Staying ahead of cyber threats means constantly evolving defenses and stopping new and often unpredictable threats. From its founding, SentinelOne has embraced AI as a means of detecting and autonomously responding to novel malware and TTPs, revolutionizing and setting the standard for modern endpoint protection in the process.
It’s not just central to our philosophy, it’s a core architectural tenet. It is how we give customers the advantage of speed and innovation when defending themselves against sophisticated nation state actors, constantly evolving ransomware variants, and the rise of a cybercriminal underground that keeps lowering the barrier to entry for the financially or politically motivated. Simply put, it’s how we stop modern attacks before they happen.
With the introduction of our new Framework for Optimized Rule Generation and Evaluation, or FORGE, SentinelOne is building on that foundation by using the power of agentic AI and large language models (LLMs) to completely reimagine and accelerate how teams create new, adaptive detection rules to stop ever-evolving threats.
The “AlphaEvolve Moment” Within the Cyber Space
Recently, Google DeepMind revealed AlphaEvolve, a powerful AI agent that evolves and optimizes algorithms for computing challenges. While AlphaEvolve explores the future of evolving algorithms in computing, SentinelOne’s FORGE1 offers a highly analogous approach in cybersecurity – an operationalized system for enhancing threat detection for real-world enterprise environments. Like AlphaEvolve, FORGE combines the creative problem-solving power of AI and LLMs with a rigorous evaluation process, enabling it to quickly generate highly effective, precise, and adaptive detection rules.
Traditional detection engines and AI-based models offer comprehensive coverage and are effective at identifying common attack patterns, forming a solid foundation for threat detection. However, updating and deploying models can be slow and complex, while attackers continually evolve their methods in real-time. Detection rules enable teams to close emerging detection gaps in a timely way, as well as fine-tune coverage.
The downside is that writing and maintaining these rules is slow, even for experts, requiring repeated testing to avoid false positives or blind spots. FORGE addresses this challenge by automatically generating high-quality rule candidates, significantly reducing manual effort and strengthening the detection stack.
Unlike traditional approaches, where rules can quickly become outdated in the face of sophisticated evasion techniques, FORGE utilizes diversified AI prompts to dynamically generate multiple rule candidates, which then undergo a rigorous, multi-tiered evaluation, ensuring that only the highest-quality rules are advanced to deployment.
Much like AlphaEvolve’s iterative approach, which uses automated evaluation to refine algorithms systematically, FORGE continuously learns and improves detection logic. When a rule does not meet the stringent precision and recall criteria, feedback is automatically integrated to guide AI-driven revisions. The result is an iterative refinement loop where detection logic rapidly adapts to emerging threats to minimize false positives and maximize coverage.
Example: Using Native OS Capabilities to Execute Malicious Code
Let’s take a look at an example where FORGE aids in our detection capabilities.
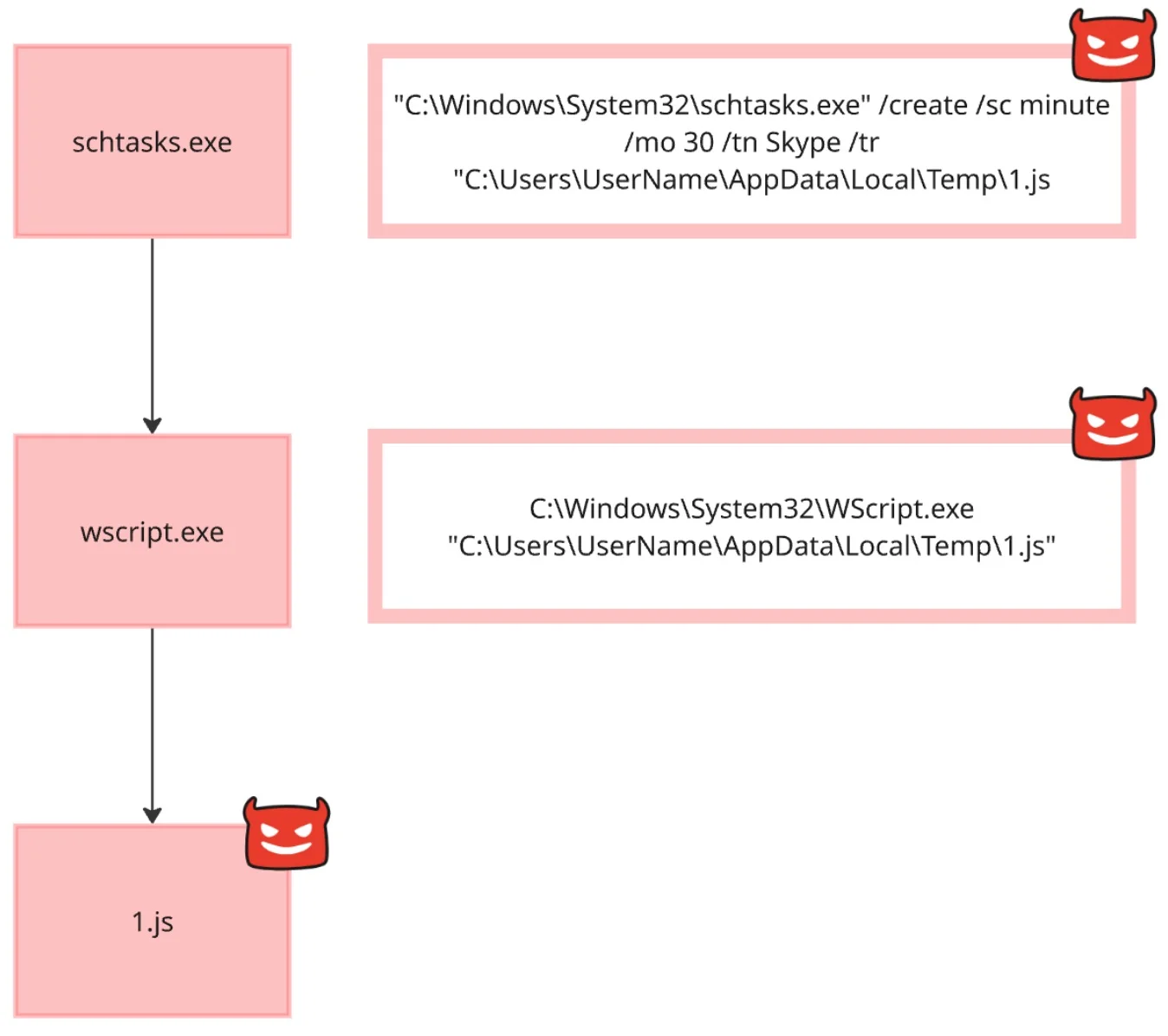
Figure 1 below represents a very typical example of how malware can maintain persistence on a Windows machine using built-in tools. The workflow is broken down into the following:
- The attacker uses the Scheduled Tasks executable (
schtasks.exe) to create a new task named “Skype” that runs every 30 minutes. - This task is configured to execute a JavaScript file called
1.jslocated in the user’s temporary files folder. - When the task runs, it launches
wscript.exe, which is the Windows Script Host used to execute.jsfiles. - As a result, this
1.jsscript is executed repeatedly on the system.

This technique is dangerous because it leverages entirely legitimate Windows components, making it difficult to detect and mitigate. By naming the task something inconspicuous such as “Skype” and placing the script in a temporary directory, the attacker avoids drawing attention. Malware authors often employ this method to ensure their code continues to run even after the system reboots or the user logs out.
We can tackle this problem with FORGE as it can easily create a detection rule to differentiate between malicious and non-malicious tasks.
How FORGE Helps Detect Malicious Activities
In Figure 2 below, we can see how FORGE generates and refines a detection rule for identifying malicious use of Windows Scheduled Tasks to execute JavaScript malware.
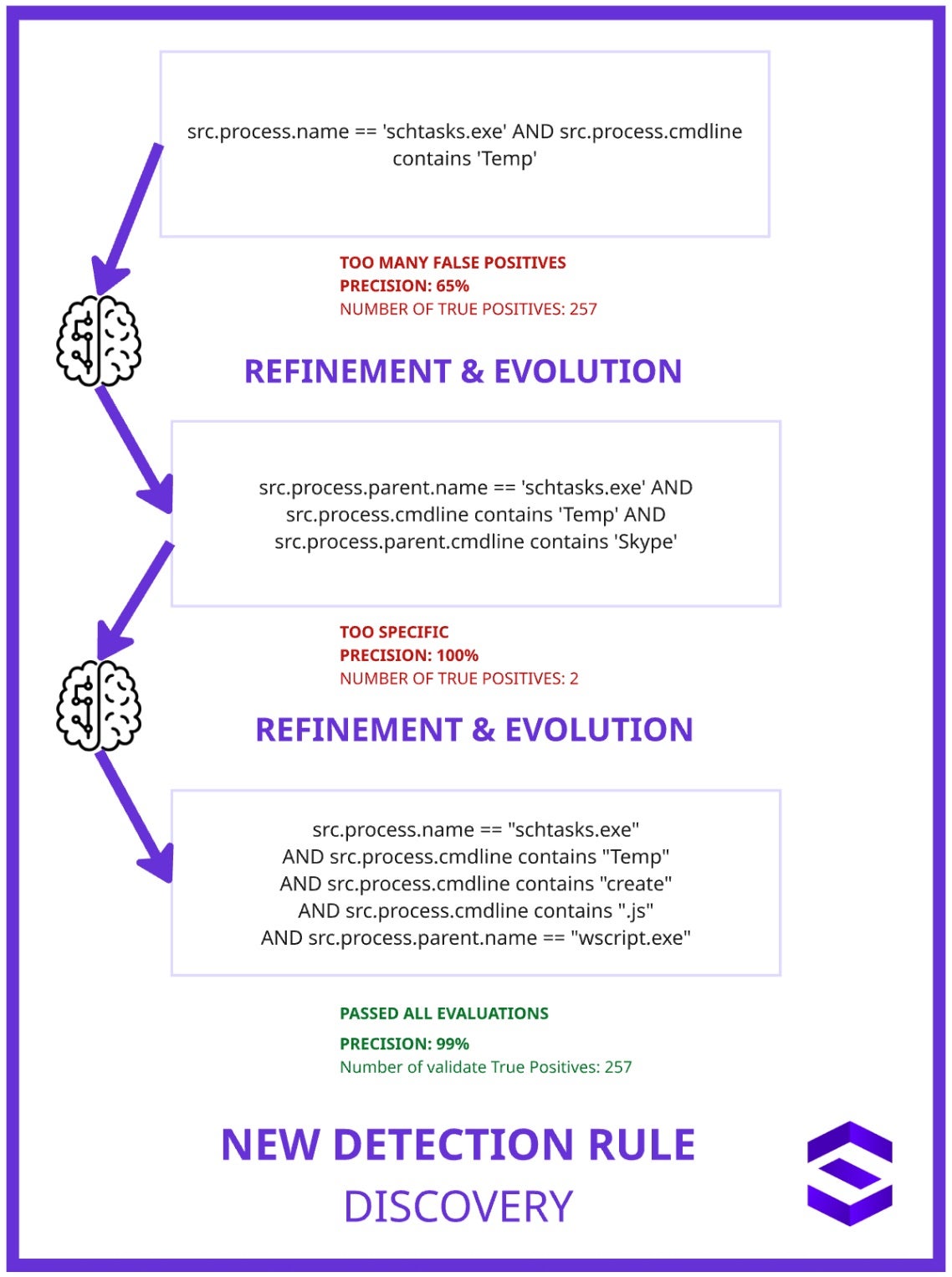
First, a broad rule flags any use of schtasks.exe with a command line referencing the Temp folder. While it captures many true positives in this example (257), the broad rule yielded a low precision rate of 65%, meaning it generated many false alarms.
Here, we iterate with the next generation of the rule created by FORGE. FORGE allows us to reduce noise by adding a condition that the parent command line must include “Skype”. However, this made the rule too narrow and it only caught 2 cases, though with perfect precision.
Finally, a more balanced and effective rule is created. FORGE checks for the creation of a scheduled task (create) that targets a JavaScript file (.js) in the Temp folder,and requires that the parent process be wscript.exe.
This rule now yields a high precision (99%) and successfully captures all 257 true positives, striking the right balance between generality and specificity.
This example illustrates how detection logic evolves through iterative tuning to enhance accuracy and minimize false positives in threat detection systems. It is important to note that FORGE does not replace our analysts. Rather, it eliminates the repetitive elements of rule generation and tuning, allowing analysts to concentrate on in-depth threat analysis and proactive defense strategies.
FORGE sets a new standard for AI-driven cybersecurity, enabling us to be agile, precise, and remain steps ahead of attackers.
1 Patent Pending
Third-Party Trademark Disclaimer
All third-party product names, logos, and brands mentioned in this publication are the property of their respective owners and are for identification purposes only. Use of these names, logos, and brands does not imply affiliation, endorsement, sponsorship, or association with the third-party.