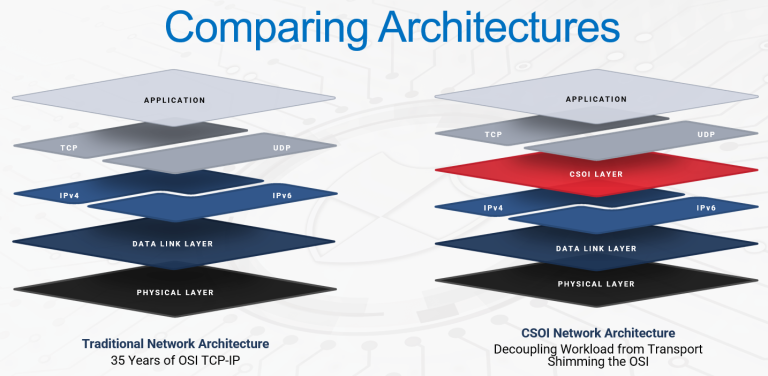

As cybersecurity threats grow more sophisticated, traditional network architectures struggle to keep pace, especially in sectors reliant on legacy hardware. IMPRES Technology Solutions has introduced its Cybersecurity Operations Infrastructure (CSOI) offering, a timely software solution that inserts an overlay between two key layers in the OSI framework to determine authentication and authorization of traffic prior to allowing any access.
At its core, CSOI introduces a software-defined networking (SDN)-based layer between the transport and network layers of the OSI stack. CSOI calls this the “3.5 layer” out of the seven layers of the OSI framework. This novel positioning lets the software intercept traffic before it’s passed through the stack, and asks a crucial question: “Do you come with valid identity and authorization?”
Decoupling Identity from Location
CSOI’s innovation leverages principles like the host identity protocol (HIP), which works to separate an endpoint’s identity from its IP address, an approach that has become central to zero-trust architecture solutions.
Steven Lemons, principal solutions architect, shared that CSOI “inserts a software shim” to let systems evaluate key criteria, namely who a device is, not just where it is. “We call it a shim because it levels up the network stack to separate identity from location,” Lemons said.
This is especially critical for those networks operating on legacy devices that cannot accept software updates or be easily replaced. These devices represent significant vulnerabilities in environments that are part of the nation’s critical infrastructure.
How CSOI Works
CSOI is anchored by the Conductor, a cloud-based control dashboard that manages the identities of approved devices as well as the policies of authorization allowing approved access, Lemons explained. Once installed, the Conductor assigns each device a unique, cryptographically secure identity. The network can ignore devices without this ID; those with IDs must meet strict policy-based access controls to communicate.
“We call it the Conductor because it’s like the conductor in front of an orchestra who directs every musician,” he said. “The software layer we call the ‘red diamond’—that’s how it’s illustrated in diagrams showing its position in the OSI stack.”
The result is a deny-by-default security model that inherently resists man-in-the-middle and distributed denial of service (DDoS) attacks. Traffic that doesn’t meet both identity and policy of trust requirements simply doesn’t get through, Lemons said.
Zero Trust, Made Practical
With the growing need for zero-trust strategies, CSOI offers a realistic path forward without requiring a full network overhaul. Its overlay design means organizations can deploy it on top of their existing infrastructure, supporting current devices (whether physical or virtual) and any that may be added in the future, he offered.
CSOI also strengthens cloud deployments. Through virtual private clouds and policy segments, it can extend its identity-based protections across public cloud environments, using its API-ready architecture and mobile compatibility to manage trust at scale.
Operational and Cost Advantages
In addition to heightened security, CSOI can help organizations optimize their IT budgets. By reducing reliance on traditional firewalls, VPNs and outdated maintenance contracts, some hardware refreshes may become unnecessary. Over time, organizations can simplify operations and reduce costs while gaining stronger security postures.
The Bottom Line
CSOI represents a forward-thinking shift in network security architecture. By introducing an identity-aware layer into the OSI model, it lets organizations, especially those reliant on legacy systems, adopt zero-trust principles without starting from scratch.
For more information and a demonstration of CSOI’s capabilities, visit CSOI.US



