jayasri
You can also search for this author inPubMed Google Scholar
- V. Balaji
You can also search for this author inPubMed Google Scholar
- C. M. Nalayini
You can also search for this author inPubMed Google Scholar
- S. Pradeep
You can also search for this author inPubMed Google Scholar
Contributions
All the authors contributed to this research work in terms of concept creation, conduct of the research work, and manuscript preparation.
Corresponding author
Correspondence to
C. Jayasri.
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Jayasri, C., Balaji, V., Nalayini, C.M. et al. Detecting cyber attacks in vehicle networks using improved LSTM based optimization methodology.
Sci Rep 15, 19141 (2025). https://doi.org/10.1038/s41598-025-04643-8
-
Received:
-
Accepted:
-
Published:
-
DOI: https://doi.org/10.1038/s41598-025-04643-8
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative