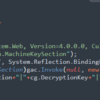
Microsoft’s SharePoint collaboration tools have faced widespread attacks over the last few days, impacting U.S. federal and state agencies, universities, energy companies, and an Asian telecommunications company, state officials and researchers told the Washington Post.
Microsoft said Sunday evening it’s still mitigating “active attacks” affecting on-premises SharePoint servers. It said attackers are “exploiting vulnerabilities partially addressed by the July Security Update.” The hackers’ identities are still unknown, the outlet reported.
Experts are referring to this latest hack on Microsoft’s collaboration tools as a “zero-day” attack because it “targeted a previously unknown vulnerability,” impacting tens of thousands of servers, the Post reported.
Microsoft released security updates that it said “fully protect” customers using SharePoint Subscription Edition and SharePoint 2019. There is no update for its SharePoint Server 2016 yet. The company said SharePoint Online in Microsoft 365 wasn’t impacted by the hack.
The FBI said in a statement in regards to the hack, “We are working closely with our federal government and private sector partners,” the Post reported.
This attack comes just days after ProPublica released an investigation where it discovered Microsoft is using Chinese engineers “to help maintain the Defense Department’s computer systems” with “minimal supervision” from U.S. workers with security clearances, making it vulnerable to cyberattacks — like this one.
While cyberattacks aren’t unique to Microsoft, the company sure faces a lot of them. After multiple attacks over the years from international hackers with ties to foreign governments, the U.S. Cyber Safety Review Board released a scathing report last year that said a “cascade of security failures” was to blame for the company’s series of cyberattacks, including an attack last January. It also found that Microsoft could have stopped Chinese state actors from hacking government emails in 2023.
—Laura Bratton and Britney Nguyen contributed to this article.