Cybersecurity professionals constantly seek more effective penetration testing tools to stay ahead of threat actors and properly assess organizational defenses.
A recent innovation in this field comes from security researchers who have developed a specialized agent for the Mythic framework designed to overcome limitations in popular penetration testing platforms.
This development addresses critical challenges faced by ethical hackers who find their tools frequently detected by modern security solutions, reducing their effectiveness during assessment engagements.
The need for more sophisticated, harder-to-detect pentesting tools has grown as defensive technologies have improved at identifying known frameworks.
Popular tools like Cobalt Strike, with its specific opcode sequences, and Metasploit’s Meterpreter payload, which has over 230 signatures in Microsoft’s antivirus database, have become increasingly difficult to use without triggering security alerts.
Open-source alternatives like Sliver and Havoc frameworks show promise but suffer from significant drawbacks including oversized payloads, stability issues, and limited customization options.
Securelist researchers identified these limitations through extensive analysis and proposed a modular approach to penetration testing using the Mythic framework.
Their research demonstrated how existing tools quickly become obsolete as security vendors prioritize their detection, forcing pentesters to spend increasing amounts of time preparing for engagements rather than conducting the actual assessment work.
Payload Stages
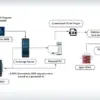
The proposed solution involves a three-stage payload structure that splits functionality between initial execution (Stage 0), reconnaissance and persistence (Stage 1), and advanced operations like privilege escalation and lateral movement (Stage 2).
This modular design allows components to be updated or modified independently, increasing the framework’s resilience against detection.
The researchers particularly focused on optimizing Stage 1, which establishes the critical foothold and communications pathway for subsequent operations.
For implementing Stage 1, the researchers selected Beacon Object Files (BOFs) designed for execution within the Mythic framework.
.webp)
This approach represents an evolution beyond traditional techniques like reflective DLL injection or .NET assembly execution, which have become relatively easy for security solutions to detect.
The BOF approach enables dynamic functionality through object file execution in memory, without creating new processes or injecting code-activities that frequently trigger security alerts.
The technical implementation centers around loading Common Object File Format (COFF) files directly into memory, executing them without writing to disk.
The process involves sophisticated symbol relocation where the agent reads the .text section of the object file and replaces zeros with relative addresses of external functions and static data:-
COFF object file
in memory
.text
0x07: 4C 8D 05 00 00 00 00
0x17: FF 15
Relocations
OxOA
Symbol 0x08
0x19
Symbol Ox0C
lea r8, [rip+0x0]
call QWORD PTR [rip+ ]While acknowledging limitations-such as the blocking nature of object file execution preventing multiple simultaneous tasks-the researchers emphasize that their approach yields a significantly smaller payload (approximately 50KB unencrypted when using C) compared to alternatives like Sliver’s 8-9MB payload.
.webp)
This smaller footprint combined with the ability to leverage various communication protocols, including covert channels over platforms like Slack or Telegram, provides pentesters with enhanced flexibility and improved evasion capabilities.
This research represents a valuable contribution to the field of ethical hacking, demonstrating how security professionals can balance leveraging existing open-source projects with custom development to create more effective and resilient assessment tools.
How SOC Teams Save Time and Effort with ANY.RUN - Live webinar for SOC teams and managers




.png
)
