
The government in Switzerland is informing that sensitive information from various federal offices has been impacted by a ransomware attack at the third-party organization Radix.
The hackers have stolen data from Radix systems and later leaked it on the dark web, the Swiss government says.
The exposed data is being analyzed with the help of the country’s National Cyber Security Centre (NCSC) to determine which government agencies are impacted and to what effect.
“The foundation Radix has been targeted by a ransomware attack, during which data was stolen and encrypted,” announced the Swiss government.
“Radix’s customers include various federal offices. The data has been published on the dark web and will now be analyzed by the relevant offices.”
Sarcoma ransomware attack
Radix is a Zurich-based non-profit organization dedicated to health promotion. It operates eight competence centers that carry out projects and services commissioned by the Swiss federal government, cantonal and municipal authorities, and other public and private organizations.
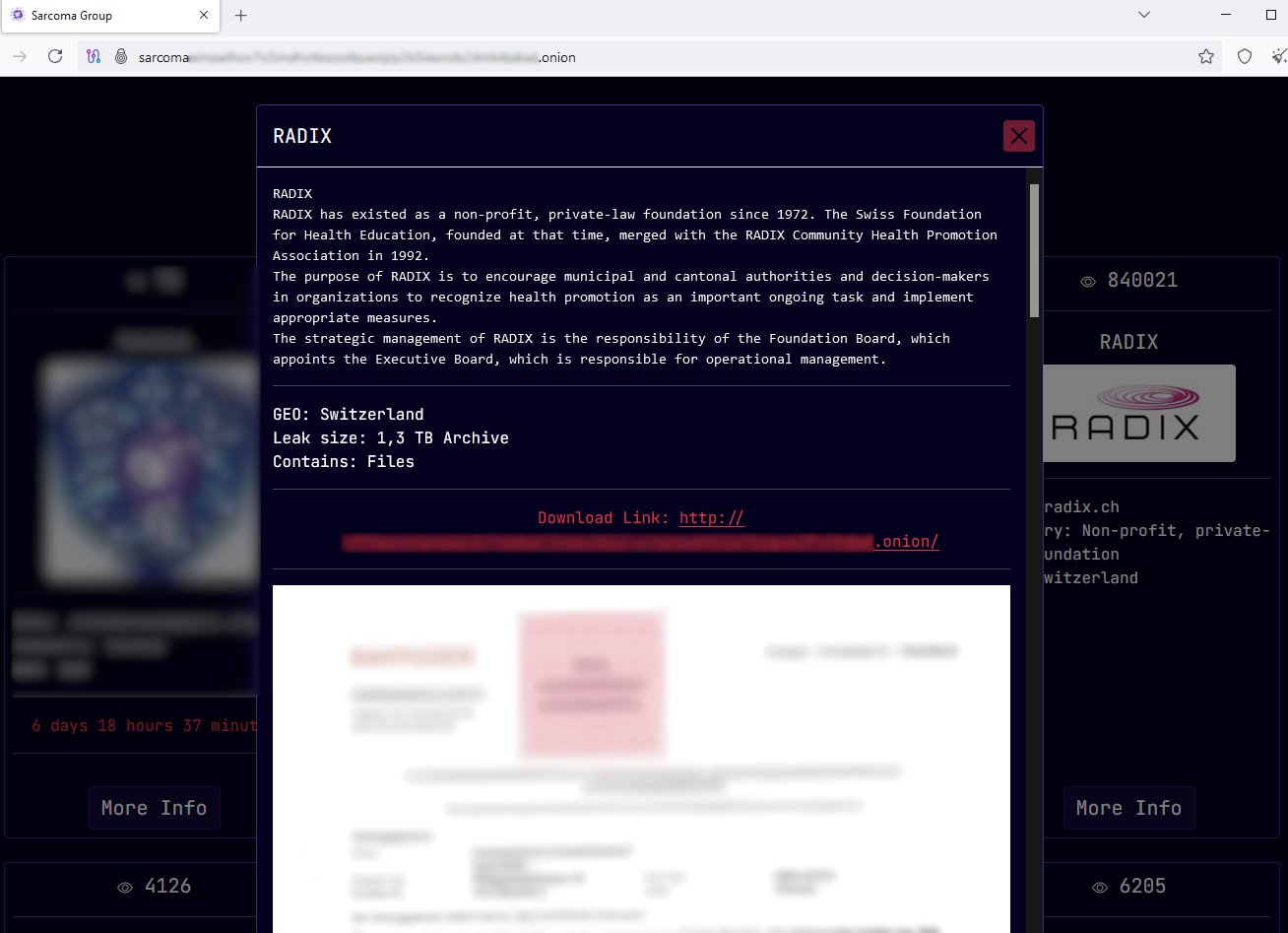
The organization issued a statement saying that Sarcoma ransomware affiliates compromised its systems on June 16.
Sarcoma is a rapidly emerging ransomware group that began operations in October 2024, quickly becoming one of the most active by claiming 36 victims in its first month. One notable case was an attack against PCB giant Unimicron.
Sarcoma gains access through phishing, older vulnerabilities, and supply-chain attacks. Then the hackers typically rake advantage of RDP connections and move laterally on the network. In the last stage of the attack, the threat actor steals data and may also encrypt it.
The threat actor published the data stolen from Radix on their leak portal on the dark web on June 29, likely after extortion efforts failed.
Source: BleepingComputer
Radix says it informed impacted individuals via personalized notifications and notes that there is no evidence that sensitive data from partner organizations was affected.
Meanwhile, Sarcoma appears to have published a 1.3TB archive on its extortion portal, including several document scans, financial records, contracts, and communications. The data is being offered for free.
To mitigate this risk, Radix suggests that potentially exposed individuals remain vigilant over the coming months and be wary of attempts to get their passwords, credit card numbers, and account credentials.
BleepingComputer has contacted NCSC to request more information about the data unearthed by the ongoing investigations, but a comment wasn’t immediately available.
In March 2024, the Swiss government confirmed it had suffered a similar exposure via third-party software services provider Xplain, which was breached by the Play ransomware group on May 23, 2023.
That incident resulted in the leak of 65,000 documents relating to the Federal Administration, many of which contained sensitive personal information.



