Key Takeaways:
- A massive ATO campaign is exploiting a legitimate pentesting tool to breach Microsoft Entra ID accounts.
- Over 80,000 user accounts across global organizations have been targeted using stealthy, cloud-based tactics.
- Attackers are bypassing security controls and automating data theft through advanced token abuse.
Cybersecurity researchers have discovered a widespread account takeover (ATO) campaign that weaponizes the TeamFiltration penetration testing framework to infiltrate Microsoft Entra ID (formerly Azure Active Directory) accounts. The attackers have already targeted over 80,000 user accounts across hundreds of organizations worldwide.
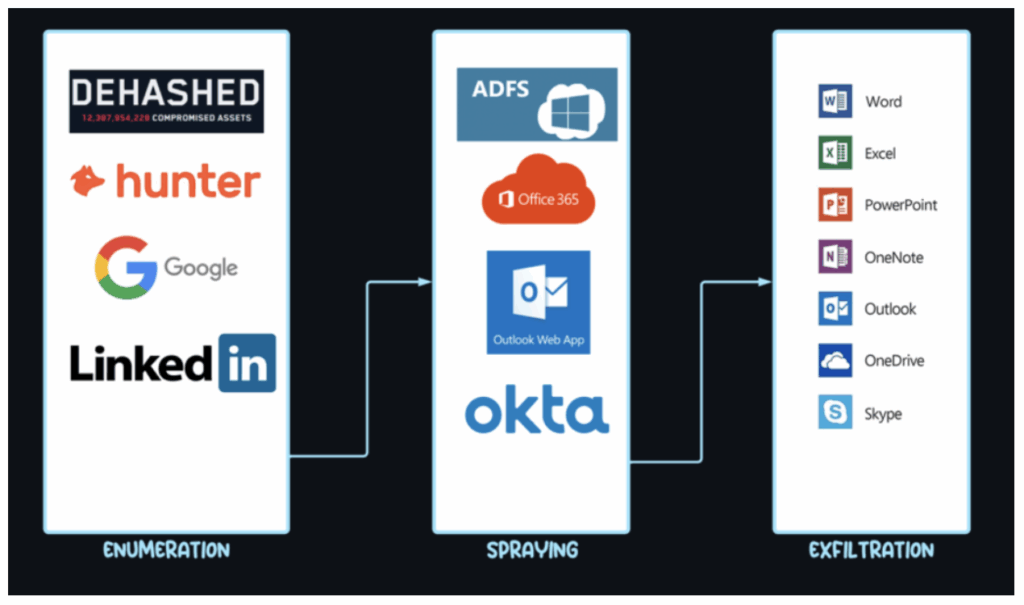
TeamFiltration is a cross-platform penetration testing tool designed to simulate post-exploitation activities in Office 365 and Entra ID environments. It allows security professionals to perform various tasks like user enumeration, password spraying, data exfiltration from services (like Outlook, Teams, and OneDrive), and even persistent access through account backdooring. This tool is particularly useful for red team operations and cloud security assessments.
How hackers exploit Microsoft Entra ID using TeamFiltration
According to a new report from Proofpoint, the active account takeover (ATO) campaign (codenamed UNK_SneakyStrike) was first observed in December 2024. The attackers used a combination of Microsoft Teams API and AWS servers scattered across 100 cloud tenants to conduct enumeration and password-spraying attacks.
“These attempts systematically rotate AWS Regions, ensuring each password spraying wave originates from a different server in a new geographic location,” Proofpoint researchers explained.
Once TeamFiltration successfully obtains credentials for a user account, it then tries to bypass or exploit weaknesses in the organization’s Conditional Access Policies (CAPs). TeamFiltration can exploit a feature in Microsoft’s OAuth system called “family refresh tokens” (FRTs), which allow access tokens to be generated for multiple related applications. If an attacker gains access to one app using an FRT, they can potentially access other apps in the same token family without needing to reauthenticate.
Lastly, TeamFiltration automates the extraction of data from compromised accounts. For instance, if it gains access to a Teams account, it will automatically collect chat histories, shared files, and contact lists without manual input.
Proofpoint says that the attacks peaked in January 2025. The majority of the suspicious or malicious login attempts were traced back to servers hosted on Amazon Web Services (AWS), with 42% coming from the U.S., 11% from Ireland, and 8% from the UK.

How organizations can defend against TeamFiltration account takeover campaigns
To defend against TeamFiltration-based account takeover campaigns, Proofpoint recommends a multi-layered security approach. Organizations should enforce strong multi-factor authentication (MFA) across all user accounts, especially for those with administrative privileges. This helps prevent unauthorized access even if credentials are compromised. It’s also important to monitor for signs of account enumeration and password spraying, particularly from cloud infrastructure like AWS, which attackers often use to mask their origin.
Additionally, organizations should review and tighten their conditional access policies to ensure they don’t leave exploitable gaps. Limiting the scope and lifespan of OAuth tokens, especially Family Refresh Tokens (FRTs), can reduce the risk of attackers using one compromised app to access others. Finally, educating users about phishing and suspicious login activity can help detect and stop attacks early in the chain.