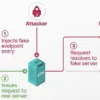
A new vulnerability in file archiving software WinRAR has come to light that can potentially install backdoor malware on Windows PCs. The zero-day vulnerability was discovered by security researchers at ESET and has been tracked as CVE-2025-8088 which is said to be actively exploited by the Russian-linked hacking group RomCom.
The vulnerability has been classified as a directory traversal flaw that allows malicious archives to place files in locations chosen by the attacker. By exploiting it, threat actors can place executable files into autorun directories like the Windows Startup folder at:
%APPDATA%MicrosoftWindowsStart MenuProgramsStartup (user-specific)
%ProgramData%MicrosoftWindowsStart MenuProgramsStartUp (system-wide)
This allows the placed malicious files to execute automatically the next time the system boots, giving attackers a pathway to remote code execution. Speaking to Bleeping Computer, Anton Cherepanov, Peter Košinár, and Peter Strýček from ESET said that they observed spearphishing emails with attachments containing RAR files to deliver RomCom backdoors.
RomCom, known by aliases such as Storm-0978, Tropical Scorpius, Void Rabisu, or UNC2596, is a cybercrime and cyber-espionage group linked to Russia. Emerging around mid-2022, RomCom primarily targeted entities in Ukraine including the government, military, energy, and water infrastructure. It has today broadened its scope to include organizations and audiences in the U.S., Europe, and internationally connected to Ukraine-related humanitarian efforts.
Flaw acknowledged and fixed – please manually update
The flaw has been acknowledged and fixed via a new WinRAR update with version 7.13. According to the release notes, extracting a file using previous versions of WinRAR, Windows versions of RAR, UnRAR, portable UnRAR source code and UnRAR.dll can be tricked into using a path, defined in a specially crafted archive, instead of user specified path.
Get Tom’s Hardware’s best news and in-depth reviews, straight to your inbox.
Since WinRAR does not include an auto-update feature, it is recommended to manually update the software. Notably, Unix versions of RAR, UnRAR, portable UnRAR source code, UnRAR library, and RAR for Android, are safe from this exploit.
A similar directory traversal flaw was spotted back in June, when independent security researcher “whs3-detonator” reported CVE-2025-6218 to Trend Micro’s Zero Day Initiative. This high-risk vulnerability in WinRAR stemmed from flawed handling of archive file paths, where attackers could craft malicious archives that bypass extraction boundaries and deposit files into unintended locations.
Follow Tom’s Hardware on Google News to get our up-to-date news, analysis, and reviews in your feeds. Make sure to click the Follow button.