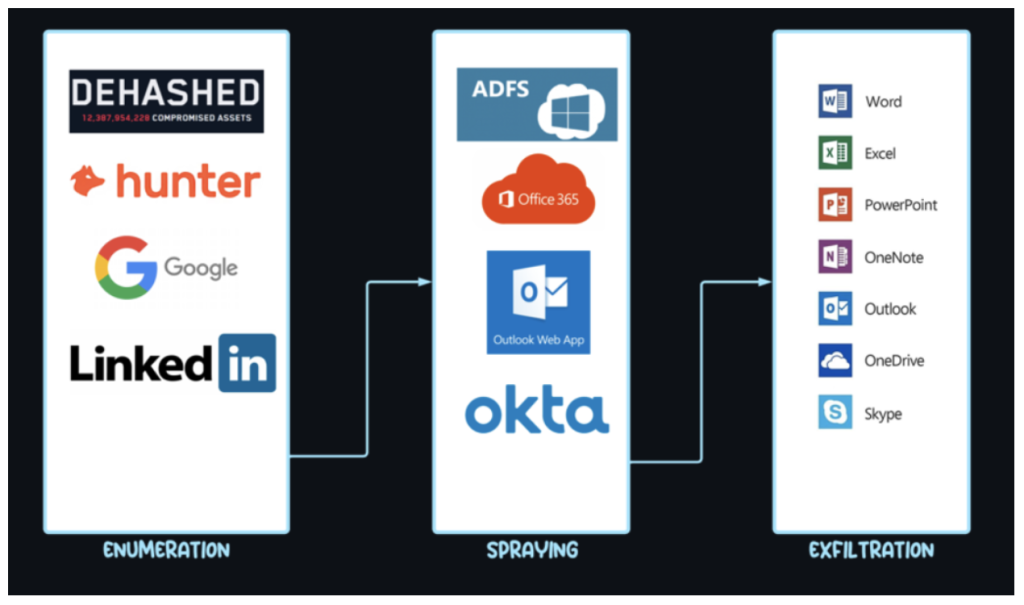
Proofpoint Threat Intelligence has uncovered a large-scale Account Takeover (ATO) campaign, internally tracked as UNK_SneakyStrike, that leverages the open-source penetration testing framework TeamFiltration to target Microsoft Entra ID user accounts across global organizations.
The campaign, which began in late 2024, has targeted over 80,000 user accounts across hundreds of cloud tenants to date, with several confirmed cases of successful credential compromise and unauthorized access.
This marks a significant escalation in the use of legitimate security tools for malicious purposes a trend that is likely to increase as attackers evolve their methods.
Technical Overview: TeamFiltration and Its Weaponization
TeamFiltration a tool originally designed for penetration testing in cloud environments, was created by security researchers to automate tactics, techniques, and procedures (TTPs) commonly observed in modern ATO attacks.
Publicly released at DefCon30 in August 2021, TeamFiltration empowers both red teams and threat actors to efficiently identify vulnerable accounts and exfiltrate sensitive data.
- Account Enumeration:
- Uses the Microsoft Teams API to check if a user account exists within a targeted Entra ID (Azure AD) environment.
- Recently added an optional OneDrive-based enumeration method, offering more stealth and flexibility.
- Password Spraying:
- Attempts to log in using a list of common or systematically varied passwords.
- Operates across multiple AWS regions for IP rotation, making detection more difficult.
- Data Exfiltration:
- Extracts emails, files, and other valuable data from cloud storage.
- Persistence and Backdooring:
- Uploads malicious files to a victim’s OneDrive, replacing existing files (e.g., on the desktop) with lookalike documents.
- These files may contain macros or malware to establish persistence or further compromise systems.

pythonimport os
import shutil
import requests# Simulated code: replace a user's file with lookalike after upload to OneDrive
desktop_file = "C:/Users/User/Desktop/important_document.docx"
backdoor_file = "C:/temp/backdoor_doc.docx"
onedrive_url = "https://graph.microsoft.com/v1.0/me/drive/root/children"
# Copy backdoor file locally (if needed)
shutil.copy(desktop_file, desktop_file + ".bak")
os.rename(desktop_file, desktop_file + ".old")
os.rename(backdoor_file, desktop_file)
How Proofpoint Tracked UNK_SneakyStrike
According to the Report, Proofpoint’s threat researchers analyzed the publicly available TeamFiltration code and its default configuration file to identify unique signatures and behavioral patterns associated with the campaign.
- User Agent:
- Default TeamFiltration user agent:
text
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Teams/1.3.00.30866 Chrome/80.0.3987.165 Electron/8.5.1 Safari/537.36- This outdated Teams client agent is rarely seen in legitimate environments, serving as a strong initial detection signal.
- Application ID Targeting:
- TeamFiltration targets a specific list of Microsoft OAuth client applications to obtain “family refresh tokens” from Entra ID.These tokens can be exchanged for valid bearer tokens, which are then used for unauthorized access.
- AWS and Azure Infrastructure:
- Attackers use AWS servers to rotate IPs across different regions, complicating blocking efforts.
- TeamFiltration requires a “sacrificial” Microsoft 365 account with a valid license for enumeration.
UNK_SneakyStrike activity is marked by concentrated bursts of unauthorized access attempts, targeting all users in smaller tenants and a subset of users in larger ones. These are followed by quiet periods of four to five days.
Key Recommendations and Mitigation
Proofpoint’s findings underscore the dual-use nature of open-source security tools and the growing sophistication of threat actors in impersonating legitimate traffic and leveraging cloud infrastructure for anonymity.
- Monitor for unusual sign-ins from the listed IPs and user agents, especially from AWS regions.
- Review and audit OAuth applications and client IDs in Entra ID, particularly those referenced in pentesting tools.
- Implement multi-factor authentication (MFA) and limit the use of legacy authentication protocols.
- Stay updated on new TTPs and share threat intelligence within your organization and industry community.
Selected IoCs (from Proofpoint):
| Indicator | Type | Description |
|---|---|---|
| Mozilla/5.0 (Windows NT 10.0; Win64; x64)… | User Agent | Default TeamFiltration user agent |
| 44.220.31[.]157 | IP Address | Source IP, active since 04/01/2025 |
| 44.206.7[.]122 | IP Address | Source IP, active since 07/01/2025 |
| 3.255.18[.]223 | IP Address | Source IP, active since 28/02/2025 |
| 44.206.7[.]134 | IP Address | Source IP, active since 07/01/2025 |
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates




.png
)
