A Look at ENISA’s NIS360 Cyber Risk Quadrant
In an increasingly volatile threat landscape, European cybersecurity strategies are being put to the test. The war in Ukraine, heightened geopolitical tensions, and growing state-sponsored cyber operations have underscored the fragility of essential systems. The EU’s collective cyber resilience depends not only on strong individual actors, but on shared capacity across sectors that sustain daily life. ENISA’s 2024 ENISA NIS360 quadrant challenges us to confront a difficult truth: some of Europe’s most critical sectors remain dangerously underprepared for modern cyber threats.

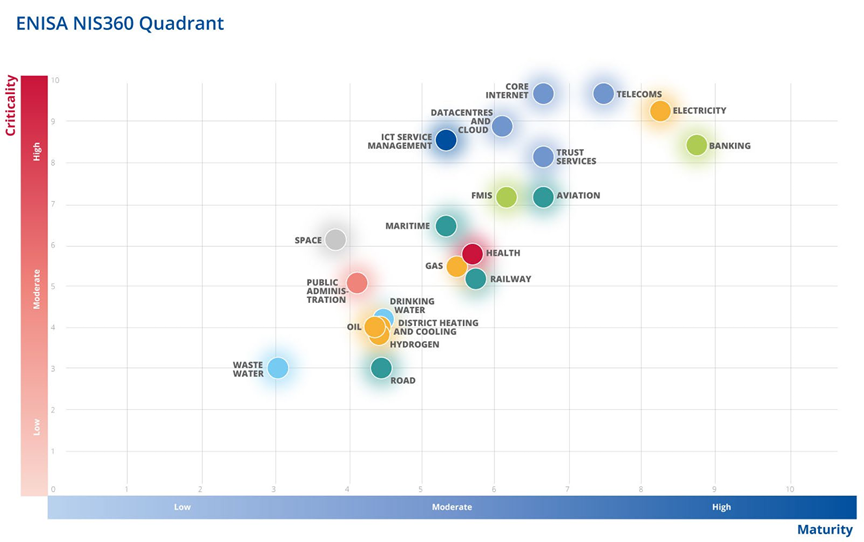
The ENISA NIS360 quadrant maps 21 sectors along two axes—cybersecurity maturity and societal criticality—revealing which ones are falling behind and why that matters.
It’s important to understand that this is a pan-European assessment. The quadrant aggregates data from multiple sources across the EU to reflect cross-sectoral patterns, not the exact maturity level of a sector in each Member State. ENISA explicitly notes that cybersecurity maturity varies significantly between countries and even within the same sector depending on the national context.
As such, a sector positioned in the “low maturity” area may actually be well-developed in countries like Germany or the Netherlands, but still rated low at the EU level due to inconsistent implementation and preparedness across the bloc. The quadrant offers a strategic view of collective EU risk—not a one-size-fits-all diagnosis for national systems. While ENISA does not publish detailed scores per Member State or sector, national-level insights can sometimes be found in complementary reports. These include country-specific cybersecurity strategies, DESI (Digital Economy and Society Index) data, or voluntary contributions to EU-wide assessments. Such sources may provide a more granular picture of how individual countries are progressing within each sector.
The ENISA NIS360 Quadrant: A Strategic Risk Map
The ENISA NIS360 quadrant displays 21 critical sectors. The horizontal axis measures maturity—from ad hoc to systematically managed cybersecurity. The vertical axis measures criticality—the degree to which the sector underpins societal function.
Sectors in the top-left quadrant—high criticality, low maturity—represent the greatest strategic risk. These include:
- Space
- Maritime
- Health
- Gas
- ICT Service Management
- Public Administration
- Railway
These are not minor support functions. They operate satellites, run hospitals, distribute gas, and manage core digital infrastructure. Yet, ENISA finds that they are the least prepared to absorb or recover from serious cyber disruption.
Sectors in the bottom-left quadrant—lower maturity, moderate to high criticality—present a complex policy dilemma. Their placement suggests a lower degree of societal dependence than sectors like electricity or health, but this interpretation is increasingly contested.
Consider sectors such as:
- Oil
- Drinking Water
- District Heating and Cooling
- Waste Water
- Hydrogen
- Road
Each of these underpins daily life, from energy continuity to hygiene and mobility. In the face of prolonged disruptions, particularly during winter energy demand peaks, climate-induced water scarcity, or attacks on transportation networks—these sectors could become acute points of systemic vulnerability. Their quadrant position may reflect historical risk perception more than actual criticality. Revisiting their classification could support more proactive resilience planning.
Criticality Without Resilience
Let’s take a closer look at the sectors in the high-criticality, low-maturity and lower-maturity, critical quadrants:
- Space: While space infrastructure is increasingly integral to telecommunications, positioning, timing, and earth observation services, ENISA finds that the sector has not yet developed a mature cybersecurity framework. The fragmented ecosystem—spanning national, commercial, and intergovernmental actors—hinders collective preparedness and incident response.
- Maritime: As a backbone of EU trade, the maritime sector faces growing digital dependencies in port operations and navigation. ENISA points to challenges in harmonising cybersecurity efforts across diverse actors and jurisdictions, limiting coordinated responses.
- Health: Despite frequent targeting by cybercriminals and the high impact of disruptions, the healthcare sector remains fragmented in terms of governance and cybersecurity capacity. Legacy systems, regional disparities, and operational pressure limit the sector’s ability to invest in structural cyber resilience.
- Gas: A foundational energy source with cross-border infrastructure. ENISA identifies disparities in digital maturity among operators and concerns about legacy ICS vulnerabilities, which complicate risk mitigation.
- ICT Service Management: These providers support critical back-end functions for many other sectors. Their role is often underappreciated, and maturity levels vary widely, exposing cascading vulnerabilities in dependent sectors.
- Public Administration: Public entities at various levels—especially regional and local administrations, face high exposure but show varied levels of preparedness. Disparities in resources, digital maturity, and coordination mechanisms across EU Member States contribute to systemic vulnerability.
- Railway: Heavily relied upon for freight and passenger transport, the railway sector exhibits limited maturity in integrating cyber considerations into legacy signaling and control systems, especially across cross-border operations.
- Oil: Though part of the traditional energy backbone, many oil infrastructures rely on aging digital control systems and face high physical and cyber risk without sufficient harmonized cyber governance.
- Drinking Water: A critical utility with high societal impact yet often operated by local entities with limited cybersecurity resources and low baseline maturity.
- District Heating and Cooling: These regional utilities face integration challenges between operational technology and IT layers, leading to limited threat detection and recovery capabilities.
- Waste Water: Similar to drinking water, wastewater treatment systems tend to be under-resourced and overlooked, despite their importance in maintaining public health and environmental safety.
- Hydrogen: As a growing sector, hydrogen infrastructure lacks a harmonized cybersecurity baseline. New projects often proceed without embedded-by-design security principles.
- Road: Increasing digitalization through smart traffic systems and toll infrastructure is not yet matched by adequate cyber protection, particularly in distributed jurisdictions.
These sectors are not lagging due to inaction, but because of deeper structural constraints. ENISA points to challenges such as fragmented governance, limited coordination mechanisms, and inconsistent implementation of cybersecurity requirements across Member States. These issues hinder timely risk mitigation. Addressing them will require targeted policy interventions, improved capacity-building, and more cohesive alignment between operational needs and regulatory frameworks.
Blueprint for a Coordinated Fix
The quadrant must be read in conjunction with the revised EU Cybersecurity Blueprint, adopted on 6 June 2025. The Blueprint lays out a structured model for cyber crisis management—covering five stages: detection, analysis, escalation, response, and recovery. It aims to synchronize the actions of national authorities, EU bodies, and sectoral operators when cyber incidents threaten the internal market or societal stability.
However, the Blueprint presumes that each sector involved has already achieved a baseline level of operational cybersecurity maturity. For many of the sectors located on the left side of the ENISA NIS360 quadrant—particularly those with high criticality and low maturity—that assumption does not hold.
ENISA warns that this mismatch can significantly undermine the effectiveness of coordinated crisis management. Low maturity can delay detection and information-sharing, fragment situational awareness, and lead to breakdowns in escalation and coordinated response. If a high-criticality sector cannot mount an effective response or recovery effort, the consequences may exceed national containment capacities, demanding EU-wide intervention.
In these cases, the maturity gap is no longer just a performance issue. It becomes a structural vulnerability—one that can amplify the scale, duration, and cross-border consequences of cyber disruption.
This gap is particularly concerning in light of the ongoing implementation of the NIS2 Directive, which aims to raise cybersecurity standards across essential and important entities in the EU. While NIS2 expands scope and sets stricter obligations, ENISA’s findings suggest that many sectors still face delays in meeting these requirements. The implementation gap—between what the Directive mandates and what sectors have operationalised—compounds the risk landscape. When sectors fall short of NIS2 compliance, they enter crisis coordination unprepared, undermining the very goals the revised Blueprint seeks to achieve.
From Visibility to Action: What Leaders Must Do
For sector regulators, cybersecurity decision-makers, and EU-level policymakers, the quadrant is not just a visualization—it should be a strategic prompt, raising a fundamental challenge:
Is your sector in the top-left quadrant—and if so, what’s your plan?
The ENISA NIS360 quadrant isn’t just a scorecard. It’s a prioritization tool.
Here are four strategic responses leaders should take:
- Reprioritize investment: Funding and regulatory attention often go to the most digitized or visible sectors—but these are not always the most vulnerable. Use the quadrant to direct resources toward high-criticality, low-maturity sectors where marginal improvements yield systemic benefits.
- Tailor Blueprint exercises: Cyber Blueprint Exercises (CBX) should focus on testing coordination and response in the sectors identified as high risk. Sectors with less maturity—and more critical dependencies—must be brought into simulated crisis environments to stress-test coordination.
- Address coordination gaps: For sectors like space, maritime, and public administration, crisis ownership is not always clearly defined. Establishing shared escalation protocols, communication flows, and jurisdictional clarity will make crisis response more cohesive.
- Benchmark and revisit: The quadrant isn’t static. It should be treated as a living tool for reviewing cybersecurity posture, sector readiness, and policy alignment. Risk evolves—so must our defensive posture.
Appendix: Definitions of the 21 Critical Sectors in the ENISA NIS360 Quadrant
- Banking – Institutions that provide financial services including savings, loans, and payment systems. Highly digitized and tightly regulated.
- Core Internet – Infrastructure providers ensuring global Internet routing and DNS functionality. Fundamental to all digital operations.
- Datacenters and Cloud – Providers hosting and managing digital assets, storage, and services across private and public clouds.
- District Heating and Cooling – Urban heating and cooling systems relying on a networked distribution of thermal energy.
- Drinking Water – Systems responsible for water sourcing, treatment, and distribution to households and industry.
- Electricity – Production, transmission, and distribution of electrical power, covering both conventional and renewable sources.
- FMIS (Financial Market Infrastructure Services) – Platforms enabling transactions, clearing, and settlement in financial markets (e.g. stock exchanges, central counterparties).
- Gas – Extraction, processing, and distribution of natural gas and related infrastructure, often cross-border and high-pressure.
- Health – Healthcare delivery, hospital operations, medical devices, and e-health platforms handling sensitive personal data.
- Hydrogen – Emerging energy sector focused on hydrogen production, storage, and transport, increasingly linked to decarbonization goals.
- ICT Service Management – Providers delivering software, hardware, and digital support functions essential to enterprise IT environments.
- Maritime – Ports, shipping operators, and related logistics systems responsible for global goods movement and sea transport safety.
- Oil – Upstream (exploration, production) and downstream (refining, distribution) petroleum industry infrastructure.
- Aviation – Airports, airlines, air traffic control, and reservation systems supporting both cargo and passenger movement.
- Public Administration – Government institutions and municipal bodies providing services and governance at all levels.
- Railway – Railway infrastructure managers and train operators ensuring the movement of people and freight.
- Road – Infrastructure for road transport including tunnels, bridges, toll systems, and traffic management platforms.
- Space – Satellite operators, ground stations, and commercial launch services increasingly linked to navigation, weather, and telecom.
- Telecoms – Providers of mobile, fixed-line, and broadband communication services, including 5G core and access networks.
- Trust Services – Qualified digital identity and authentication providers (e.g. eIDAS services, digital signatures, timestamping).
- Waste Water – Systems for collecting, treating, and discharging sewage and industrial waste in compliance with health and environmental standards.

Sinclair Koelemij
With over 45 years of experience in process automation, Sinclair has developed extensive expertise spanning process automation, networking, security, and risk management for process automation systems. During a 43-year tenure at Honeywell, he contributed to service, engineering, and securing a wide range of control and process safety solutions, from basic to advanced systems, across the wider process industry, including petrochemical, refining, pipeline, and offshore operations. His experience includes software development and the implementation of control and safety systems for more than 100 installations, ranging from smaller setups with fewer than 1,000 I/O points to large-scale systems exceeding 100,000 I/O points.
Sinclair’s approach to OT security and cyber-physical risk is grounded in a deep understanding of production processes. He emphasizes addressing risks from the perspective of the process itself, ensuring that security measures align with the operational and safety requirements of industrial systems. His career includes 25 years focused on process automation and 20 years specializing in networking, cybersecurity, and risk management.
Sinclair also holds multiple patents in the field of cyber-physical risk evaluation and mitigation, reflecting his expertise in integrating technology and safety to protect industrial environments.



