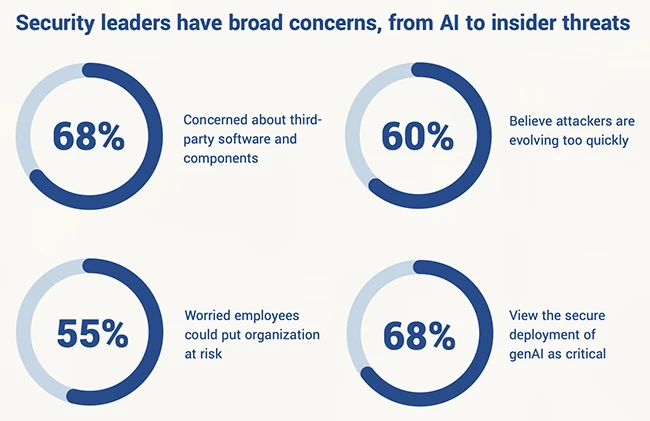
Security leaders are rethinking their approach to cybersecurity as digital supply chains expand and generative AI becomes embedded in critical systems. A recent survey of 225 security leaders conducted by Emerald Research found that 68% are concerned about the risks posed by third-party software and components. While most say they are meeting regulatory requirements, 60% admit attackers are evolving too fast to maintain resilience.

Survey of 225 C-suite or VP-level individuals (Source: Emerald Research)
The report highlights a growing tension between compliance and actual security. As one section states, “Security leaders are calling for stronger controls, faster remediation, and greater visibility into emerging AI risks.” Many now view cybersecurity as a strategic business issue rather than just a technical one.
Third-party tools remain the top concern, but generative AI is catching up. Nearly half of respondents say they are uneasy about AI-driven features and large language models. Boards are also taking note. Sixty-eight percent of security leaders say their board now sees the secure deployment of GenAI as a critical priority.
These worries are not hypothetical. Penetration tests of AI applications found that 32% had high-risk vulnerabilities. That is a higher rate of severe findings than in other categories of systems. The most common flaws were not unique to AI, but classic issues like SQL injection and stored cross-site scripting.
The complexity of software supply chains is also driving concern. Most organizations today rely on a mix of proprietary code, open-source components, and external services. Seventy-three percent of surveyed executives said they had received at least one notification of a supply chain vulnerability or incident in the past year. In response, 83% now face formal requirements to demonstrate vendor security, and more than half require pentesting and vulnerability reporting from suppliers.
These measures are also shaping customer relationships. “Seventy-four percent of security leaders believe regular, documented pentesting enhances credibility with clients and can offer a competitive edge in procurement.”
Penetration testing is no longer treated as a box to check. It has become a core element of enterprise security programs. Eighty-eight percent of security leaders now consider it vital. Over half say they use pentests to validate their own software. More than half also require third-party pentests before releasing software to customers.
The survey found that 49% plan to use pentesting to identify software supply chain vulnerabilities, and 44% intend to use it to uncover insider threats. The practice is being integrated across the development life cycle and procurement workflows.
Generative AI is emerging as a new and unpredictable risk. Sixty-six percent of respondents say GenAI helps attackers analyze data and evade defenses. More than half worry that AI can automate the entire attack lifecycle, and 62% are concerned that AI development tools may introduce hidden vulnerabilities into codebases.
Data protection sits at the center of these concerns. “Forty-four percent of leaders cite model poisoning and intellectual property theft as their most pressing GenAI-related risks.” Others cite training data leakage, unauthorized platform use, and bias in AI outputs. Despite the novelty of AI, the underlying issues still trace back to classic software security problems.
Security teams are calling for new tools and standards. Over half want dedicated tools to assess GenAI security before deployment. An equal number want guidance on how to use AI defensively. Forty-eight percent say they need frameworks to detect and respond to AI-generated attacks. As one section of the report states, “Without such guardrails, the promise of innovation may come at the expense of long-term security and brand reputation.”
CISOs are now being pushed toward a more offensive mindset. Many are embedding pentesting into vendor agreements and applying the same rigor to AI systems as to traditional infrastructure. One recommendation reads, “Make penetration testing a non-negotiable part of procurement and the entire software development life cycle.”




